Understanding GitHub Scan ScopeProwler can scan either:
- User Repositories: All repositories owned by or accessible to a specific GitHub user
- Organizations: Repositories and organization-level settings
Prowler Cloud/App
Web-based interface with centralized management
Prowler CLI
Command-line interface for local or automated scans
Prowler Cloud/App
Walkthrough video onboarding a GitHub Account using GitHub App.
Prerequisites
Before adding GitHub to Prowler Cloud/App, ensure you have:-
GitHub Account Access
- Personal GitHub account, OR
- Admin access to a GitHub organization
-
Authentication Credentials
- Choose one method (see Authentication Guide):
- Fine-Grained Personal Access Token (Recommended)
- OAuth App Token
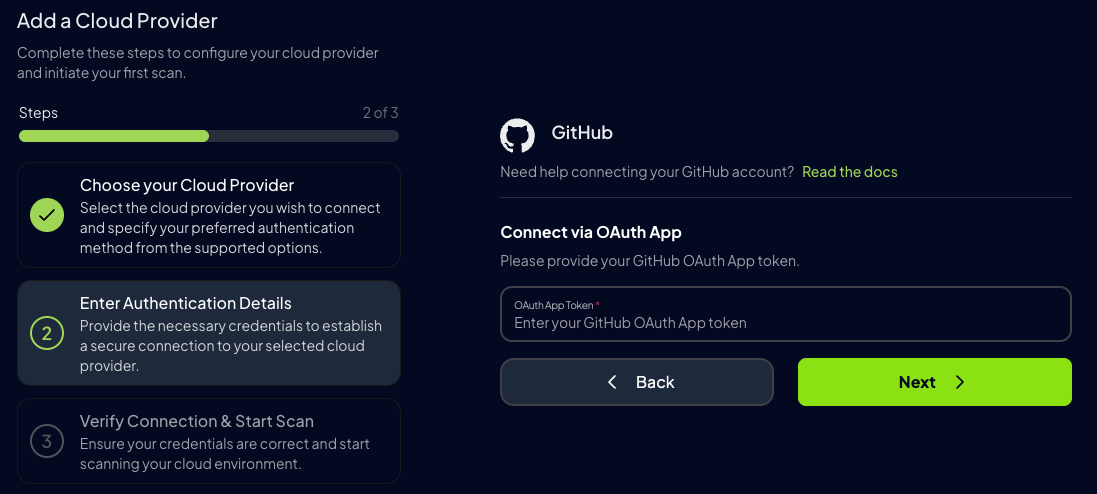
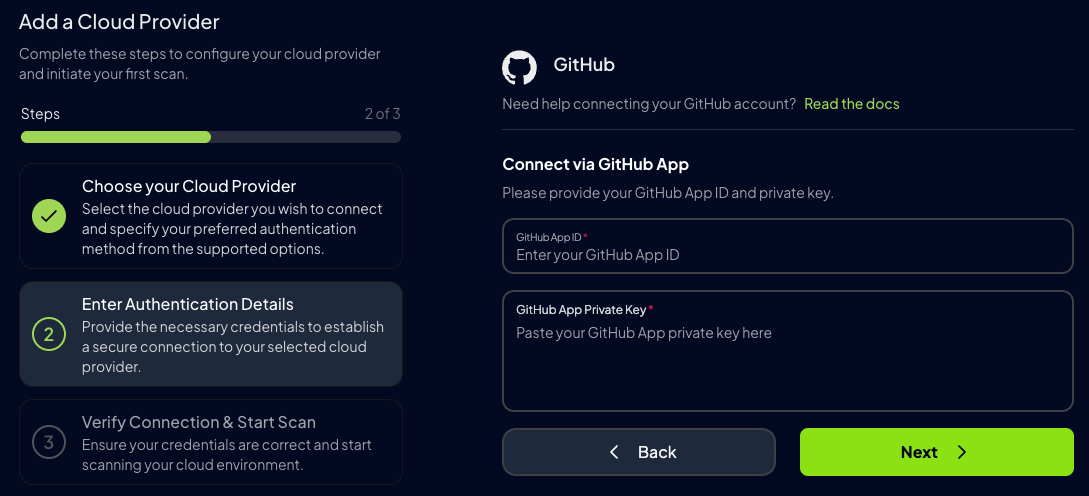
- GitHub App Credentials (Not Recommended - limited data access)
- Choose one method (see Authentication Guide):
Step 1: Access Prowler Cloud/App
- Navigate to Prowler Cloud or launch Prowler App
-
Go to Configuration → Cloud Providers
-
Click Add Cloud Provider
-
Select GitHub
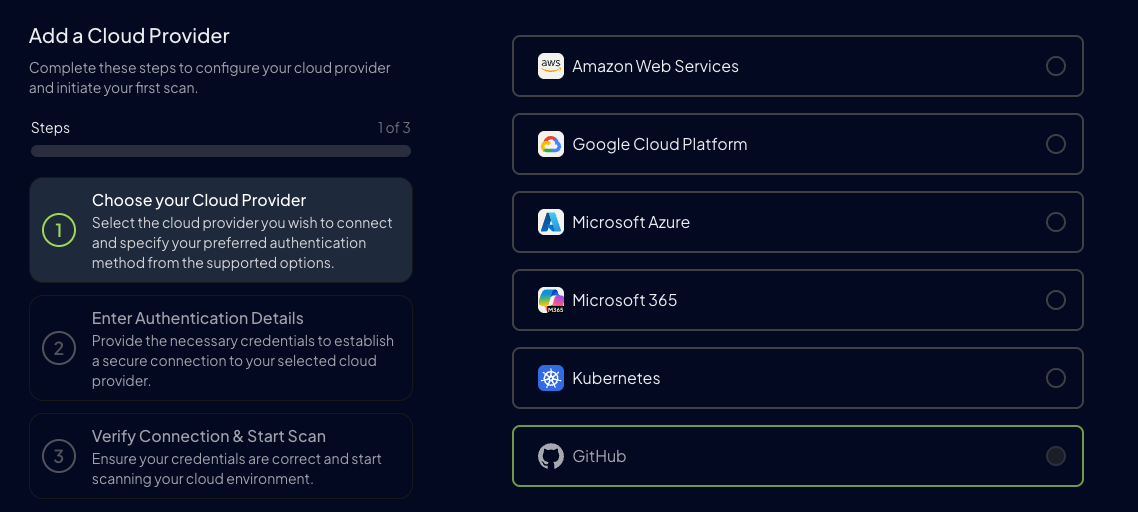
Step 2: Configure GitHub Account
-
Add the GitHub Account ID and an optional alias:
- Account ID: Your GitHub username (e.g.,
username) or organization name (e.g.,org-name) - Alias (optional): Friendly name for this connection (e.g.,
My Personal ReposorProwler Org)
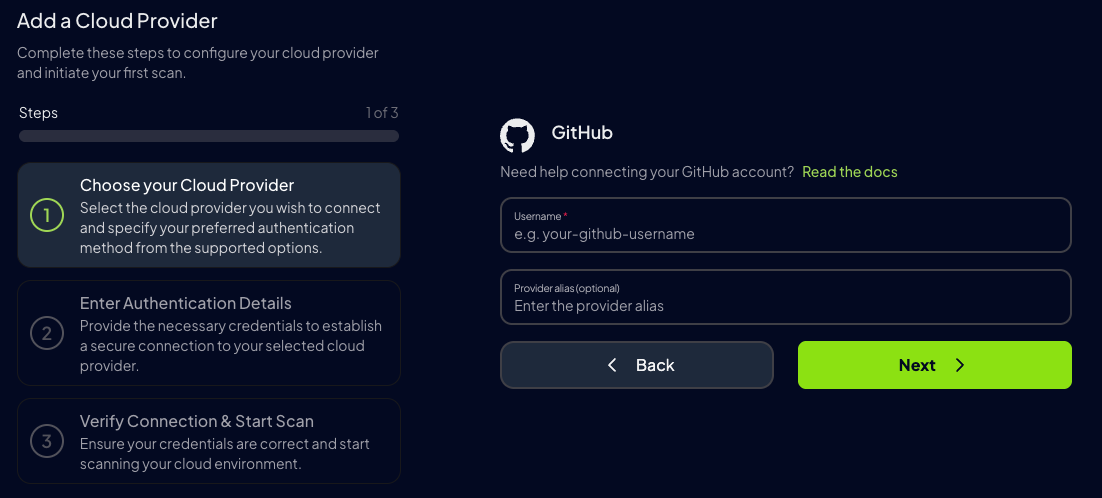
- Account ID: Your GitHub username (e.g.,
- Click Next
Step 3: Choose Authentication Method
Recommended: Fine-Grained Personal Access TokenFine-Grained Personal Access Tokens are strongly recommended because they provide:
- Best data access for comprehensive security scanning
- Granular permission control
- Resource-specific access
-
Select your preferred authentication method:
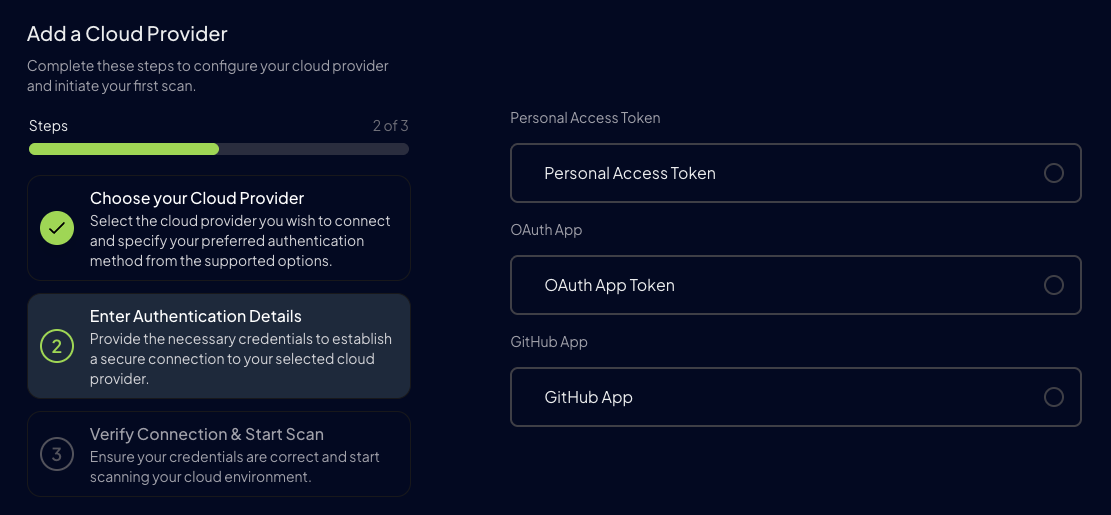
- Personal Access Token (Recommended)
- OAuth App Token
- GitHub App (Not Recommended)
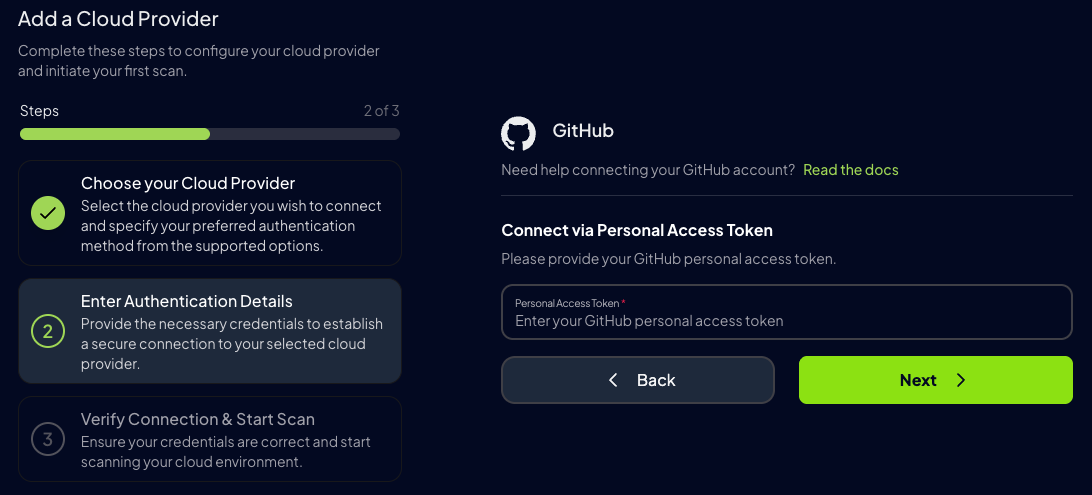
- Enter your Fine-Grained Personal Access Token
- Click Verify to test the connection
- Click Save
- Click Start Scan to begin your first security assessment
Step 5: View Results
Once the scan completes, you can:- View security findings in the dashboard
- Export results in multiple formats (JSON, CSV, HTML)
- Set up continuous scanning schedules
- Configure alerts for critical findings
Prowler CLI
Prerequisites
Before running Prowler CLI for GitHub, ensure you have:-
Prowler Installed
-
Authentication Credentials
- Choose one method (see Authentication Guide):
- Fine-Grained Personal Access Token (Recommended)
- OAuth App Token
- GitHub App Credentials (Not Recommended)
- Choose one method (see Authentication Guide):
Authentication Setup
Prowler CLI automatically detects authentication credentials using environment variables in this order:GITHUB_PERSONAL_ACCESS_TOKENGITHUB_OAUTH_APP_TOKENGITHUB_APP_IDandGITHUB_APP_KEY
- Environment Variables (Recommended)
- CLI Flags
Scan Scope: Understanding What Gets Scanned
Scanning User Repositories
Scan repositories owned by your user account:- Repository security settings
- Branch protection rules
- Secret scanning configuration
- Dependabot settings
- Organization-level policies (not included)
Scanning Organizations
Scan organization repositories and organization-level security settings:- All organization repositories
- Repository security settings
- Organization MFA requirements
- Organization security policies
- Member access and permissions
Scan Scoping
Scan scoping controls which repositories and organizations Prowler includes in a security assessment. By default, Prowler scans all repositories accessible to the authenticated user or organization. To limit the scan to specific repositories or organizations, use the following flags.Scanning Specific Repositories
To restrict the scan to one or more repositories, use the--repository flag followed by the repository name(s) in owner/repo-name format:
Scanning Specific Organizations
To restrict the scan to one or more organizations or user accounts, use the--organization flag:
Scanning Specific Repositories Within an Organization
To scan specific repositories within an organization, combine the--organization and --repository flags. The --organization flag qualifies unqualified repository names automatically:
my-organization/my-repo. Fully qualified repository names (owner/repo-name) are also supported alongside --organization:
my-repo is qualified as my-org/my-repo, while other-owner/other-repo is used as-is.
The
--repository and --organization flags can be combined with any authentication method.Filtering Scans
Customize your scan scope with these options:Example Workflows
- Quick Security Assessment
- Organization Compliance Audit
- CI/CD Integration
- Multi-Organization Scan
Viewing Prowler CLI Scan Results
Prowler CLI generates results in multiple formats:Next Steps
Authentication Guide
Detailed permissions and token creation
Available Checks
Browse all GitHub security checks
Compliance Frameworks
CIS, NIST, and other frameworks
Troubleshooting
Common issues and solutions