Accessing Prowler Cloud and API Documentation
If you are a Prowler Cloud user, you can access API docs at https://api.prowler.com/api/v1/docsFor Prowler App usersAfter installing Prowler App, access it at http://localhost:3000.To view the auto-generated Prowler API documentation, navigate to http://localhost:8080/api/v1/docs. This documentation provides details on available endpoints, parameters, and responses.
Step 1: Sign Up
Sign Up with Email
To get started, sign up using your email and password:
Sign Up with Social Login
If Social Login is enabled, you can sign up using your preferred provider (e.g., Google, GitHub).How Social Login WorksIf your email is already registered, you will be logged in, and your social account will be linked.
If your email is not registered, a new account will be created using your social account email.
Enable Social LoginSee how to configure Social Login for Prowler to enable this feature in your own deployments.
Step 2: Log In
Once registered, log in with your email and password to access Prowler App.
Step 3: Add a Provider
To perform security scans, link a cloud provider account. Prowler supports the following providers and more:- AWS
- Azure
- Google Cloud Platform (GCP)
- Kubernetes
- M365
- GitHub
- Oracle Cloud Infrastructure (OCI)
- Navigate to
Settings > Cloud Providers. - Click
Add Accountto set up a new provider and provide your credentials.
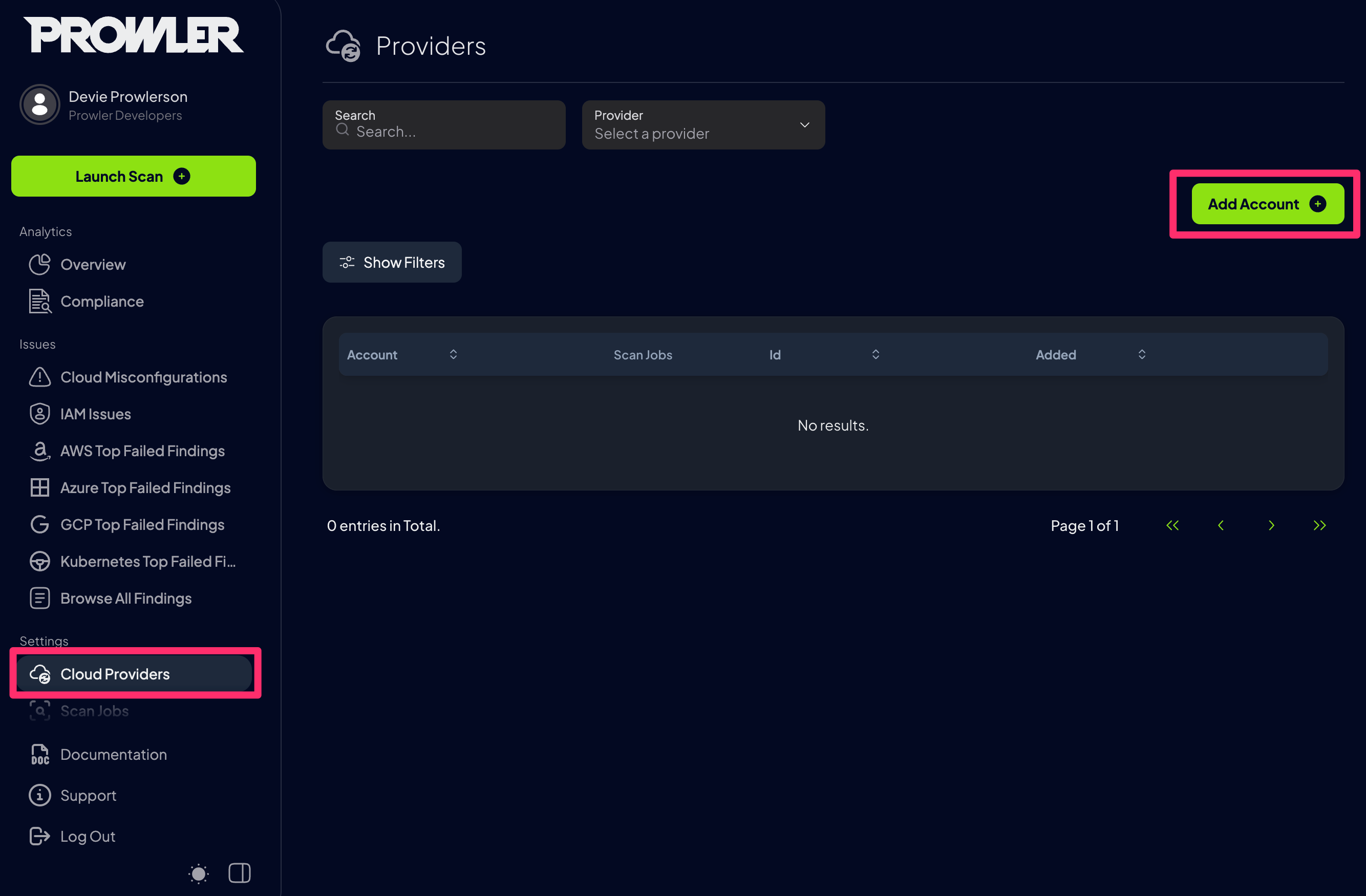
Step 4: Configure the Provider
Select the cloud provider to scan and configure authentication credentials. Each provider has specific requirements and authentication methods.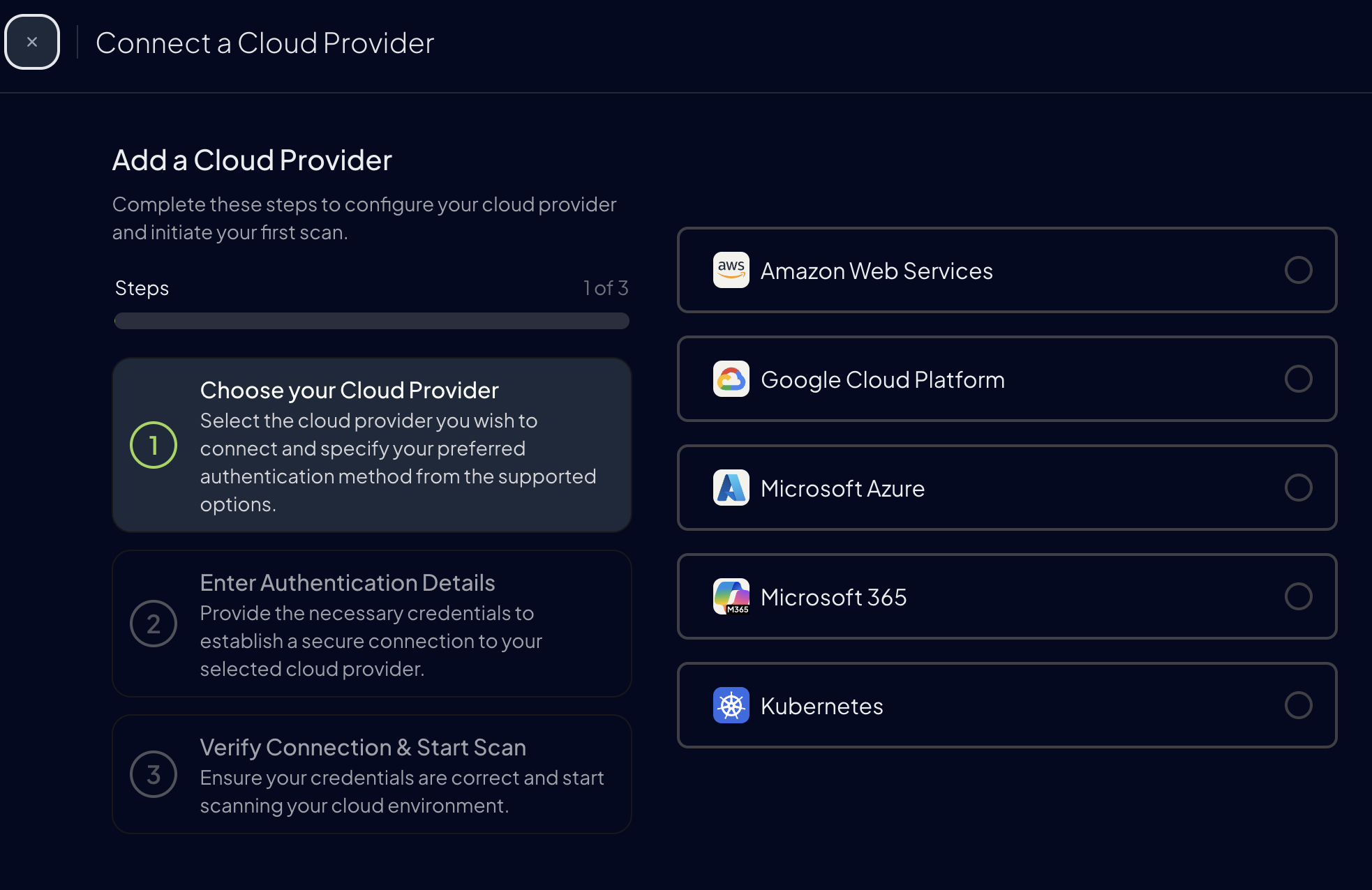
AWS
Configure AWS authentication using IAM Access Keys or Assumed Role credentials.
Azure
Set up Azure authentication using Service Principal credentials.
Google Cloud
Configure GCP authentication with Service Account or Application Default Credentials.
Oracle Cloud Infrastructure
Connect OCI with API key credentials to scan compartments and regions.
Kubernetes
Set up Kubernetes authentication using kubeconfig files for cluster access.
Microsoft 365
Configure M365 authentication with Application Certificate or Client Secret.
GitHub
Set up GitHub authentication using Personal Access Token, OAuth App, or GitHub App.
Infrastructure as Code
Scan IaC public or private repositories for security issues.
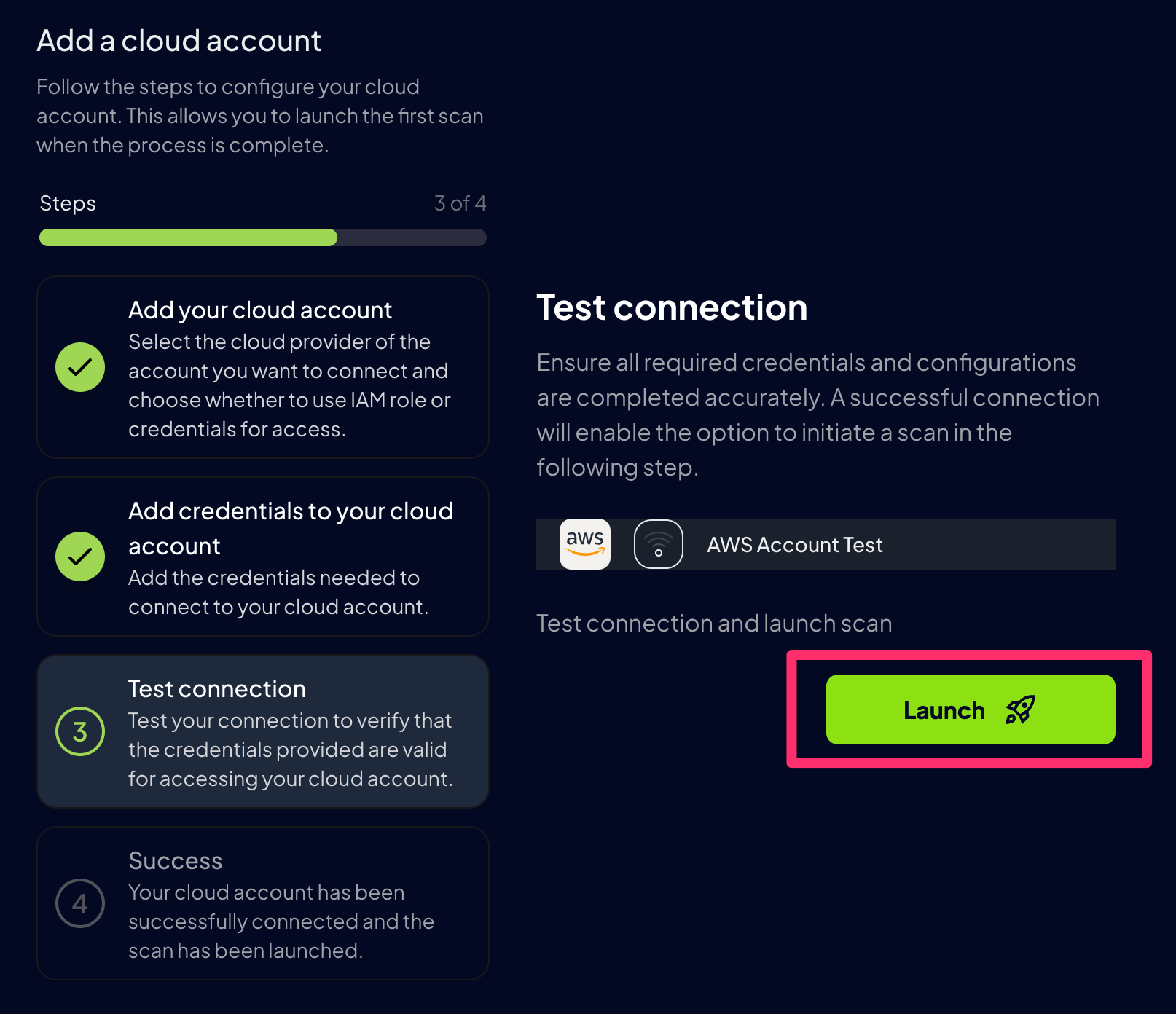
Step 5: Test Connection
After adding your credentials of your cloud account, click theLaunch button to verify that Prowler App can successfully connect to your provider:
Step 6: Scan started
After successfully adding and testing your credentials, Prowler will start scanning your cloud environment, click theGo to Scans button to see the progress:
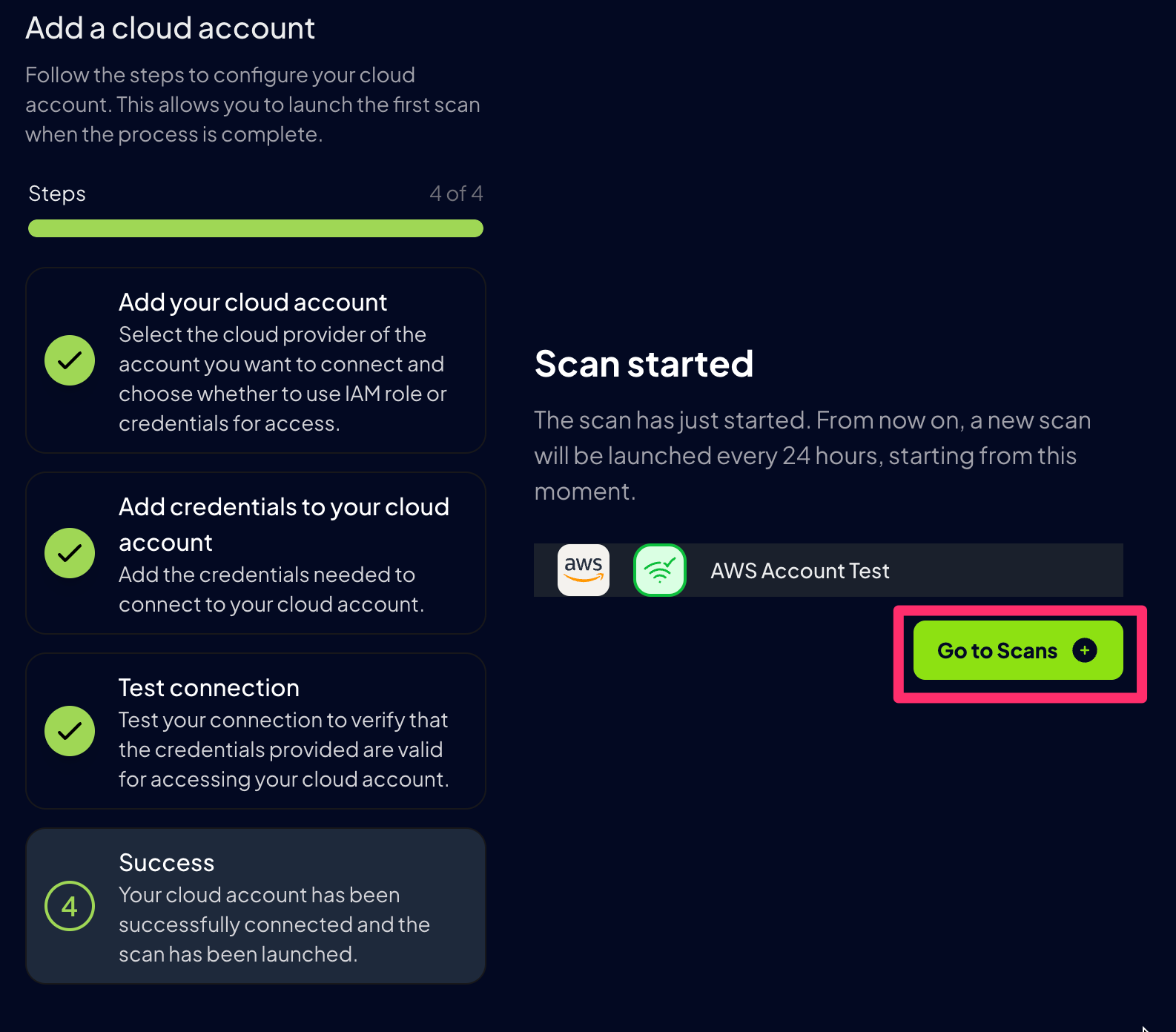
Prowler will automatically scan all configured providers every 24 hours, ensuring your cloud environment stays continuously monitored.
Step 7: Monitor Scan Progress
Track the progress of your scan in theScans section:
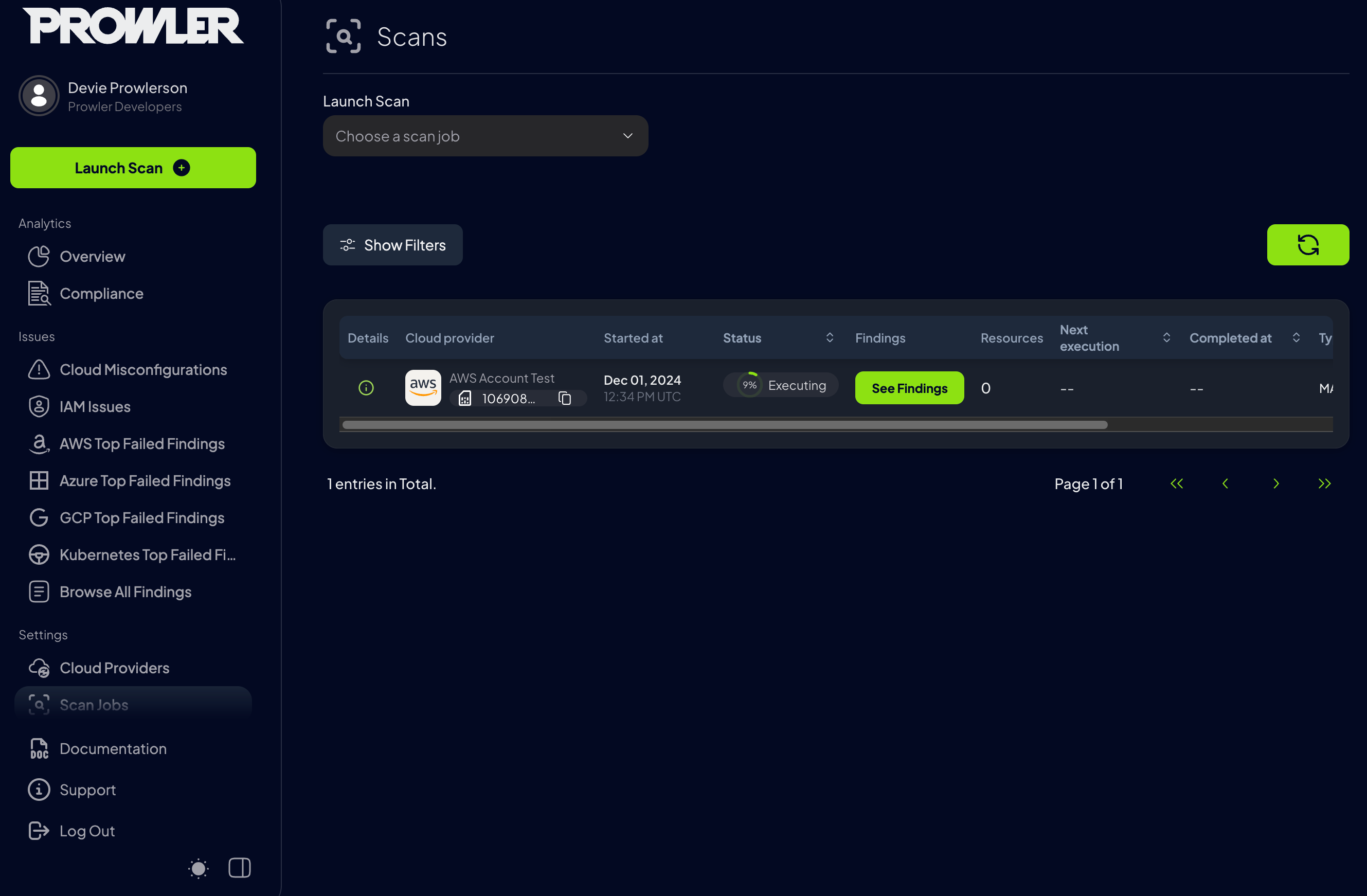
How Dashboards Display Scan DataEach dashboard handles scan data differently:
- Overview displays aggregated metrics from the latest completed scan per provider only.
- Findings displays results from the latest completed scan per provider by default. To access historical findings, apply a date or scan filter.
- Resources lists all discovered resources across all scans. However, when selecting a resource, the Findings tab within the resource detail shows only findings from the latest completed scan. If the latest scan did not evaluate a particular resource, its Findings tab may appear empty.
Step 8: Analyze the Findings
While the scan is running, start exploring the findings in these sections:-
Overview: High-level summary of the scans.
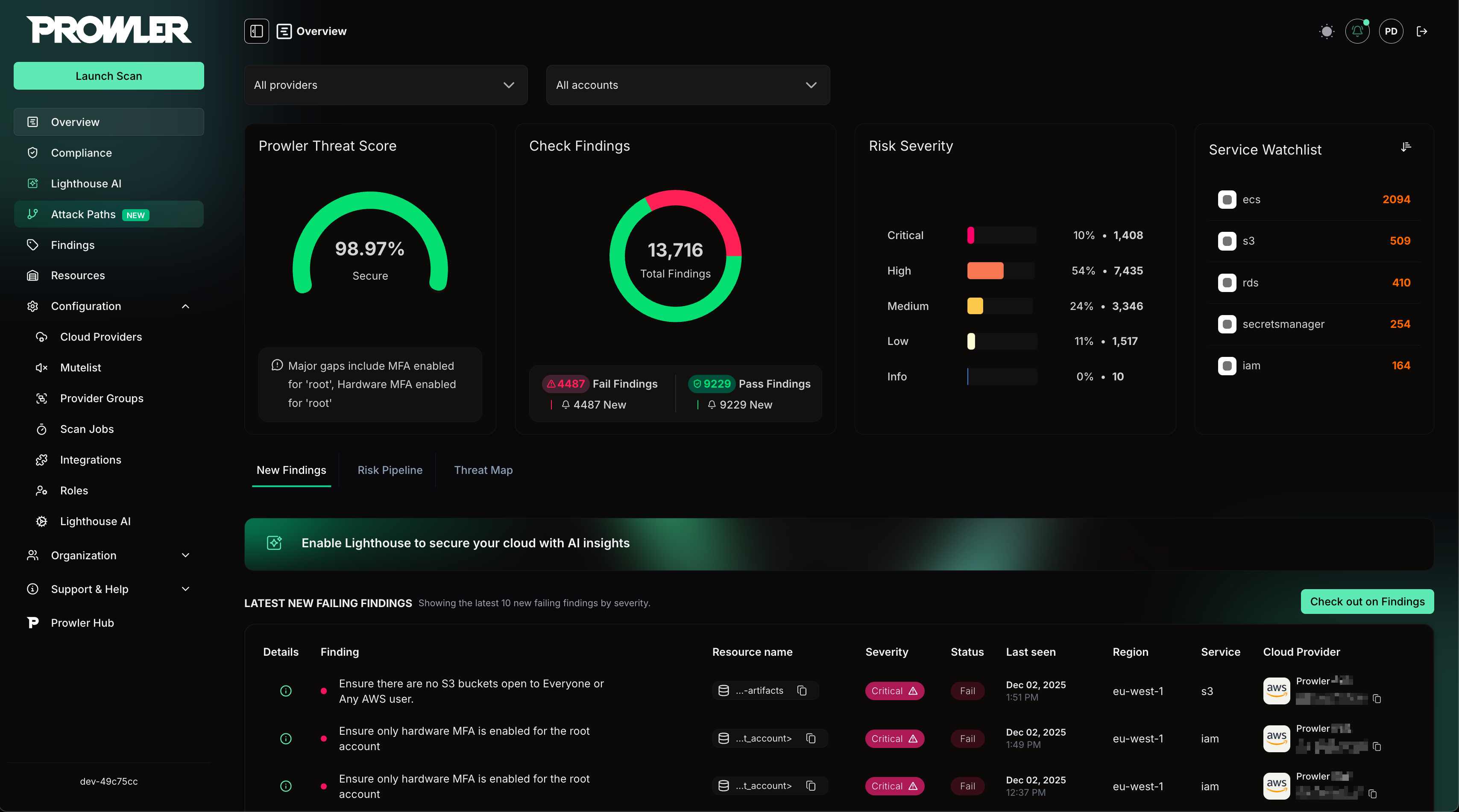
-
Compliance: Insights into compliance status.
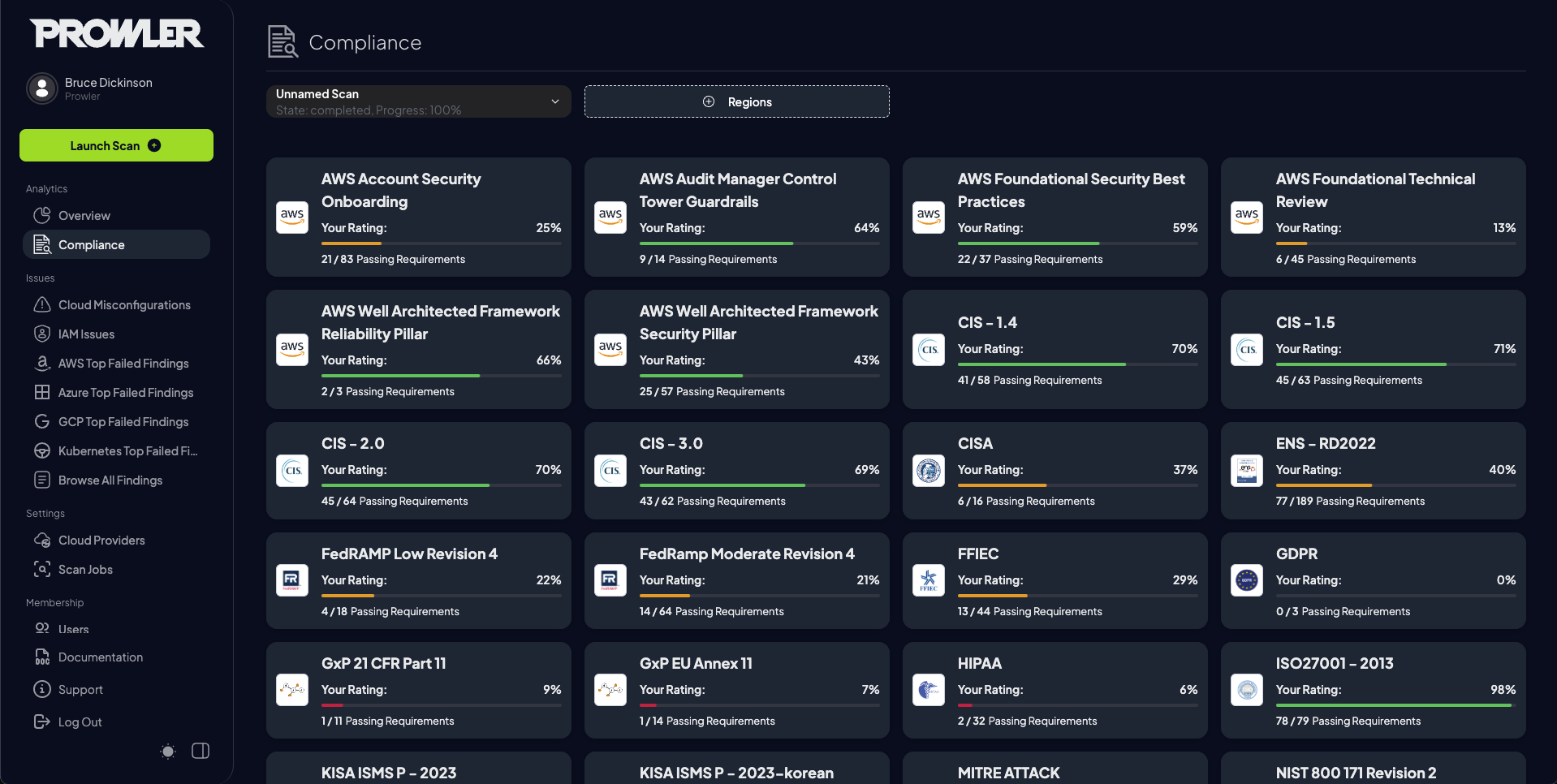
-
Issues: Types of issues detected.
-
Browse All Findings: Detailed list of findings detected, where you can filter by severity, service, and more.
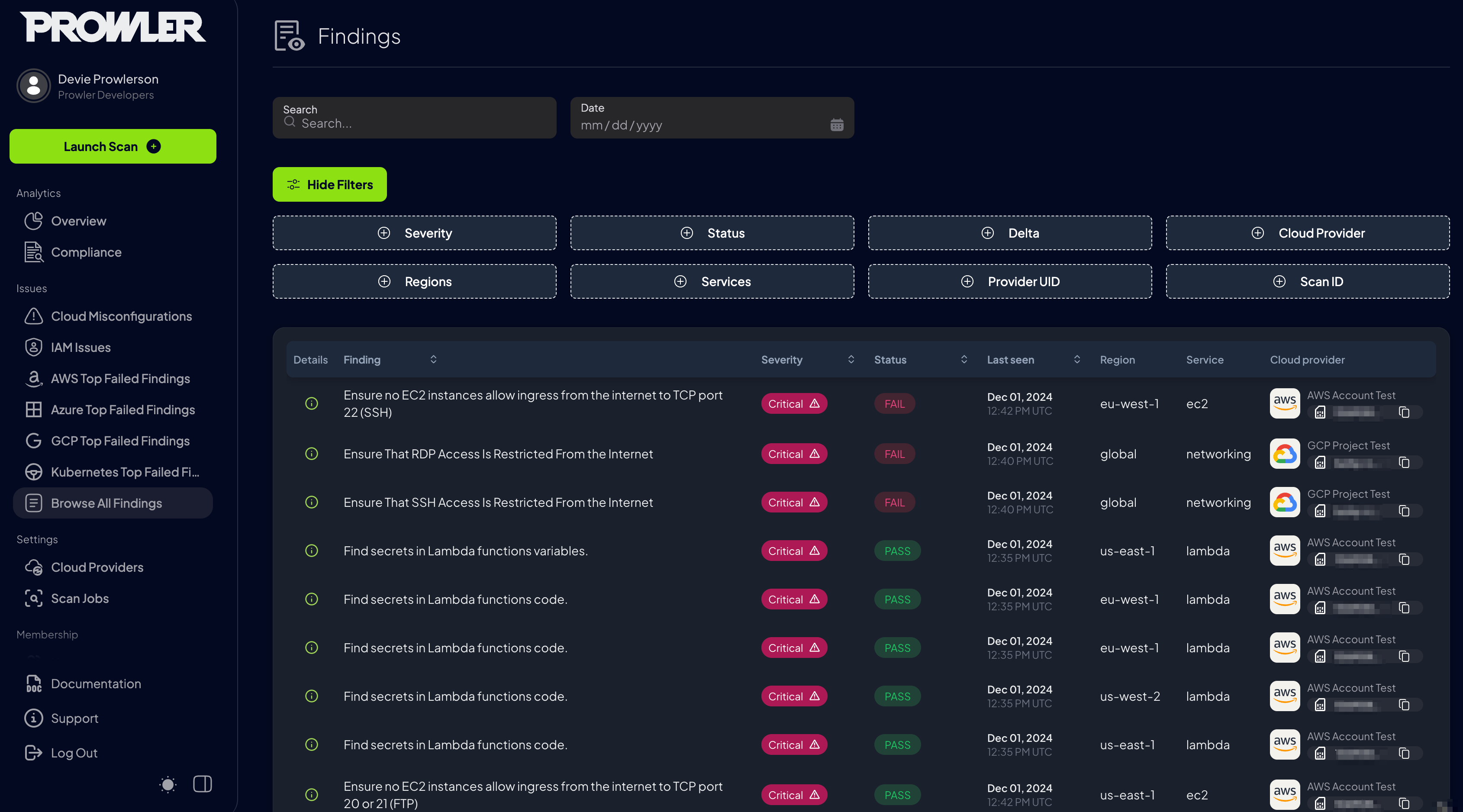
new findings that have not been seen prior to this scan, click the Delta filter and select new. To view all changed findings that have had a status change (from PASS to FAIL for example), click the Delta filter and select changed.
Step 9: Download the Outputs
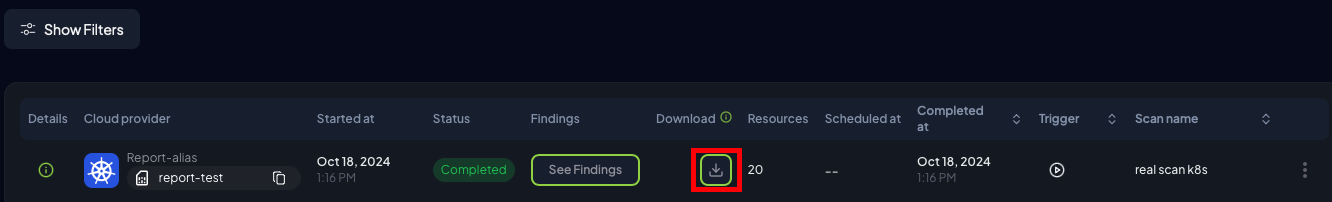
Once a scan is complete, navigate to the Scan Jobs section to download the output files generated by Prowler:
zip file. This archive contains the CSV, JSON-OSCF, and HTML reports detailing the findings.
To download these files, click the Download button. This button becomes available only after the scan has finished.
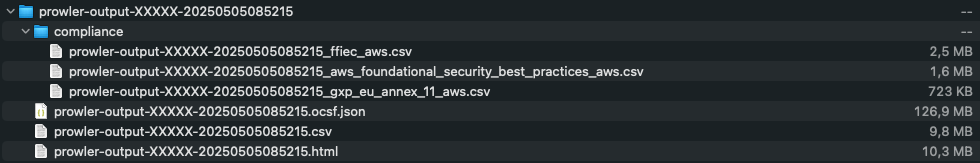
zip file unpacks into a folder named like prowler-output-<provider_id>-<timestamp>, which includes all of the above outputs. In the example below, you can see the .csv, .json, and .html reports alongside a subfolder for detailed compliance checks.
API NoteFor more information about the API endpoint used by the UI to download the ZIP archive, refer to: Prowler API Reference - Download Scan Output
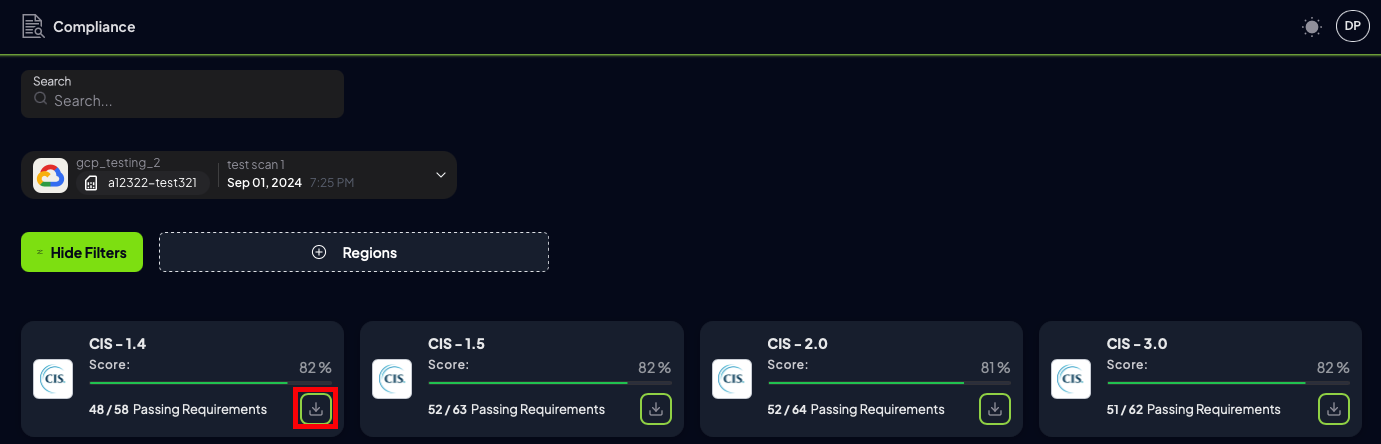
Step 10: Download specified compliance report
Once your scan has finished, you don’t need to grab the entire ZIP—just pull down the specific compliance report you want:- Navigate to the Compliance section of the UI.
- Find the Framework report you need.
- Click its Download icon to retrieve that report’s CSV file with all the detailed findings.
API NoteTo fetch a single compliance report via API, see the Retrieve compliance report as CSV endpoint in the Prowler API Reference.Prowler API Reference - Retrieve compliance report as CSV

