Added in: 5.9.0
Prowler App allows users to mute specific findings to focus on the most critical security issues. This comprehensive guide demonstrates how to effectively use the Mutelist feature to manage and prioritize security findings.
What Is the Mutelist Feature?
The Mutelist feature enables users to:- Suppress specific findings from appearing in future scans
- Focus on critical issues by hiding resolved or accepted risks
- Maintain audit trails of muted findings for compliance purposes
- Streamline security workflows by reducing noise from non-critical findings
Prerequisites
Before muting findings, ensure:- Valid access to Prowler App with appropriate permissions
- A provider added to the Prowler App
- Understanding of the security implications of muting specific findings
Step 1: Add a provider
To configure Mutelist:- Log into Prowler App
- Navigate to the providers page
- Add a provider, then “Configure Muted Findings” button will be enabled in providers page and scans page
Step 2: Configure Mutelist
- Open the modal by clicking “Configure Muted Findings” button
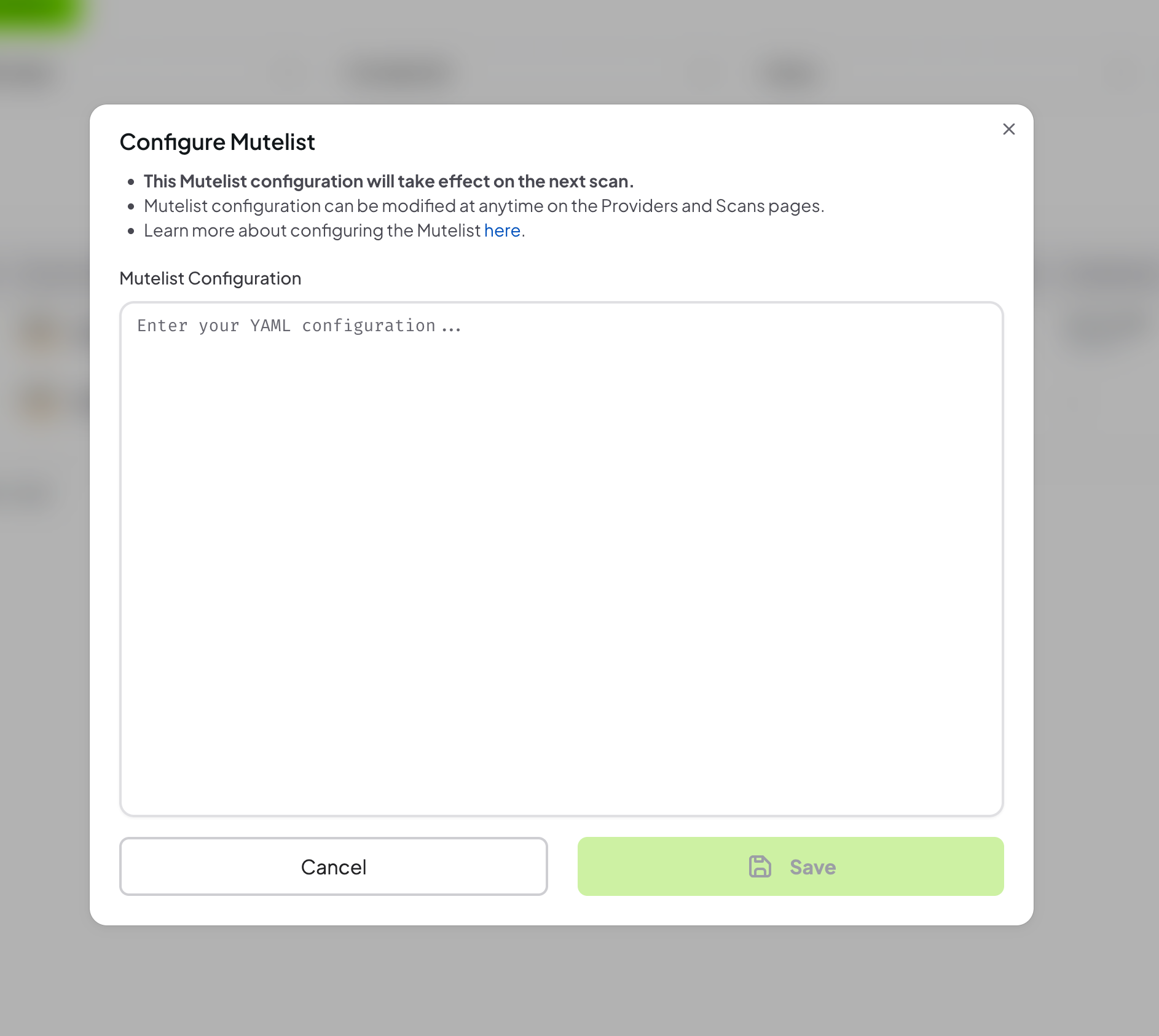
- Provide a valid Mutelist in
YAMLformat. More details about Mutelist here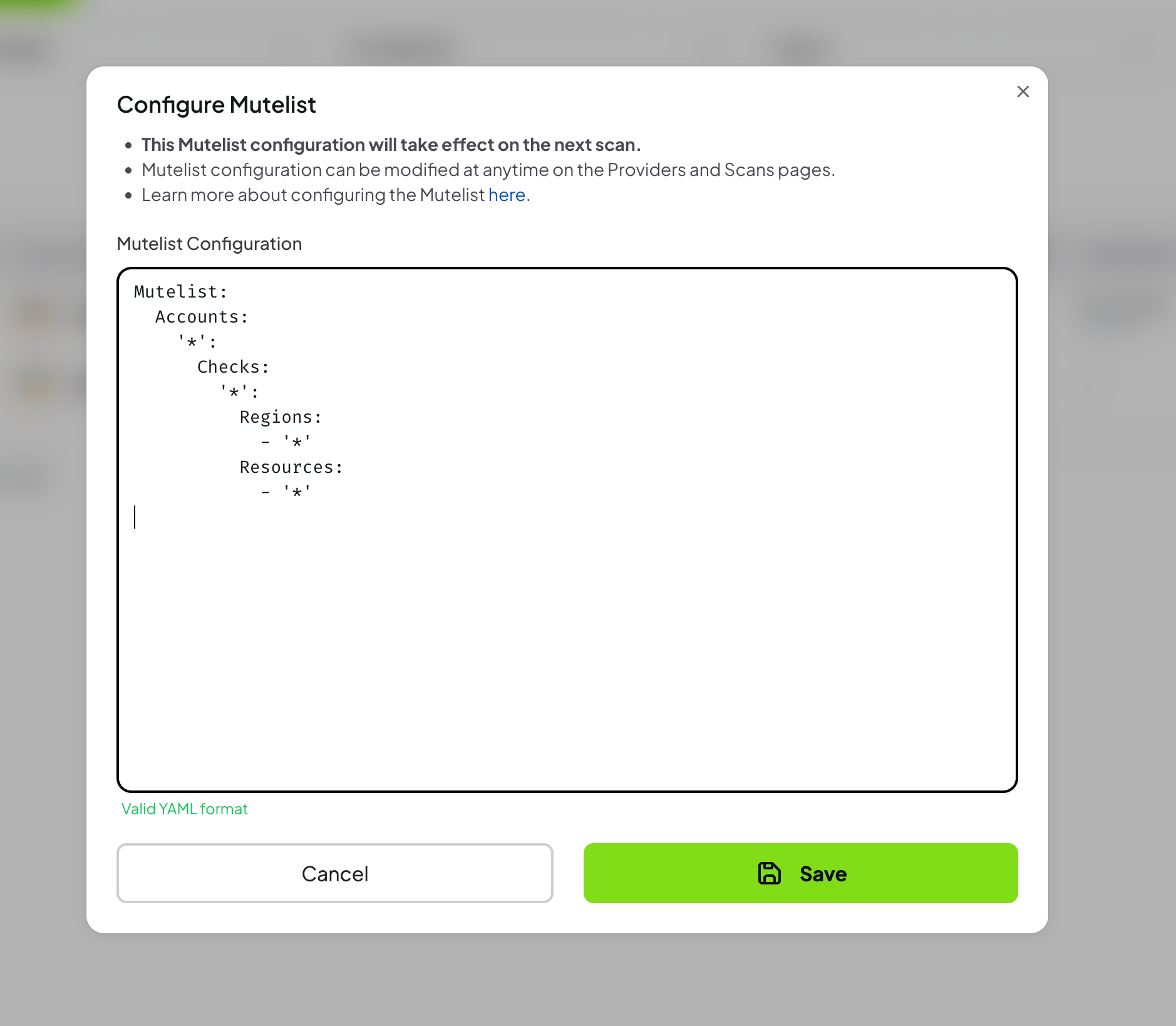
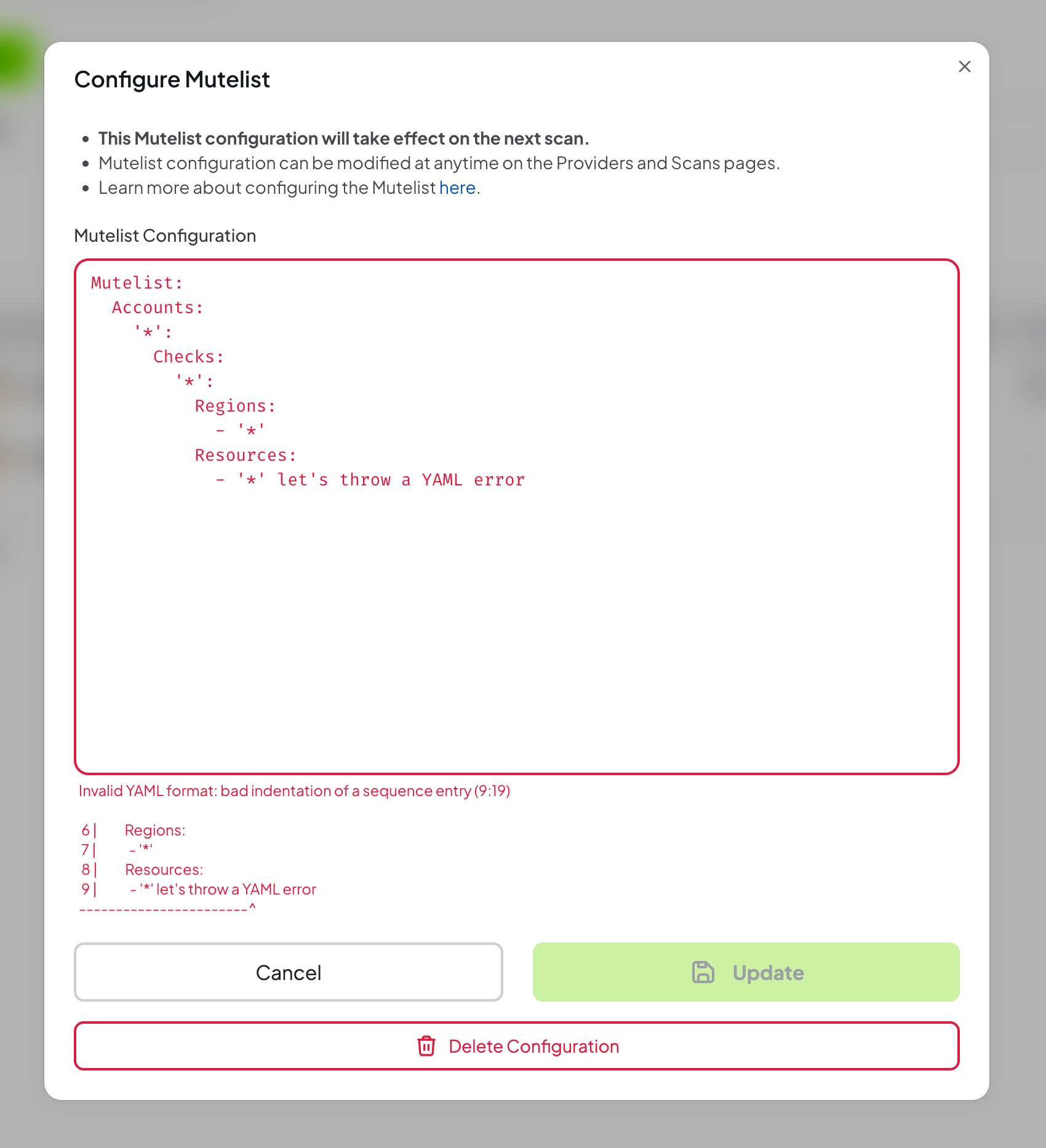
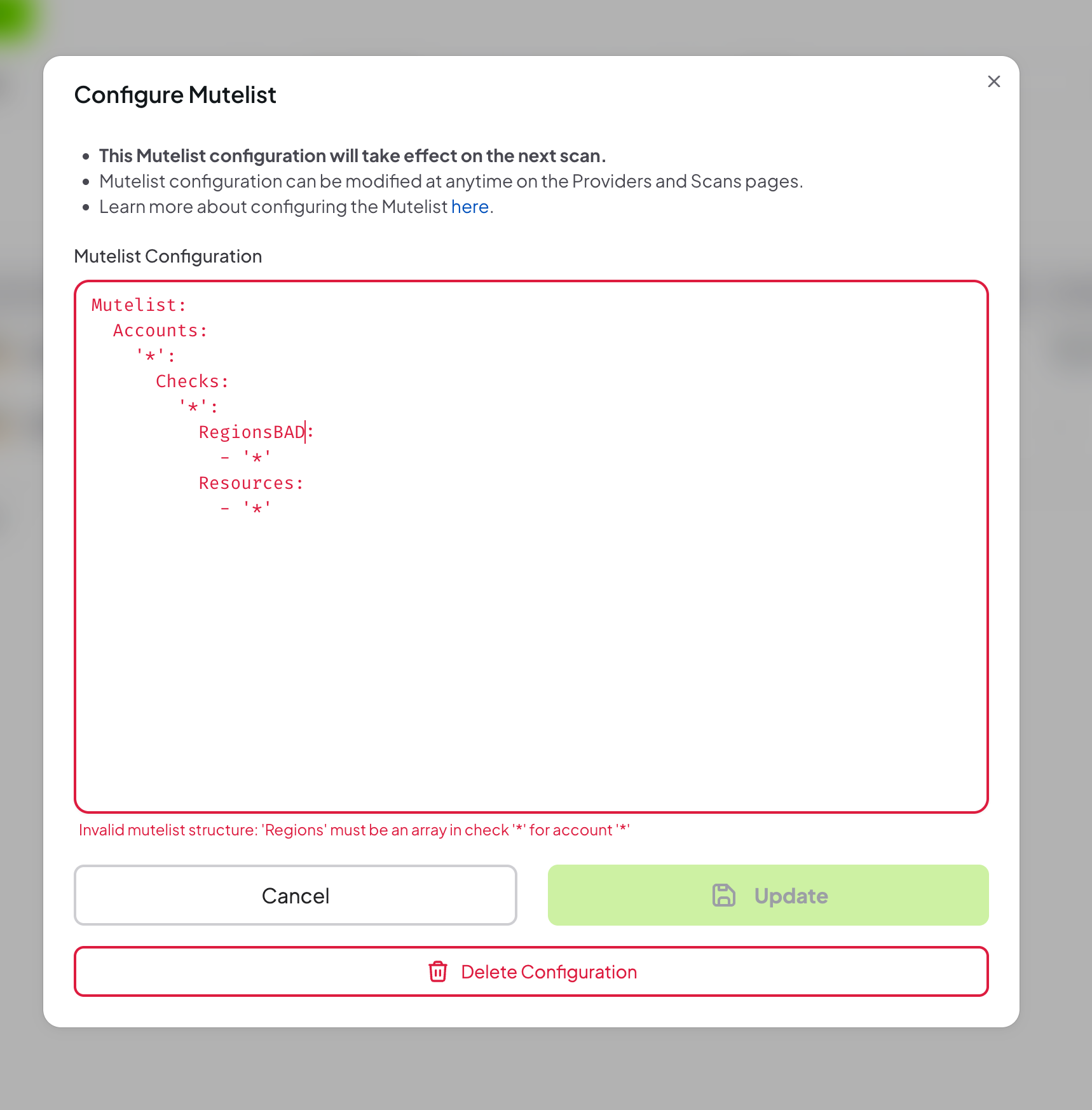
Step 3: Review the Mutelist
- Once added, the configuration can be removed or updated
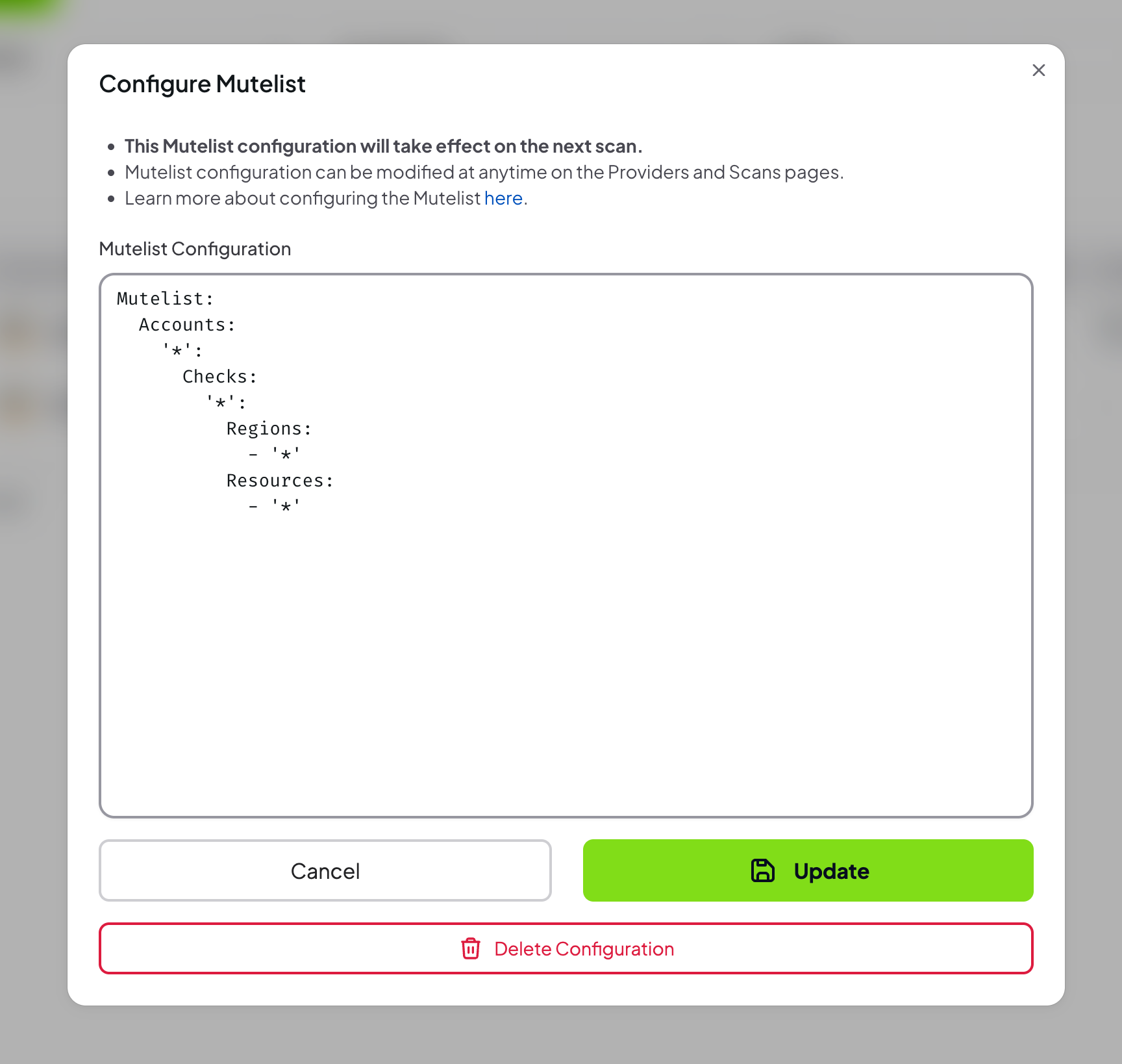
Step 4: Check muted findings in the scan results
- Run a new scan
- Check the muted findings in the scan results
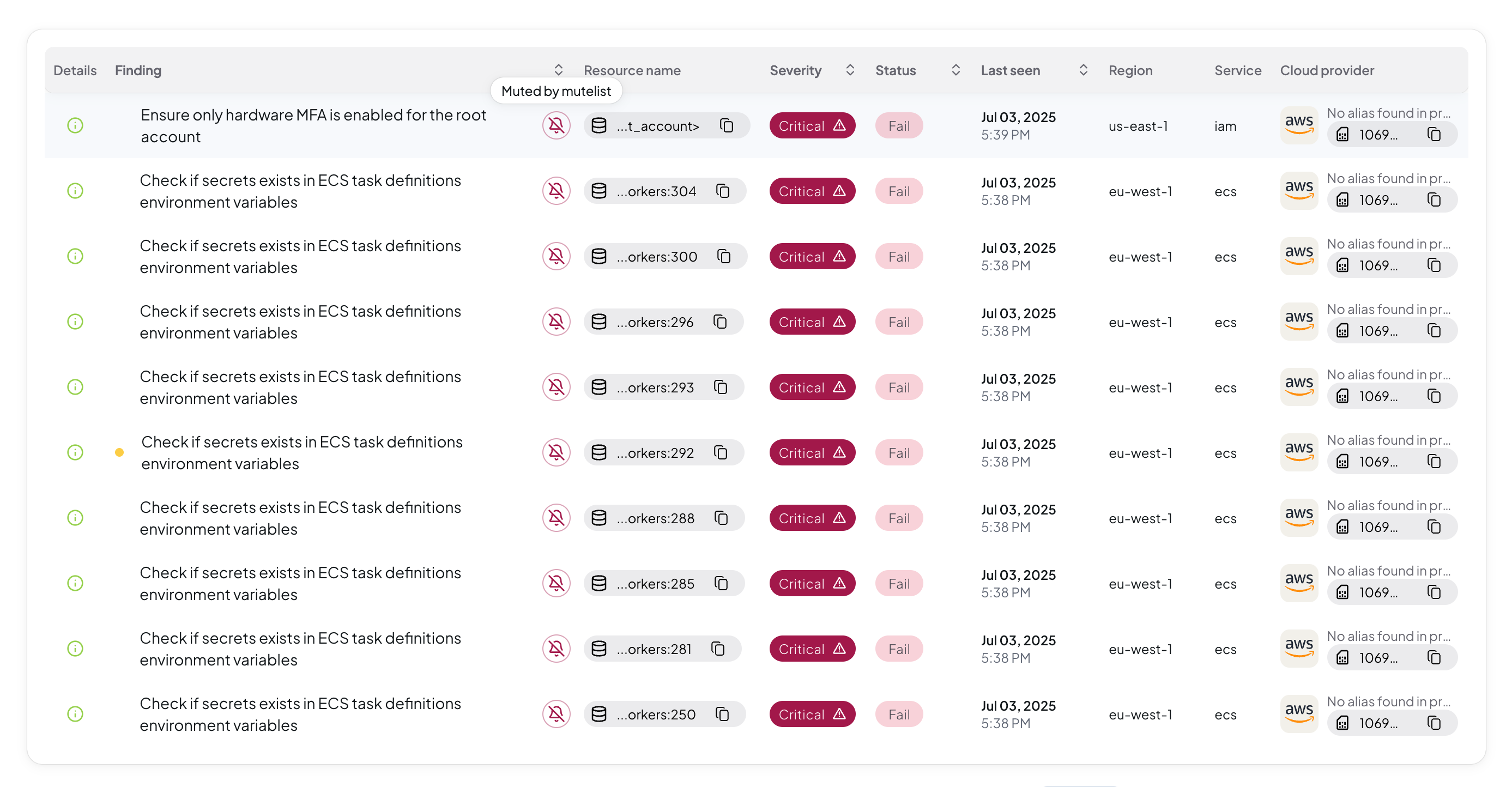
The Mutelist configuration takes effect on the next scans.
Mutelist Ready To Use Examples
Below are examples for different cloud providers supported by Prowler App. Check how the mutelist works here.AWS Provider
Basic AWS Mutelist
AWS Service-Wide Muting
AWS Tag-Based Muting
Azure Provider
For Azure provider, the Account ID is the Subscription Name and the Region is the Location.
Basic Azure Mutelist
Azure Resource Group Muting
GCP Provider
For GCP provider, the Account ID is the Project ID and the Region is the Zone.
Basic GCP Mutelist
GCP Project-Wide Muting
Kubernetes Provider
For Kubernetes provider, the Account ID is the Cluster Name and the Region is the Namespace.
Basic Kubernetes Mutelist
Kubernetes Namespace Muting
Microsoft 365 Provider
Basic Microsoft 365 Mutelist
Microsoft 365 Tenant-Wide Muting
Multi-Cloud Mutelist
You can combine multiple providers in a single mutelist configuration:Advanced Mutelist Features
Using Regular Expressions
Using Exceptions
Tag-Based Logic
Best Practices
- Start Small: Begin with specific resources and gradually expand
- Document Reasons: Always include descriptions for audit trails
- Regular Reviews: Periodically review muted findings
- Use Tags: Leverage resource tags for better organization
- Test Changes: Validate mutelist changes in non-production environments
- Monitor Impact: Track how muting affects your security posture
Validation
Prowler App validates your mutelist configuration and will display errors for:- Invalid YAML syntax
- Missing required fields
- Invalid regular expressions
- Unsupported provider-specific configurations

