Added in: 5.10.0
Prowler App allows automatic export of scan results to Amazon S3 buckets, providing seamless integration with existing data workflows and storage infrastructure. This comprehensive guide demonstrates configuration and management of Amazon S3 integrations to streamline security finding management and reporting.
When enabled and configured, scan results are automatically stored in the configured bucket. Results are provided in csv, html and json-ocsf formats, offering flexibility for custom integrations:
Enabling this integration incurs costs in Amazon S3. Refer to Amazon S3 pricing for more information.
- Automate scan result exports to designated S3 buckets after each scan
- Configure separate bucket destinations for different cloud providers or use cases
- Customize export paths within buckets for organized storage
- Support multiple authentication methods including IAM roles and static credentials
- Verify connection reliability through built-in connection testing
- Manage integrations independently with separate configuration and credential controls
Required Permissions
Before configuring the Amazon S3 Integration, ensure that AWS credentials and optionally the IAM Role used for S3 access have the necessary permissions to write scan results to the designated S3 bucket. This requirement applies when using static credentials, session credentials, or an IAM role (either self-created or generated using Prowler’s permissions templates).IAM Policy
The S3 integration requires the following permissions. Add these to the IAM role policy, or ensure AWS credentials have these permissions:s3:DeleteObject
s3:DeleteObject permission is required for connection testing. When testing the S3 integration, Prowler creates a temporary beacon file, test-prowler-connection.txt, to verify write permissions, then deletes it to confirm the connection is working properly.
s3:PutObject
s3:ListBucket
Replace
<BUCKET AWS ACCOUNT NUMBER> with the AWS account ID that owns the destination S3 bucket, and <BUCKET NAME> with the actual bucket name.Cross-Account S3 Bucket
If the S3 destination bucket is in a different AWS account than the one providing the credentials for S3 access, configure a bucket policy on the destination bucket to allow cross-account access. The following diagrams illustrate the three common S3 integration scenarios:Same Account Setup (No Bucket Policy Required)
When both the IAM credentials and destination S3 bucket are in the same AWS account, no additional bucket policy is required.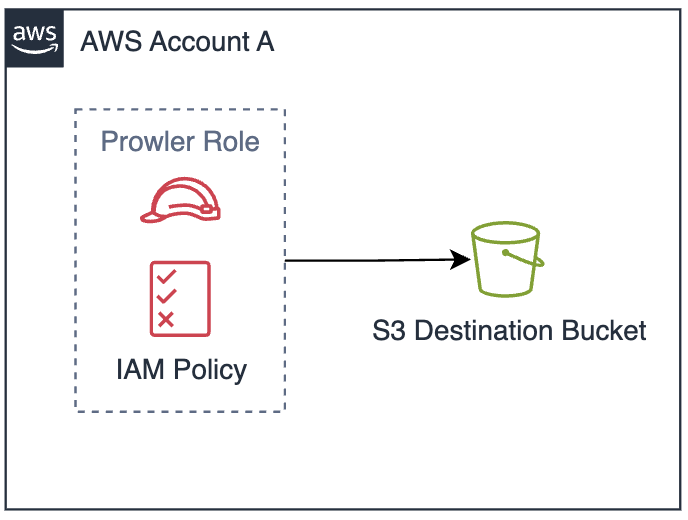
Cross-Account Setup (Bucket Policy Required)
When the S3 bucket is in a different AWS account, you must configure a bucket policy to allow cross-account access.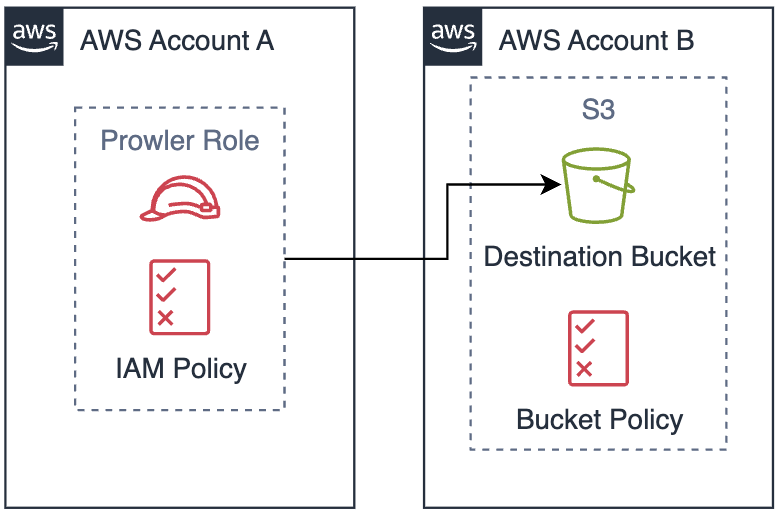
Multi-Account Setup (Multiple Principals in Bucket Policy)
When multiple AWS accounts need to write to the same destination bucket, configure the bucket policy with multiple principals.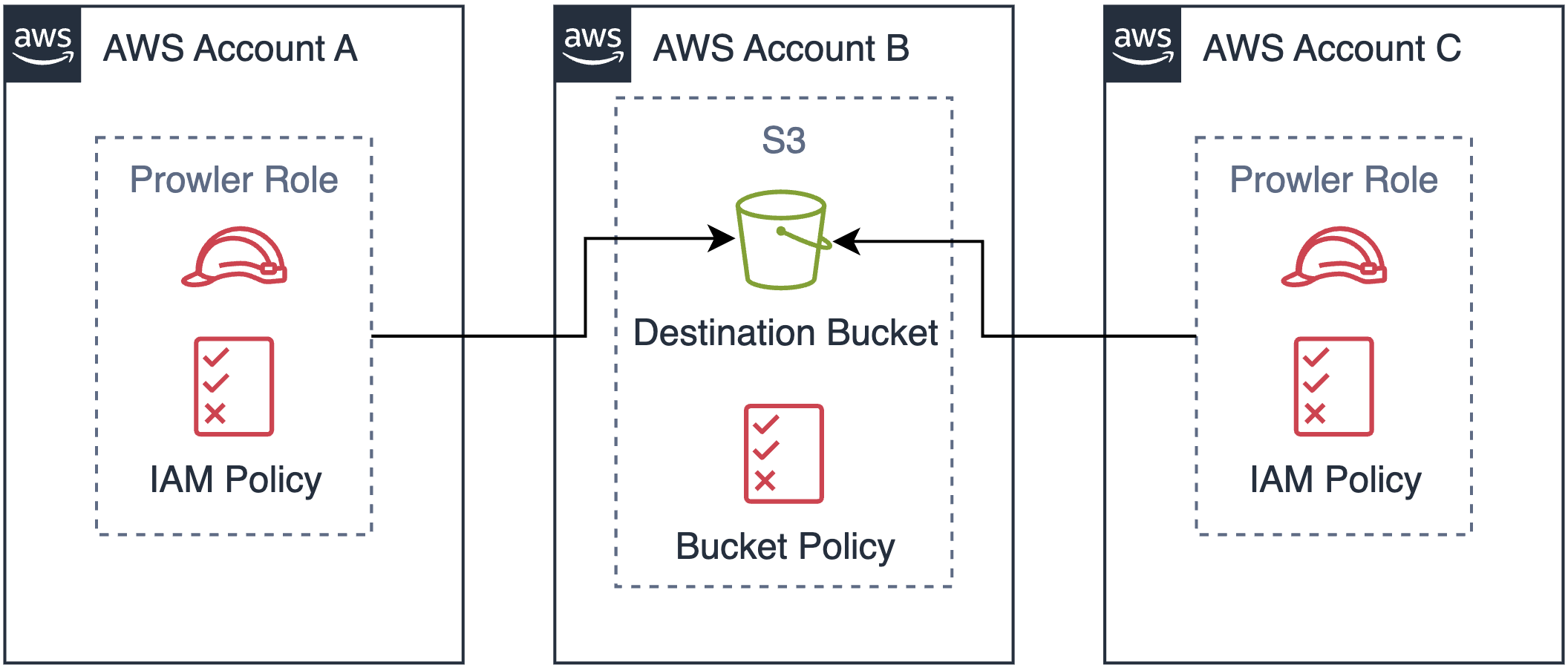
S3 Bucket Policy
Apply the following bucket policy to the destination S3 bucket:Replace
<SOURCE ACCOUNT ID> with the AWS account ID that contains the IAM role and <BUCKET NAME> with the destination bucket name. The role name ProwlerScan is the default name when using Prowler’s permissions templates. If using a custom IAM role or different authentication method, replace ProwlerScan with the actual role name.Multi-Account Configuration
For multiple AWS accounts, modify thePrincipal field to an array:
Replace
<SOURCE ACCOUNT ID> with the AWS account ID that contains the IAM role and <BUCKET NAME> with the destination bucket name. The role name ProwlerScan is the default name when using Prowler’s permissions templates. If using a custom IAM role or different authentication method, replace ProwlerScan with the actual role name.Available Templates
Prowler App provides Infrastructure as Code (IaC) templates to automate IAM role setup with S3 integration permissions.Templates are optional. Custom IAM roles or static credentials can be used instead.
CloudFormation
AWS CLI
When using Prowler’s CloudFormation template, execute the following command to update the existing Prowler stack:ProwlerScan IAM Role, execute the following command to create the CloudFormation stack:
AWS Console
If using Prowler’s CloudFormation template, execute the following command to update the existing Prowler stack:- Navigate to CloudFormation service in the AWS region you are using
- Select “ProwlerScan”, click “Update” and then “Make a direct update”
- Replace template, uploading the CloudFormation template
- Configure parameters:
ExternalId: Keep existing valueEnableS3Integration: Select “true”S3IntegrationBucketName: Your bucket nameS3IntegrationBucketAccountId: Bucket owner’s AWS account ID
- In the “Configure stack options” screen, again, leave everything as it is and click on “Next”
- Finally, under “Review Prowler”, at the bottom click on “Submit”
Terraform
-
Download the Terraform code:
-
Configure your variables:
-
Edit
terraform.tfvarswith your specific values: -
Deploy the infrastructure:
-
After successful deployment, Terraform will display important values:
-
Copy the
prowler_role_arn, as it’s required to complete the S3 integration credentials configuration.
Configuration
Once the required permissions are set up, proceed to configure the S3 integration in Prowler App.-
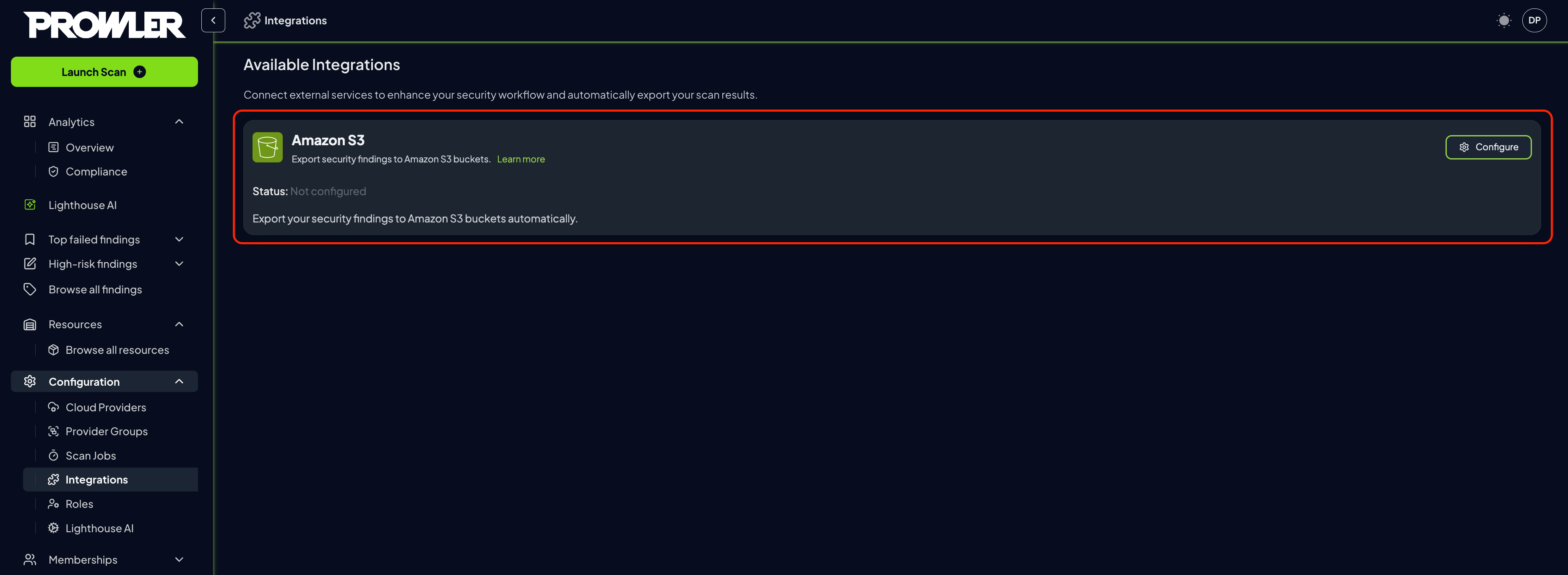
Navigate to “Integrations”
-
Locate the Amazon S3 Integration card and click on the “Configure” button
-
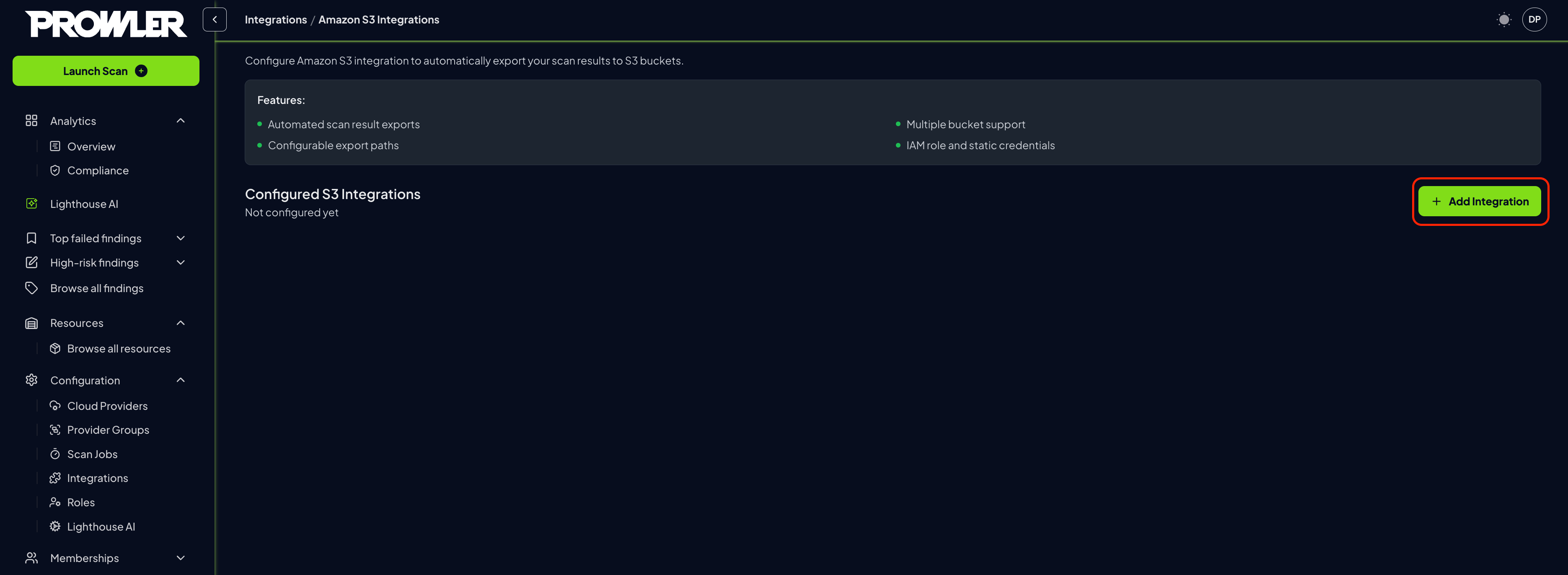
Click the “Add Integration” button
-
Complete the configuration form with the following details:
- Cloud Providers: Select the providers whose scan results should be exported to this S3 bucket
- Bucket Name: Enter the name of the target S3 bucket (e.g.,
my-security-findings-bucket) - Output Directory: Specify the directory path within the bucket (e.g.,
/prowler-findings/, defaults tooutput)
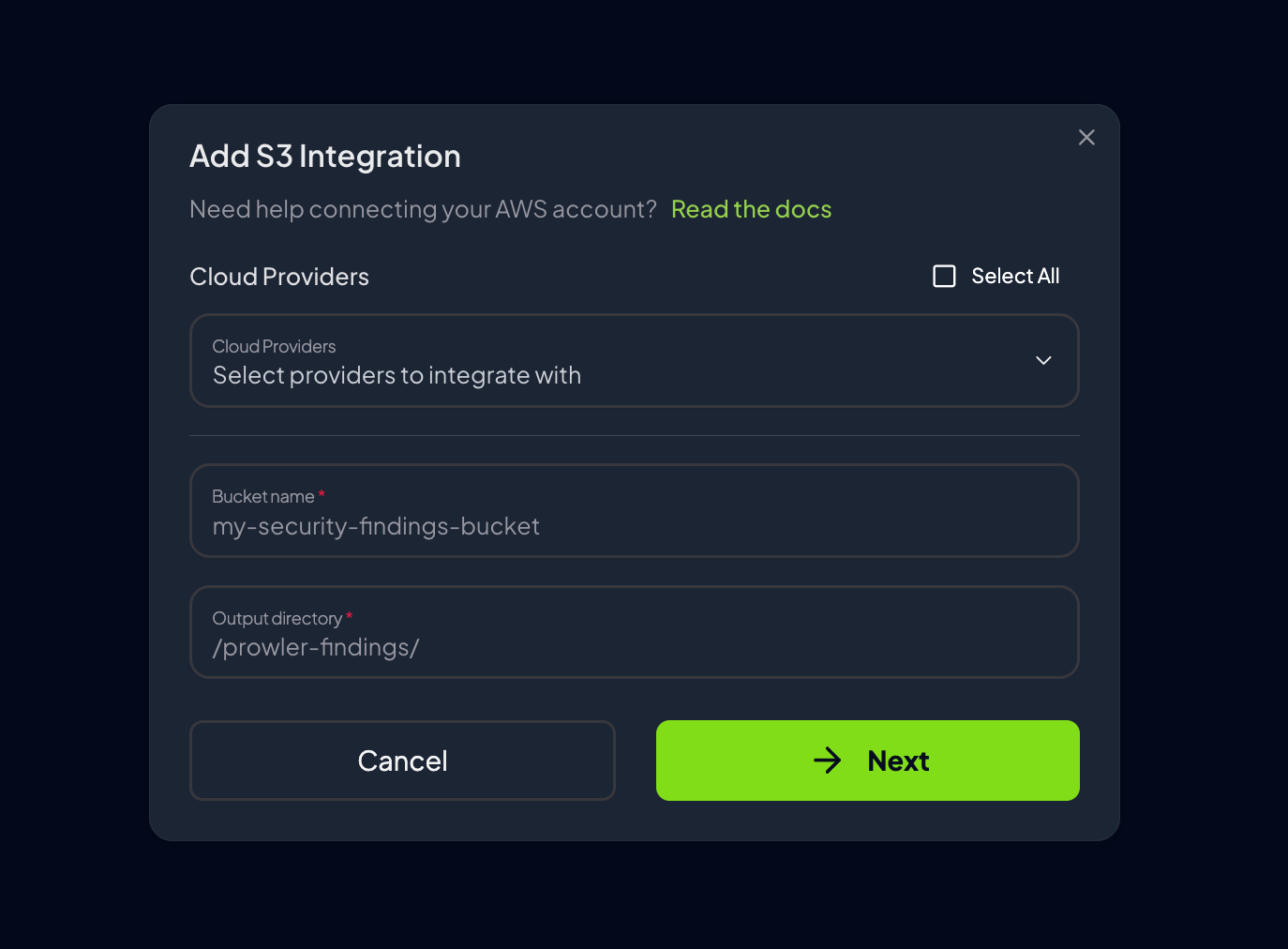
- Click “Next” to configure credentials
-
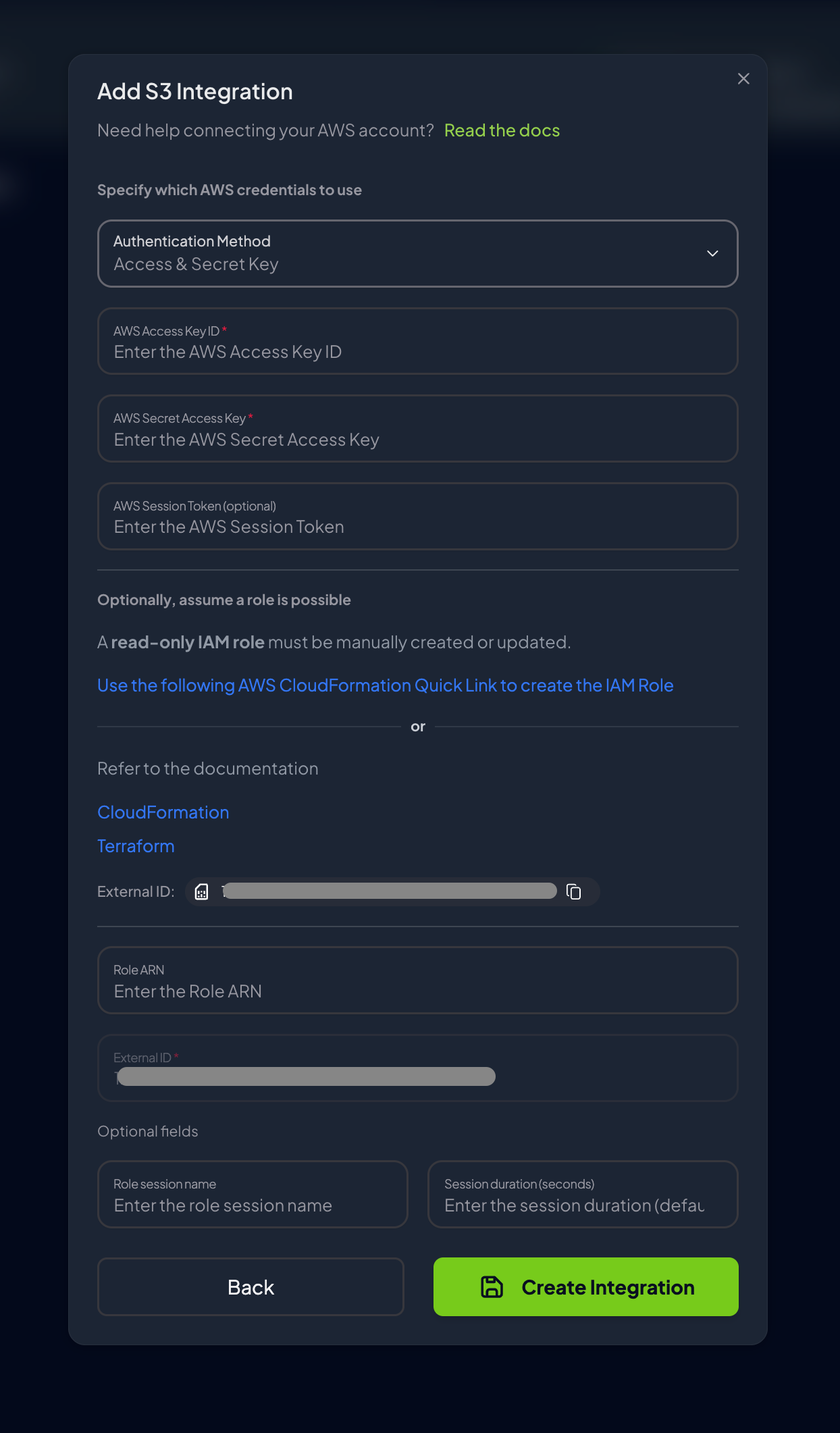
Configure AWS authentication using one of the supported methods:
- AWS SDK Default: Use default AWS credentials from the environment. For Prowler Cloud users, this is the recommended option as the service has AWS credentials to assume IAM roles with ARNs matching
arn:aws:iam::*:role/Prowler*orarn:aws:iam::*:role/prowler* - Access Keys: Provide AWS access key ID and secret access key
- IAM Role (optional): Specify the IAM Role ARN, external ID, and optional session parameters
- AWS SDK Default: Use default AWS credentials from the environment. For Prowler Cloud users, this is the recommended option as the service has AWS credentials to assume IAM roles with ARNs matching
-
Optional - For IAM role authentication, complete the required fields:
- Role ARN: The Amazon Resource Name of the IAM role
- External ID: Unique identifier for additional security (defaults to Tenant/Organization ID) - mandatory and automatically filled
- Role Session Name: Optional - name for the assumed role session
- Session Duration: Optional - duration in seconds for the session
- Click “Create Integration” to verify the connection and complete the setup
Once credentials are configured and the connection test passes, the S3 integration will be active. Scan results will automatically be exported to the specified bucket after each scan completes. Run a new scan and check the S3 bucket to verify the integration is working.
Scan outputs are processed after scan completion. Depending on scan size and network conditions, exports may take a few minutes to appear in the S3 bucket.
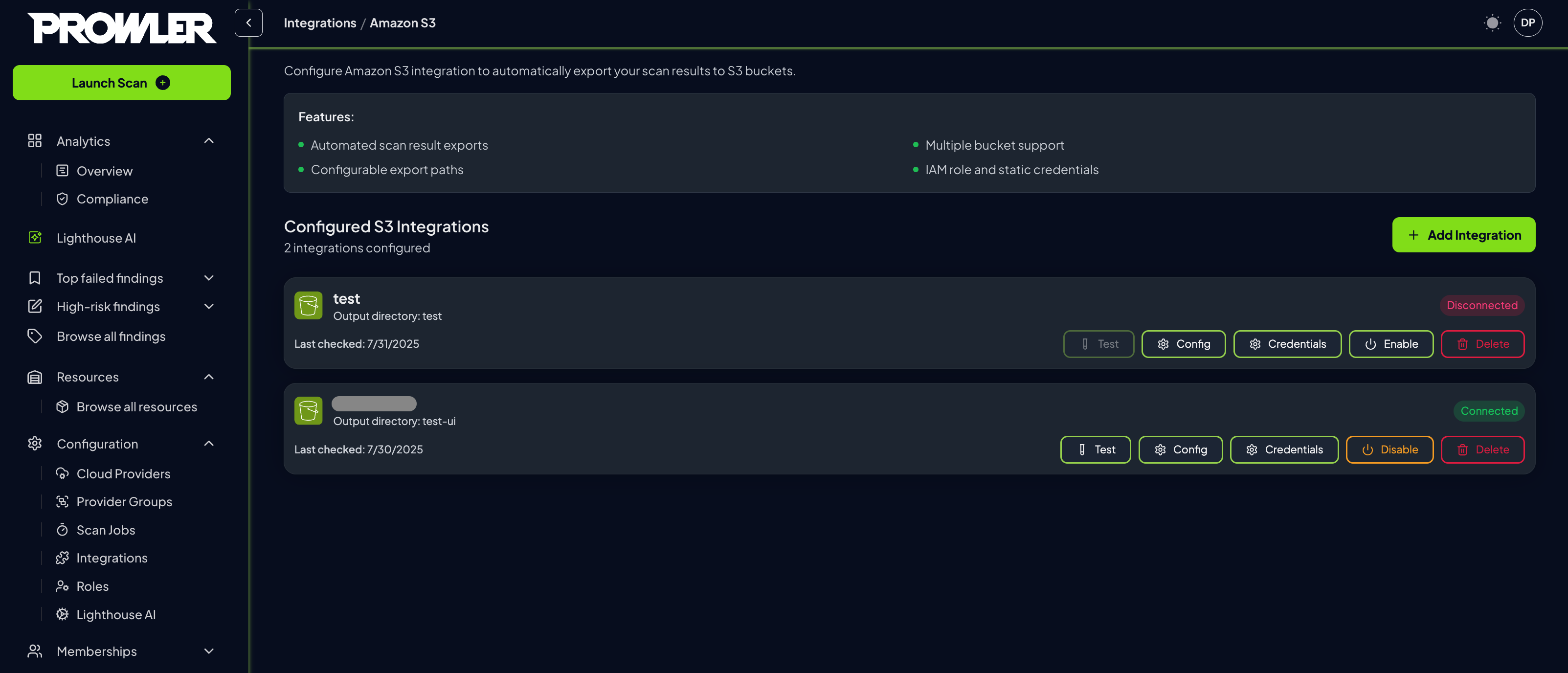
Integration Status
Once the integration is active, monitor its status and make adjustments as needed through the integrations management interface.- Review configured integrations in the management interface
-
Each integration displays:
- Connection Status: Connected or Disconnected indicator
- Bucket Information: Bucket name and output directory
- Last Checked: Timestamp of the most recent connection test
Actions
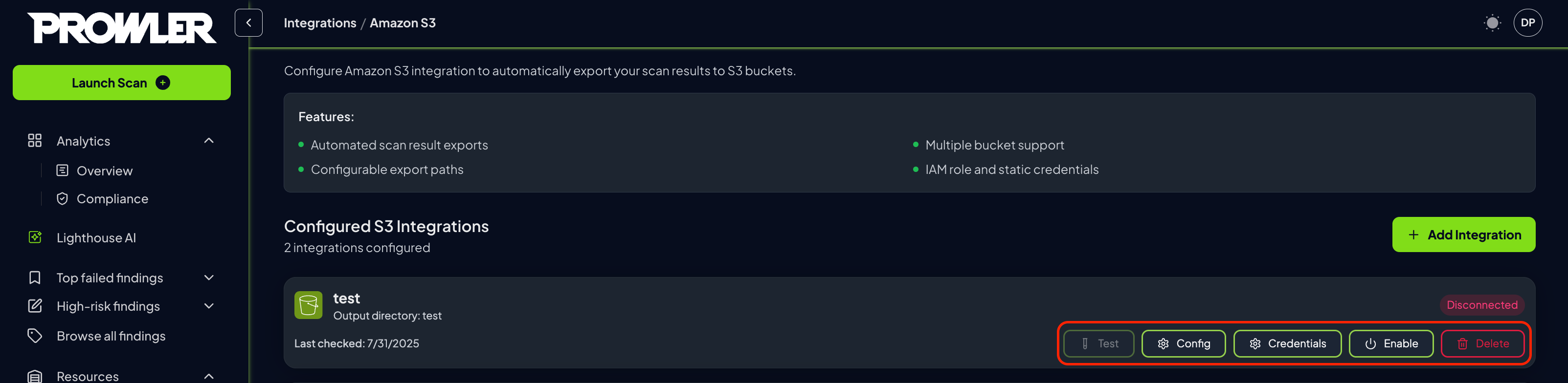
| Button | Purpose | Available Actions | Notes |
|---|---|---|---|
| Test | Verify integration connectivity | • Test AWS credential validity • Check S3 bucket accessibility • Verify write permissions • Validate connection setup | Results displayed in notification message |
| Config | Modify integration settings | • Update selected cloud providers • Change bucket name • Modify output directory path | Click “Update Configuration” to save changes |
| Credentials | Update authentication settings | • Modify AWS access keys • Update IAM role configuration • Change authentication method | Click “Update Credentials” to save changes |
| Enable/Disable | Toggle integration status | • Enable integration to start exporting results • Disable integration to pause exports | Status change takes effect immediately |
| Delete | Remove integration permanently | • Permanently delete integration • Remove all configuration data | ⚠️ Cannot be undone - confirm before deleting |
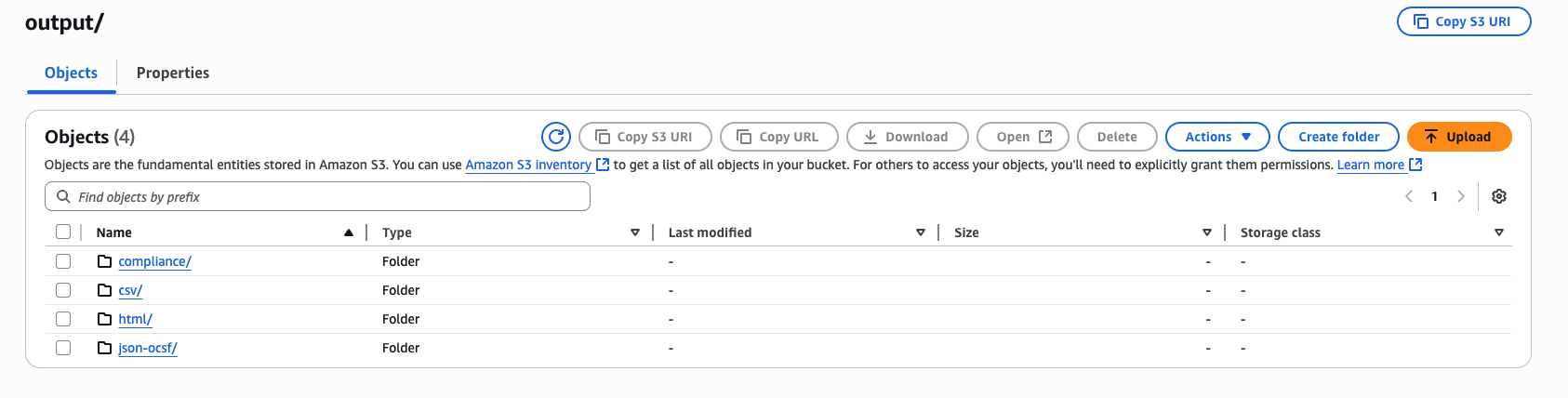
Understanding S3 Export Structure
When the S3 integration is enabled and a scan completes, Prowler creates a folder inside the specified bucket path (usingoutput as the default folder name) with subfolders for each output format:
- Regular:
prowler-output-{provider-uid}-{timestamp}.{extension} - Compliance:
prowler-output-{provider-uid}-{timestamp}_{compliance_framework}.{extension}
Troubleshooting
Connection test fails:- Check AWS credentials are valid
- If using IAM Role, check its permissions
- Verify bucket permissions and region
- Confirm network access to S3
- Ensure integration shows “Connected”
- Check that provider is associated with integration
- Verify bucket policies allow writes

