Deploy Role
The following instructions show how to create the ProwlerProScanRole in your AWS Account using our provided CloudFormation or Terraform template:
Requirements
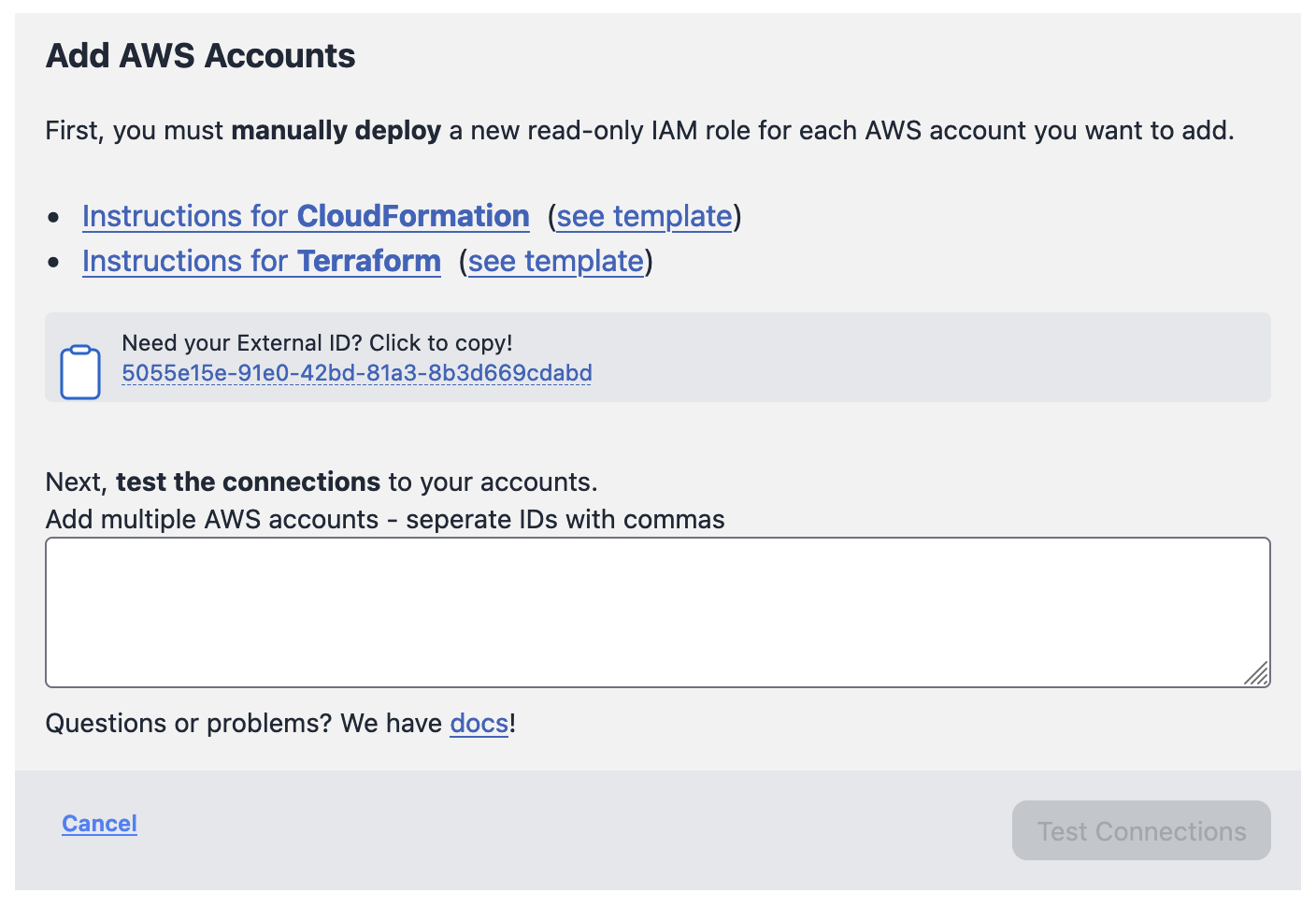
All steps and commands described here will require your Prowler SaaS IAM role External ID. To find this External ID, go to https://app.prowler.pro/app/clouds or click the Cloud menu, and then click the + Add More AWS Accounts link.
In this example, the External ID is 5055e15e-91e0-42bd-81a3-8b3d669cdabd.
Note
When executing the commands below, remember to replace our example ExternalId parameter value with your External ID.
CloudFormation Deployment
Using the AWS CLI
Execute the following AWS CLI command from the AWS account to add to Prowler SaaS:
aws cloudformation create-stack \
--capabilities CAPABILITY_IAM --capabilities CAPABILITY_NAMED_IAM \
--stack-name "ProwlerProSaaSScanRole" \
--template-url "https://s3.eu-west-1.amazonaws.com/prowler-pro-saas-pro-artifacts/templates/prowler-pro-scan-role.yaml" \
--parameters "ParameterKey=ExternalId,ParameterValue=5055e15e-91e0-42bd-81a3-8b3d669cdabd" \
--region us-east-1
Note
Since IAM is a global service, the previous command will work on any region.
Using the AWS Console
To create the ProwlerProScanRole using CloudFormation, please follow these steps:
-
Go to the CloudFormation service in the AWS region used to deploy the ProwlerProScanRole.
-
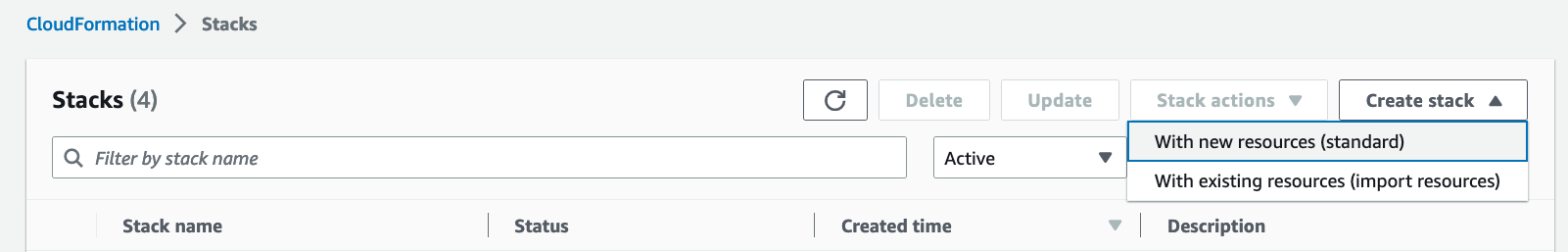
Click on Create Stack and then With new resources (standard):
-
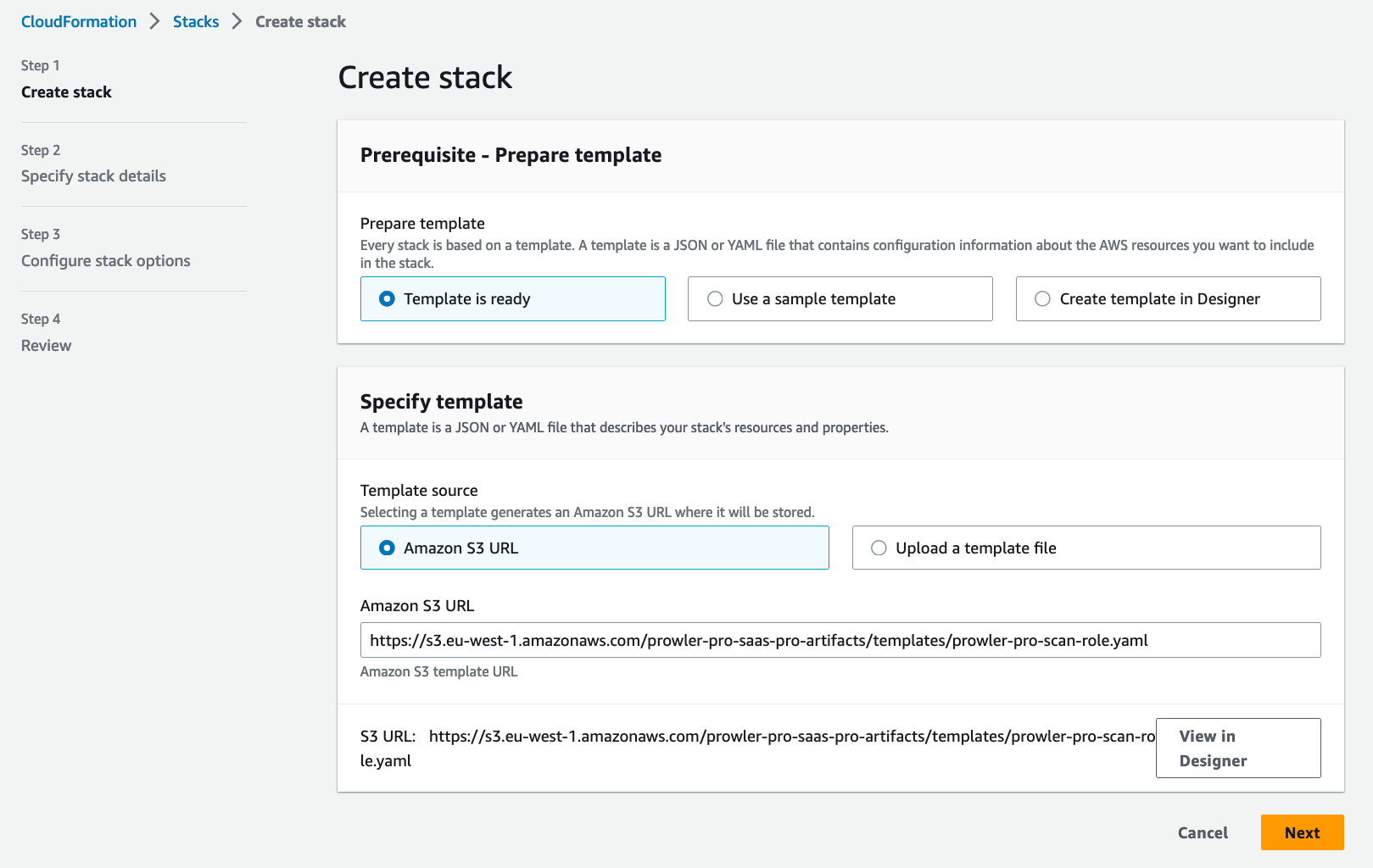
In Create stack section, under Specify template\Template Source select Amazon S3 URL with the provided template https://s3.eu-west-1.amazonaws.com/prowler-pro-saas-pro-artifacts/templates/prowler-pro-scan-role.yaml. Click the Next button.
-
In the Specify stack details section, name the stack
ProwlerProScanRole, then paste theExternalIdvalue where indicated. Click the Next button.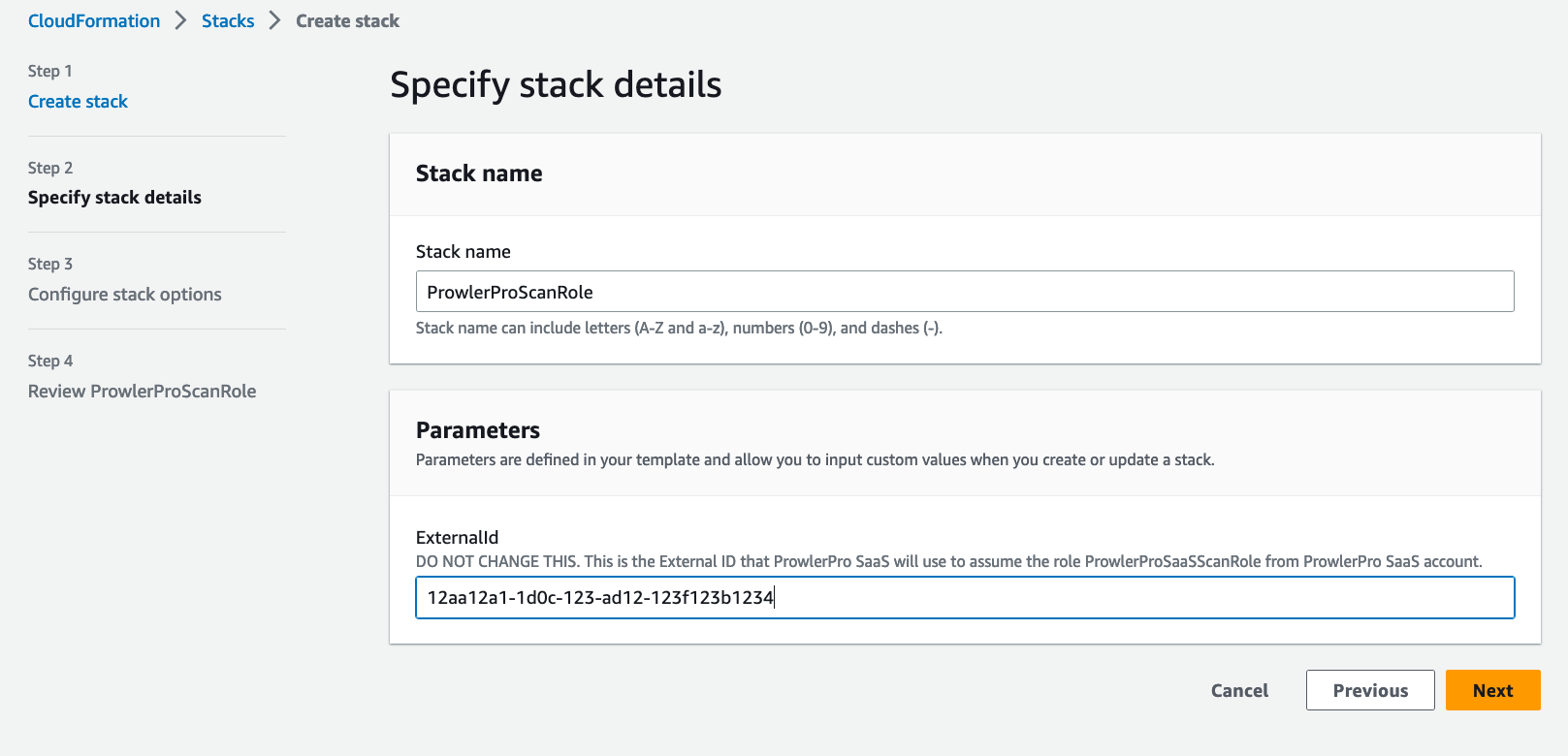
-
In the Configure stack options section, leave everything as is. Click the Next button.
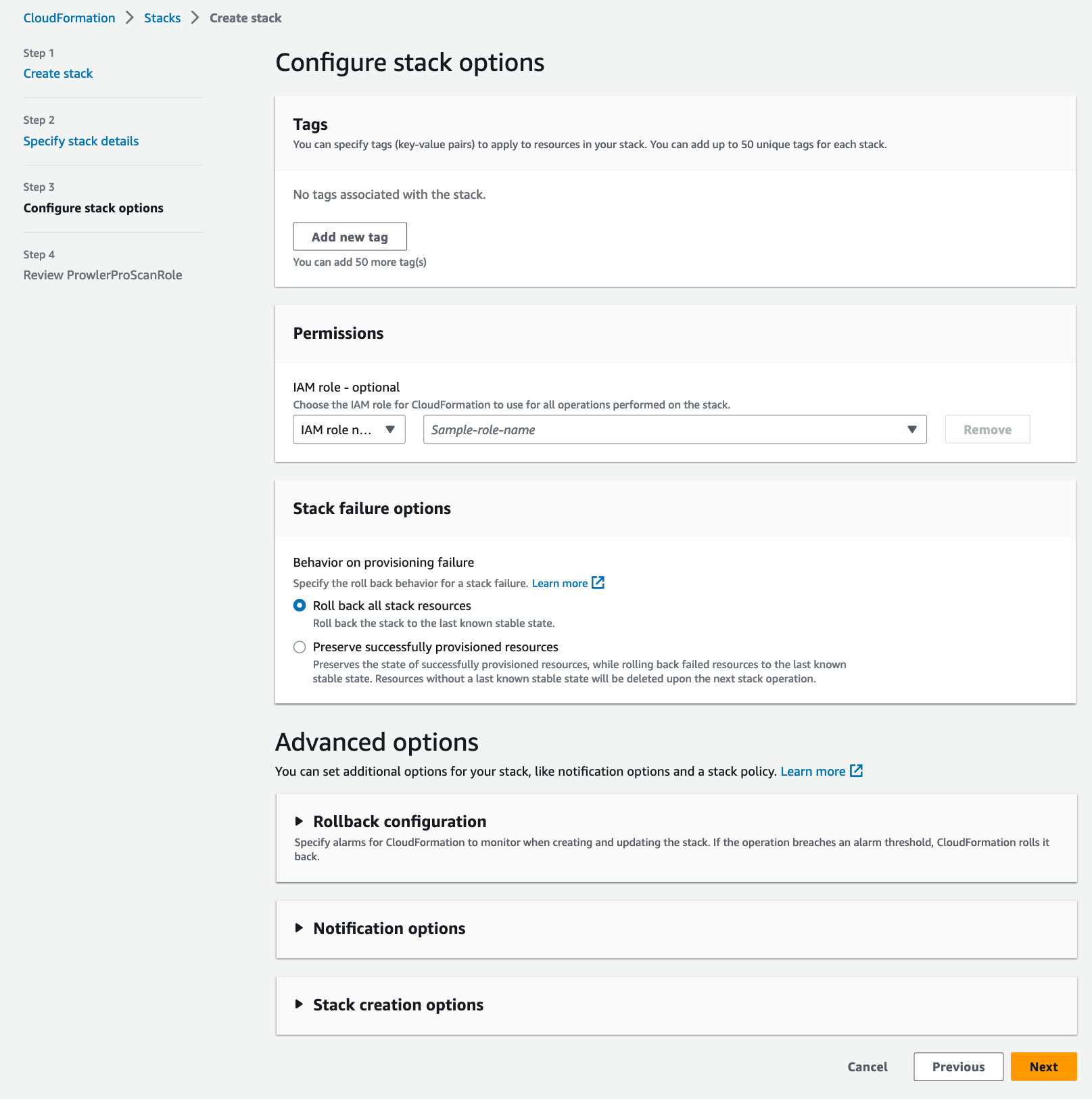
-
Finally, in the Review ProwlerProScanRole\Capabilities section (scroll down if needed), enable the checkbox I acknowledge that AWS CloudFormation might create IAM resouces with custom names. Click the Submit button and your ProwlerProScanRole will be created in your account in a matter of seconds.
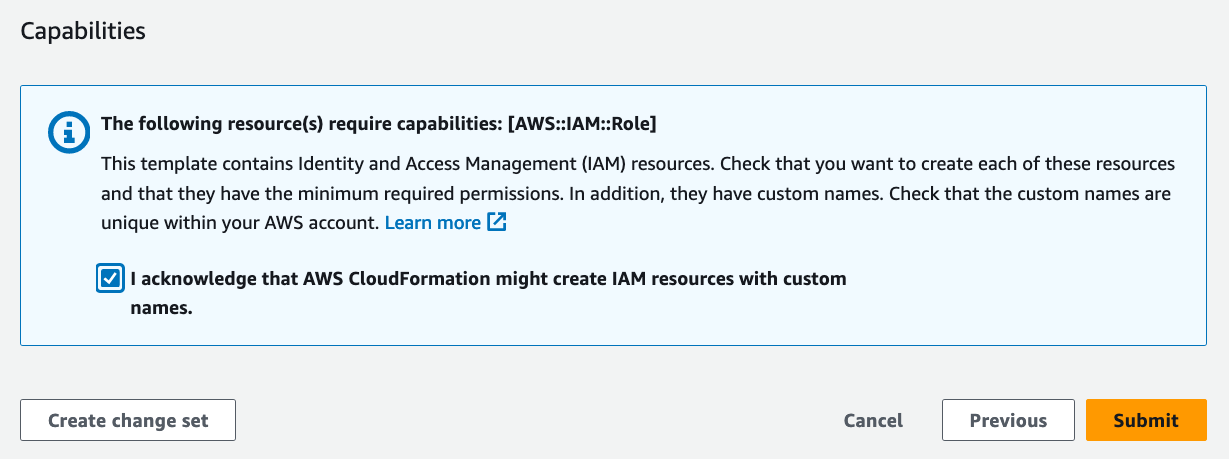
Terraform Deployment
To deploy the ProwlerProScanRole using Terraform, please follow these steps:
-
Get the latest version of the
ProwlerProScanroleTerraform template files, download or clone the repo from here. -
Get into the terraform folder inside the repo folder:
cd prowlerpro-permissions-templates-public/terraform
- Then execute the Terraform commands below:
Note
During the terraform plan and terraform apply steps you need your ExternalId (see steps above on how to find ExternalID)
terraform init
terraform plan
terraform apply
Note
Terraform will use the AWS credentials of your default profile.
CloudFormation Deployment with StackSets
Using the AWS Console
If you are scanning multiple accounts from Prowler SaaS and you have AWS Organizations, the ProwlerProScanRole template can be deployed across all the accounts at once from the AWS Organizations management account using CloudFormation StackSets.
To create the ProwlerProScanRole using CloudFormation StackSets, please follow these steps:
-
Go to the CloudFormation service in the AWS Organizations management account, and choose N. Virginia as the AWS Region.
-
Go to the CloudFormation\StackSets section and then click Create StackSet button:
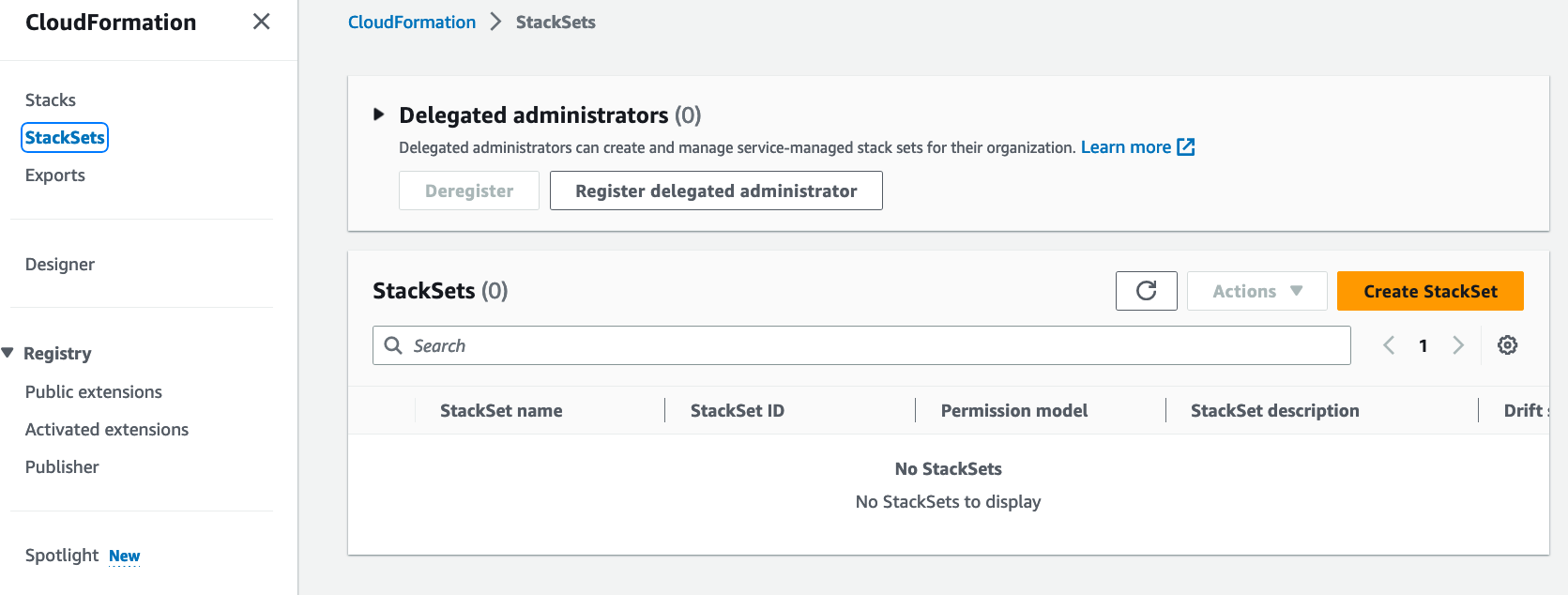
-
In Choose a template section, under Specify template\Template Source select Amazon S3 URL with the provided template https://s3.eu-west-1.amazonaws.com/prowler-pro-saas-pro-artifacts/templates/prowler-pro-scan-role.yaml. Click the Next button.
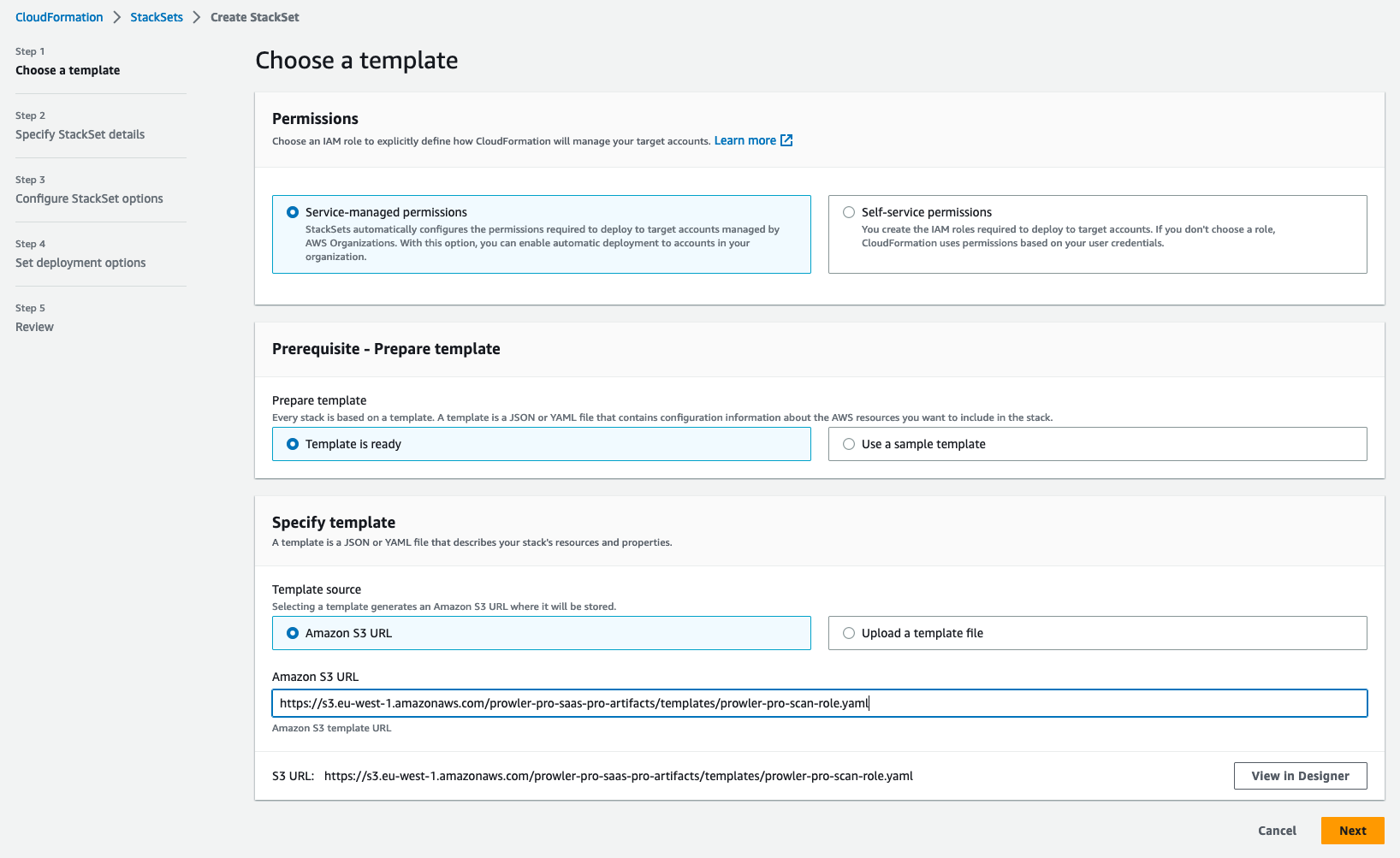
-
In the Specify stack details section, name the stack
ProwlerProScanRole, then paste theExternalIdvalue where indicated. Click the Next button.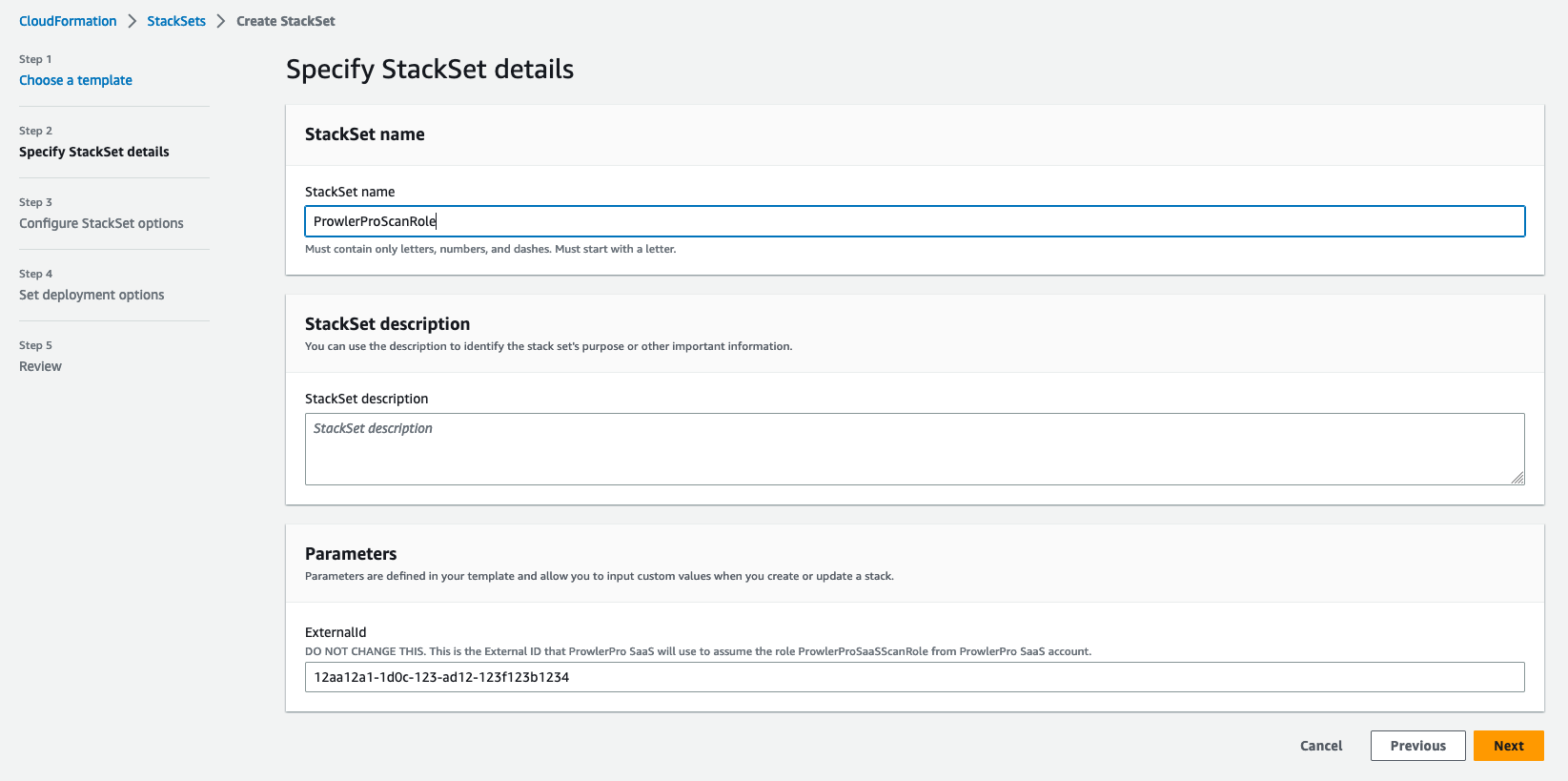
-
In the Configure StackSets options section, leave it as by default or add your custom tags. Click the Next button.
-
In the Set deployment options\Specify regions section, make sure only US East (N. Virginia) is specified.
-
In the Deployment options\Region Concurrency select Parallel. Click the Next button.
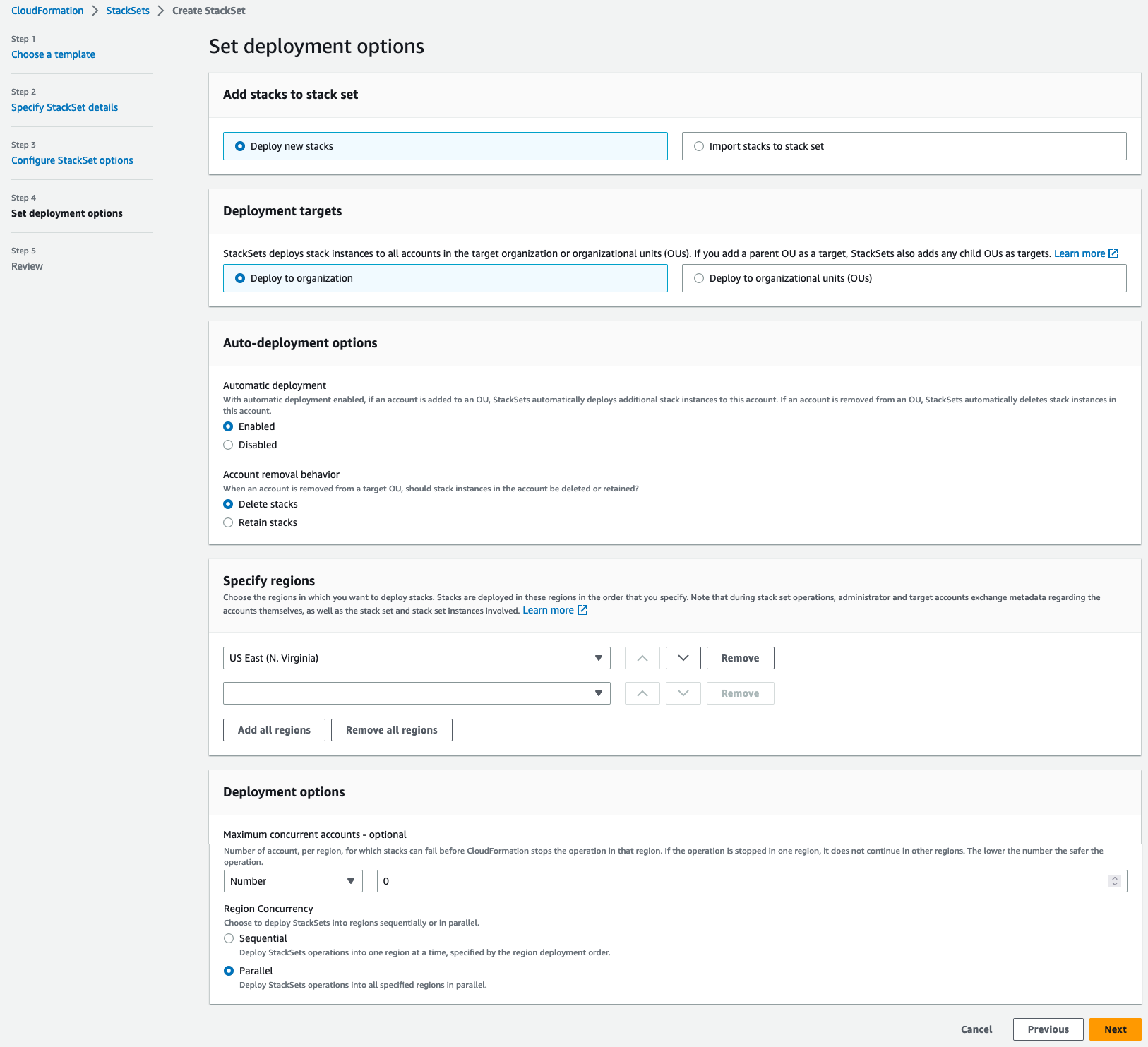
-
In the Configure stack options section, leave everything as it is. Click the Next button.
-
Finally, in the Review ProwlerProScanRole\Capabilities section (scroll down if needed), enable the checkbox I acknowledge that AWS CloudFormation might create IAM resouces with custom names, then click the Submit button and your ProwlerProScanRole will be created in your account in a matter of seconds.

CloudFormation Quick Link
If you are using CloudFormation to deploy the ProwlerProScanRole and you want to add more accounts into Prowler SaaS, the following CloudFormation quick link could be useful if you have the session opened in the Console for the AWS account you want to add.
AWS CloudFormation Quick Link to deploy the ProwlerProScanRole
Note
You will need to input your ExternalId (see steps above on how to find ExternalID).