- JSON-OCSF:
status_idisSuppressed. - CSV:
mutedisTrue. The fieldstatuswill keep the original status,MANUAL,PASSorFAIL, of the finding.
How the Mutelist Works
The Mutelist uses AND logic to evaluate whether a finding should be muted. For a finding to be muted, ALL of the following conditions must match:- Account matches (exact match or
*) - Check matches (exact match, regex pattern, or
*) - Region matches (exact match, regex pattern, or
*) - Resource matches (exact match, regex pattern, or
*) - Tags match (if specified)
Tag Matching Logic
Tags have special matching behavior:-
Multiple tags in the list = AND logic: ALL tags must be present on the resource
-
Regex alternation within a single tag = OR logic: Use the pipe operator
|for OR -
Complex tag patterns: Combine AND and OR using regex
Remember that mutelist can be used with regular expressions.
Mutelist Specification
- For Azure provider, the Account ID is the Subscription Name and the Region is the Location.
- For GCP provider, the Account ID is the Project ID and the Region is the Zone.
- For Kubernetes provider, the Account ID is the Cluster Name and the Region is the Namespace.
Account, Check, Region, Resource, and Tag
| Field | Description | Logic |
|---|---|---|
account_id | Use * to apply the mutelist to all accounts. Supports exact match or wildcard. | AND (with other fields) |
check_name | The name of the Prowler check. Use * to apply the mutelist to all checks, or service_* to apply it to all service’s checks. Supports regex patterns. | AND (with other fields) |
region | The region identifier. Use * to apply the mutelist to all regions. Supports regex patterns. | AND (with other fields) |
resource | The resource identifier. Use * to apply the mutelist to all resources. Supports regex patterns. | AND (with other fields) |
tags | List of tag patterns in key=value format. Multiple tags = AND (all must match). Regex alternation within single tag = OR (use tag1|tag2). | AND between tags, OR within regex |
Description
This field can be used to add information or some hints for the Mutelist rule.How to Use the Mutelist
To use the Mutelist, you need to specify the path to the Mutelist YAML file using the-w or --mutelist-file option when running Prowler:
<provider> with the appropriate provider name.
Considerations
- The Mutelist can be used in combination with other Prowler options, such as the
--serviceor--checksoption, to further customize the scanning process. - Make sure to review and update the Mutelist regularly to ensure it reflects the desired exclusions and remains up to date with your infrastructure.
Current Limitations and Workarounds
Limitation: No OR Logic Between Different Rule Sets
The current Mutelist schema does not support OR logic between different condition sets. Each check can have only one rule object, and all conditions are ANDed together. Example of unsupported scenario:Limitation: Cannot Negate Regions
You cannot express “all regions except X and Y”. You must explicitly list all regions you want to mute. Workaround:Best Practices
-
Use regex patterns for flexibility: Instead of listing multiple resources, use regex patterns like
"dev-.*"or"test-instance-[0-9]+" -
Combine tag OR logic with regex: Use
"environment=dev|environment=stg|environment=test"instead of multiple tag entries -
Be specific with exceptions: Use the
Exceptionsfield to unmute specific resources within a broader muting rule -
Test your mutelist: Run Prowler with
--output-modes jsonand verify that the expected findings are muted
AWS Mutelist
Muting specific AWS regions
If you want to mute failed findings only in specific regions, create a file with the following syntax and run it withprowler aws -w mutelist.yaml:
Mutelist:
Accounts:
"":
Checks:
"":
Regions:
- “ap-southeast-1”
- “ap-southeast-2” Resources:
- ”*” Description: “Description related with the muted findings for the check”
Default Mutelist
For the AWS Provider, Prowler is executed with a default AWS Mutelist with the AWS Resources that should be muted such as all resources created by AWS Control Tower when setting up a landing zone that can be found in AWS Documentation. You can see this Mutelist file inprowler/config/aws_mutelist.yaml.
Supported Mutelist Locations
The mutelisting flag supports the following AWS locations when using the AWS Provider:AWS S3 URI
You will need to pass the S3 URI where your Mutelist YAML file was uploaded to your bucket:Make sure that the used AWS credentials have
s3:GetObject permissions in the S3 path where the mutelist file is located.AWS DynamoDB Table ARN
You will need to pass the DynamoDB Mutelist Table ARN:
-
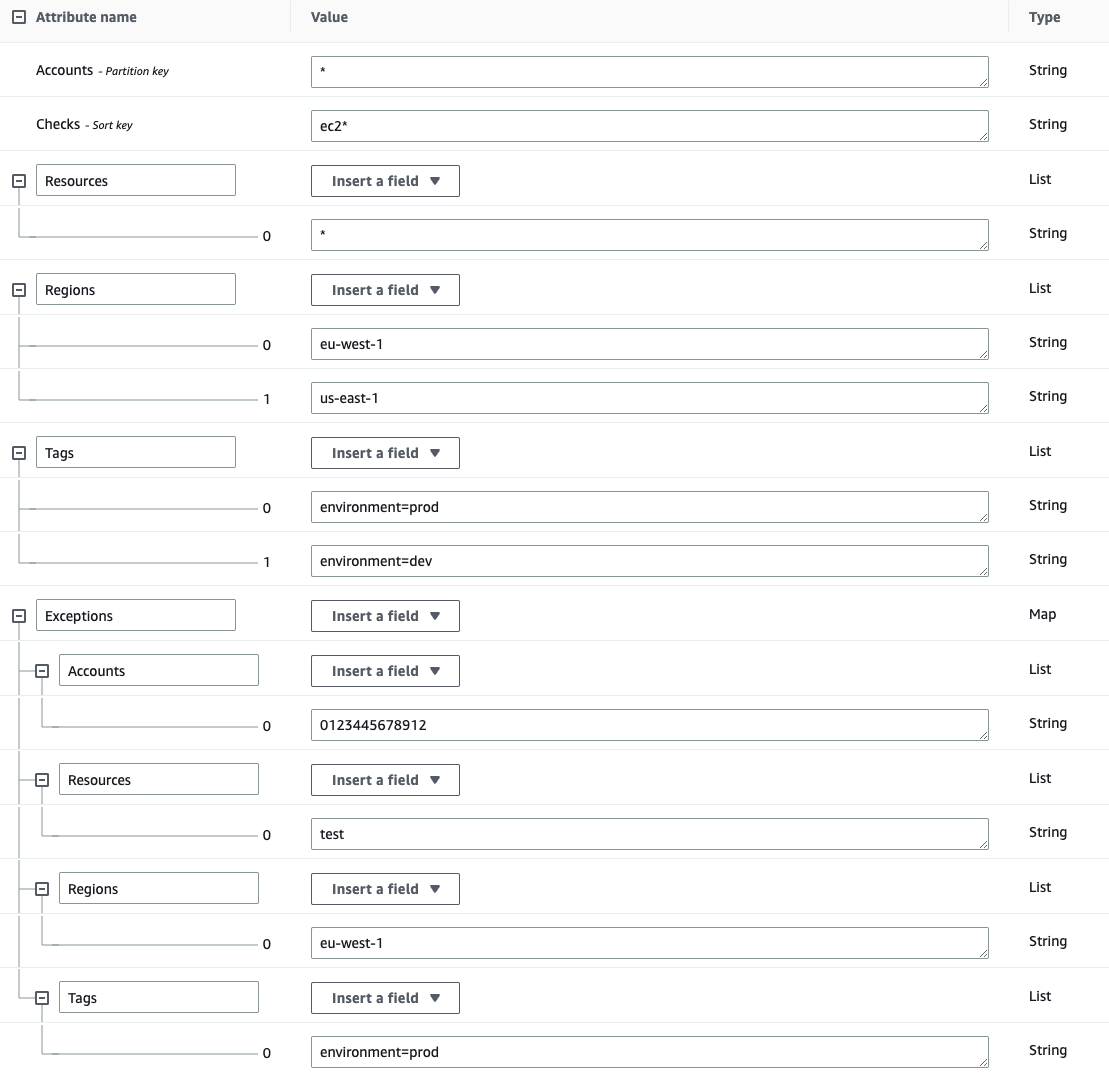
Accounts (String): This field can contain either an Account ID or an
*(which applies to all the accounts that use this table as an mutelist). -
Checks (String): This field can contain either a Prowler Check Name or an
*(which applies to all the scanned checks). -
Regions (List): This field contains a list of regions where this mutelist rule is applied (it can also contains an
*to apply all scanned regions). - Resources (List): This field contains a list of regular expressions (regex) that applies to the resources that are wanted to be muted.
- Tags (List): -Optional- This field contains a list of tuples in the form of ‘key=value’ that applies to the resources tags that are wanted to be muted.
- Exceptions (Map): -Optional- This field contains a map of lists of accounts/regions/resources/tags that are wanted to be excepted in the mutelist.
eu-west-1 and us-east-1 with the tags environment=dev and environment=prod, except the resources containing the string test in the account 012345678912 and region eu-west-1 with the tag environment=prod:
Make sure that the used AWS credentials have
dynamodb:PartiQLSelect permissions in the table.
