Added in: 5.9.0
Prowler App allows users to mute specific findings to focus on the most critical security issues. This guide demonstrates how to use the Advanced Mutelist feature with YAML configuration for complex, pattern-based muting rules.
For muting individual findings without YAML configuration, use Simple Mutelist to mute findings directly from the Findings table. What Is Advanced Mutelist?
Advanced Mutelist enables users to create powerful, pattern-based muting rules using YAML configuration:
- Define complex muting patterns using regular expressions
- Mute findings by check, region, resource, or tag across multiple accounts
- Apply wildcards to mute entire categories of findings
- Create exceptions within broad muting rules
- Maintain audit trails of muted findings for compliance purposes
Prerequisites
Before muting findings, ensure:
- Valid access to Prowler App with appropriate permissions
- A provider added to the Prowler App
- Understanding of the security implications of muting specific findings
Muting findings does not resolve underlying security issues. Review each finding carefully before muting to ensure it represents an acceptable risk or has been properly addressed.
Step 1: Connect a Provider
To configure Advanced Mutelist:
- Log into Prowler App
- Navigate to the Providers page
- Connect a provider to enable Mutelist configuration
- Navigate to the Mutelist page from the left navigation menu
- Select the “Advanced” tab
- Provide a valid Mutelist configuration in
YAML format
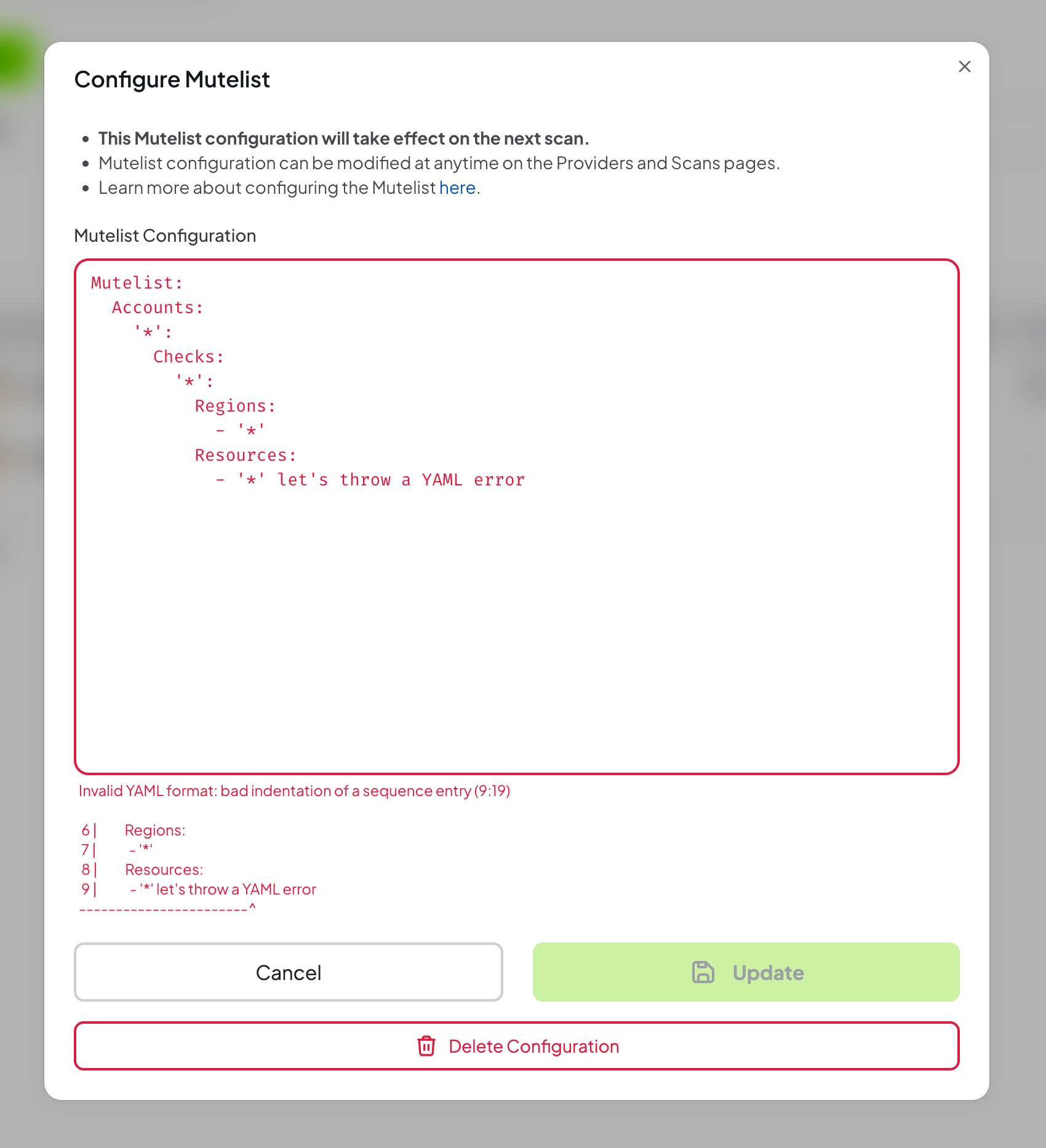
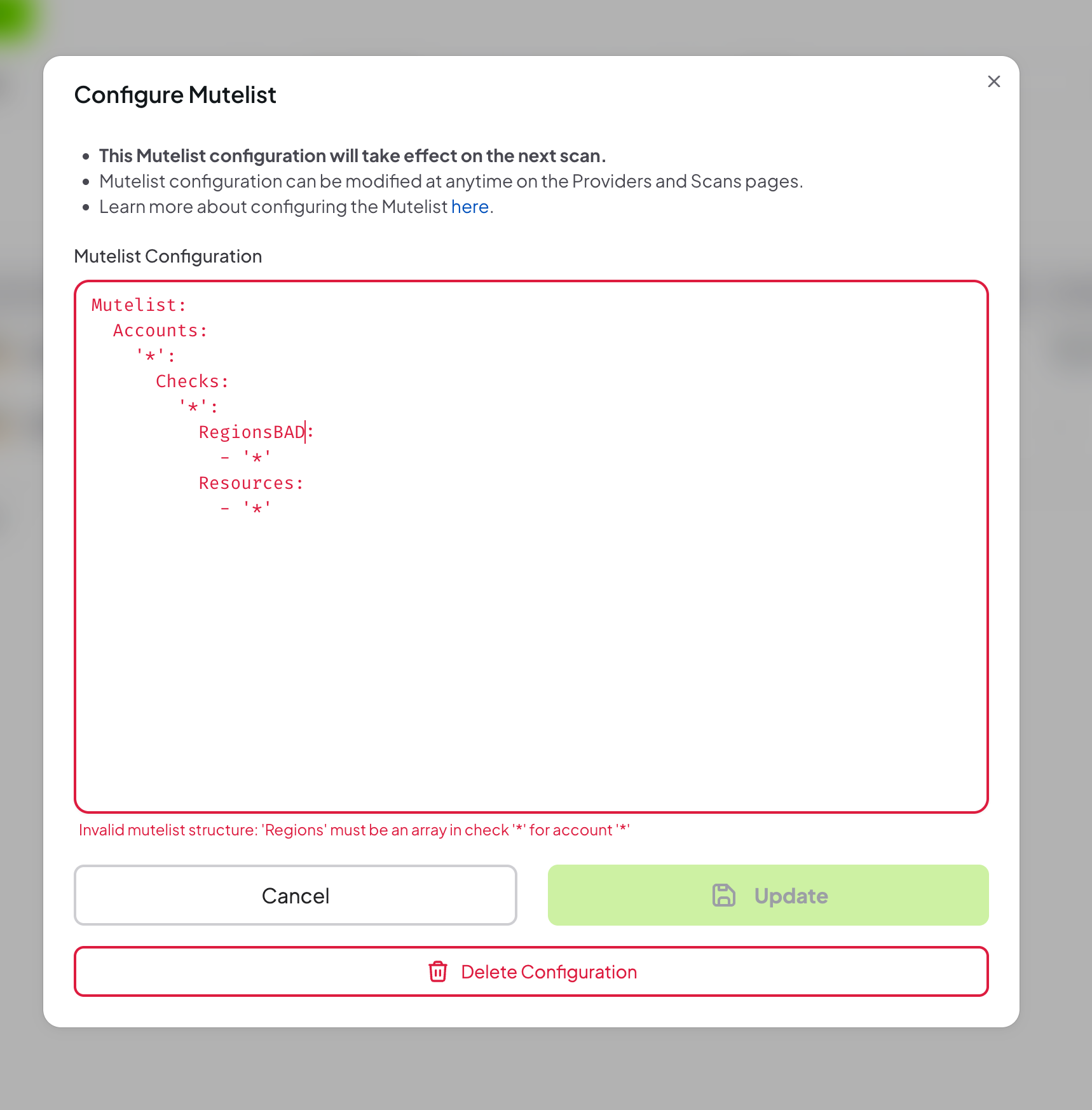
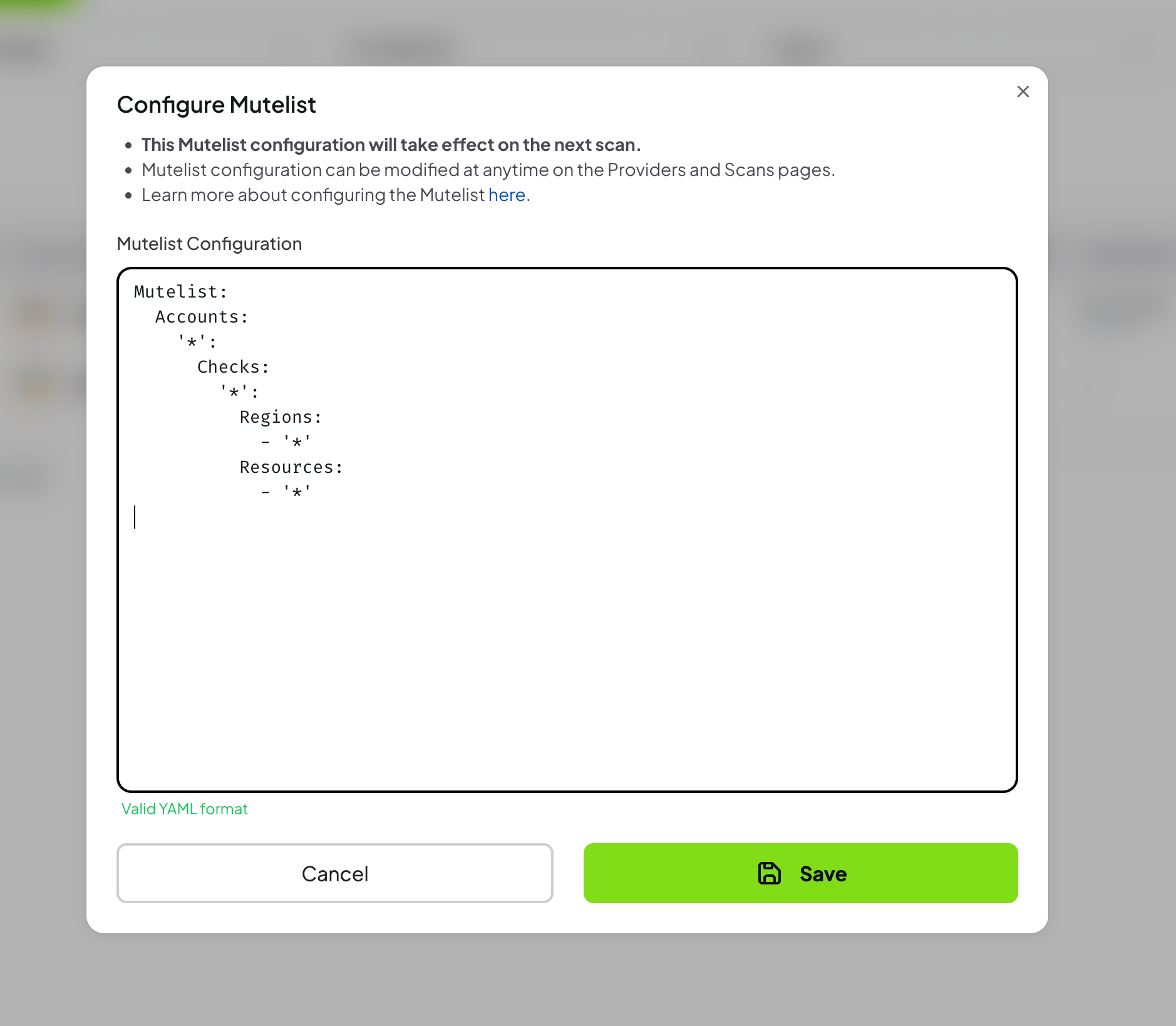 If the YAML configuration is invalid, an error message will be displayed
If the YAML configuration is invalid, an error message will be displayed
Step 3: Review and Update the Configuration
- Once added, the configuration can be updated or removed from the Advanced tab
Step 4: Verify Muted Findings in Scan Results
- Run a new scan
- Navigate to the Findings page to verify muted findings
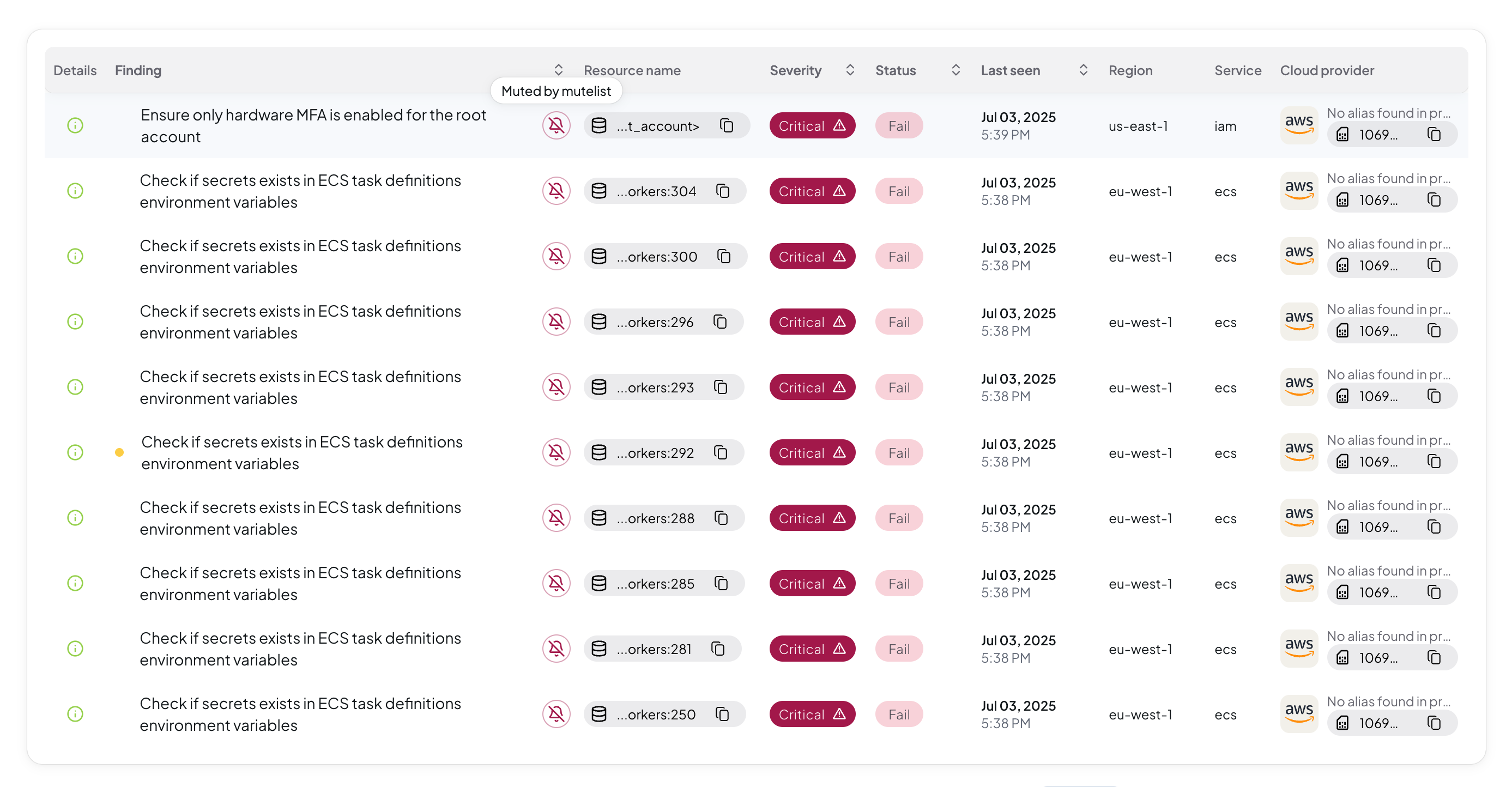
The Advanced Mutelist configuration takes effect on subsequent scans. Existing findings are not retroactively muted.
YAML Configuration Examples
Below are ready-to-use examples for different cloud providers. For detailed syntax and logic explanation, see CLI Mutelist documentation.
AWS Provider
Basic AWS Mutelist
Mutelist:
Accounts:
"123456789012":
Checks:
"iam_user_hardware_mfa_enabled":
Regions:
- "us-east-1"
Resources:
- "user-1"
- "user-2"
Description: "Mute MFA findings for specific users in us-east-1"
"s3_bucket_public_access":
Regions:
- "*"
Resources:
- "public-website-bucket"
Description: "Mute public access findings for website bucket"
AWS Service-Wide Muting
Mutelist:
Accounts:
"*":
Checks:
"ec2_*":
Regions:
- "*"
Resources:
- "*"
Description: "Mute all EC2-related findings across all accounts and regions"
AWS Tag-Based Muting
Mutelist:
Accounts:
"*":
Checks:
"*":
Regions:
- "*"
Resources:
- "*"
Tags:
- "environment=dev"
- "project=test"
Description: "Mute all findings for resources tagged with environment=dev or project=test"
Azure Provider
For Azure provider, the Account ID is the Subscription Name and the Region is the Location.
Basic Azure Mutelist
Mutelist:
Accounts:
"MySubscription":
Checks:
"storage_blob_public_access_level_is_disabled":
Regions:
- "East US"
- "West US"
Resources:
- "publicstorageblob"
Description: "Mute public access findings for specific blob storage resource"
"app_function_vnet_integration_enabled":
Regions:
- "*"
Resources:
- "app-vnet-peering-*"
Description: "Mute App Function Vnet findings related with the reources pattern"
Azure Resource Group Muting
Mutelist:
Accounts:
"*":
Checks:
"*":
Regions:
- "*"
Resources:
- "rg-dev-*"
- "rg-test-*"
Tags:
- "environment=development"
Description: "Mute all findings for development resource groups"
GCP Provider
For GCP provider, the Account ID is the Project ID and the Region is the Zone.
Basic GCP Mutelist
Mutelist:
Accounts:
"my-gcp-project":
Checks:
"cloudstorage_bucket_public_access":
Regions:
- "us-central1"
- "us-east1"
Resources:
- "public-bucket-*"
Description: "Mute public access findings for specific bucket pattern"
"compute_instance_public_ip":
Regions:
- "*"
Resources:
- "public-instance"
Description: "Mute public access findings for specific compute instance"
GCP Project-Wide Muting
Mutelist:
Accounts:
"*":
Checks:
"*":
Regions:
- "*"
Resources:
- "*"
Tags:
- "environment=staging"
Description: "Mute all GCP findings for staging environment"
Kubernetes Provider
For Kubernetes provider, the Account ID is the Cluster Name and the Region is the Namespace.
Basic Kubernetes Mutelist
Mutelist:
Accounts:
"my-cluster":
Checks:
"etcd_client_cert_auth":
Regions:
- "default"
- "kube-system"
Resources:
- "system-pod-*"
Description: "Mute etcd cert authorization findings for the matching resources"
"kubelet_tls_cert_and_key":
Regions:
- "*"
Resources:
- "*"
Description: "Mute kubelet tls findings across all namespaces"
Kubernetes Namespace Muting
Mutelist:
Accounts:
"*":
Checks:
"*":
Regions:
- "monitoring"
- "logging"
Resources:
- "*"
Description: "Mute all findings for monitoring and logging namespaces"
Microsoft 365 Provider
Basic Microsoft 365 Mutelist
Mutelist:
Accounts:
"my-tenant.onmicrosoft.com":
Checks:
"entra_admin_portals_access_restriction":
Regions:
- "*"
Resources:
- "test-user"
Description: "Mute findings related with administrative roles access for test-user"
"sharepoint_external_sharing_managed":
Regions:
- "*"
Resources:
- "public-site-*"
Description: "Mute external sharing findings for public sites"
Microsoft 365 Tenant-Wide Muting
Mutelist:
Accounts:
"*":
Checks:
"*":
Regions:
- "*"
Resources:
- "*"
Tags:
- "department=IT"
Description: "Mute all M365 findings for IT department resources"
Multi-Cloud Mutelist
You can combine multiple providers in a single mutelist configuration:
Mutelist:
Accounts:
# AWS Account
"123456789012":
Checks:
"s3_bucket_public_access":
Regions:
- "us-east-1"
Resources:
- "public-website"
Description: "Mute public access findings for AWS website bucket"
# Azure Subscription
"MyAzureSubscription":
Checks:
"storage_blob_public_access_level_is_disabled":
Regions:
- "East US"
Resources:
- "public-storage"
Description: "Mute public access findings for Azure storage account"
# GCP Project
"my-gcp-project":
Checks:
"cloudstorage_bucket_public_access":
Regions:
- "us-central1"
Resources:
- "public-bucket"
Description: "Mute public access findings for GCP storage bucket"
# Kubernetes Cluster
"my-k8s-cluster":
Checks:
"kubelet_tls_cert_and_key":
Regions:
- "default"
Resources:
- "kubelet-test"
Description: "Mute kubelet tls findings related with kubelet-test"
# Microsoft 365 Tenant
"my-tenant.onmicrosoft.com":
Checks:
"sharepoint_external_sharing_managed":
Regions:
- "*"
Resources:
- "public-site"
Description: "Mute external sharing findings for public SharePoint site"
Advanced Mutelist Features
Using Regular Expressions
Mutelist:
Accounts:
"*":
Checks:
"*":
Regions:
- "*"
Resources:
- ".*-test-.*" # Matches any resource containing "-test-"
- "dev-.*" # Matches resources starting with "dev-"
- ".*-prod$" # Matches resources ending with "-prod"
Description: "Mute findings for test and development resources using regex"
Using Exceptions
Mutelist:
Accounts:
"*":
Checks:
"*":
Regions:
- "*"
Resources:
- "*"
Exceptions:
Accounts:
- "987654321098"
Regions:
- "us-west-2"
Resources:
- "critical-resource"
Tags:
- "environment=production"
Description: "Mute all findings except for critical production resources"
Tag-Based Logic
Mutelist:
Accounts:
"*":
Checks:
"*":
Regions:
- "*"
Resources:
- "*"
Tags:
- "environment=dev | environment=test" # OR logic
- "project=alpha" # AND logic
Description: "Mute findings for dev/test environments in alpha project"
Best Practices
- Start Small: Begin with specific resources and gradually expand
- Document Reasons: Always include descriptions for audit trails
- Regular Reviews: Periodically review muted findings
- Use Tags: Leverage resource tags for better organization
- Test Changes: Validate mutelist changes in non-production environments
- Monitor Impact: Track how muting affects your security posture
Validation
Prowler App validates your mutelist configuration and will display errors for:
- Invalid YAML syntax
- Missing required fields
- Invalid regular expressions
- Unsupported provider-specific configurations









