- User Credentials (Application Default Credentials)
- Service Account Key File
- Access Token
- Service Account Impersonation
Required Permissions
Prowler for Google Cloud requires the following permissions:IAM Roles
- Viewer (
roles/viewer) – Must be granted at the project, folder, or organization level to allow scanning of target projects. - Service Usage Consumer (
roles/serviceusage.serviceUsageConsumer) IAM Role – Required for resource scanning. - Custom
ProwlerRole– Include granular permissions that are not included in the Viewer role:storage.buckets.getIamPolicy
Project-Level Settings
At least one project must have the following configurations:-
Identity and Access Management (IAM) API (
iam.googleapis.com) – Must be enabled via:- The Google Cloud API UI, or
- The
gcloudCLI:
-
Service Usage Consumer (
roles/serviceusage.serviceUsageConsumer) IAM Role – Required for resource scanning. -
Quota Project Setting – Define a quota project using either:
- The
gcloudCLI:
- Setting an environment variable:
- The
Prowler will scan the GCP project associated with the credentials.
Application Default Credentials (User Credentials)
This method uses the Google Cloud CLI to authenticate and is suitable for development and testing environments.Setup Application Default Credentials
-
In the GCP Console, click on “Activate Cloud Shell”
-
Click “Authorize Cloud Shell”
-
Run the following command:
- Type
Ywhen prompted
- Type
-
Open the authentication URL provided in a browser and select your Google account
-
Follow the steps to obtain the authentication code
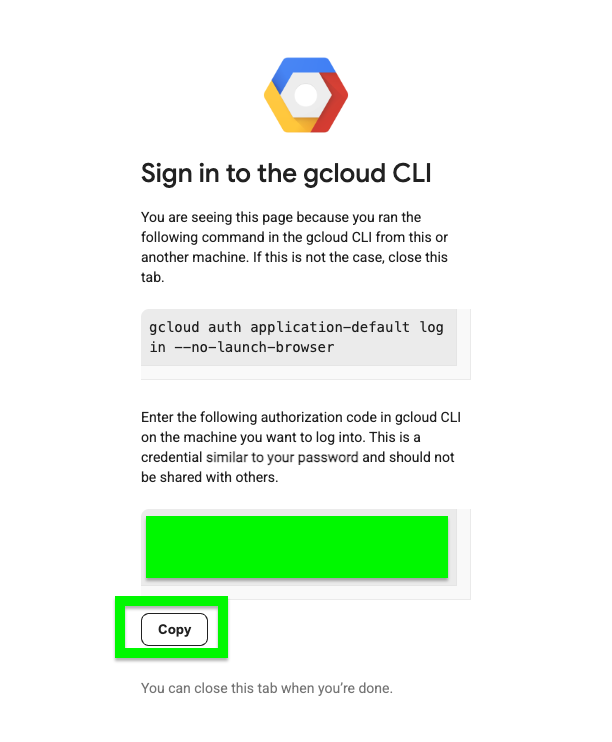
-
Paste the authentication code back in Cloud Shell
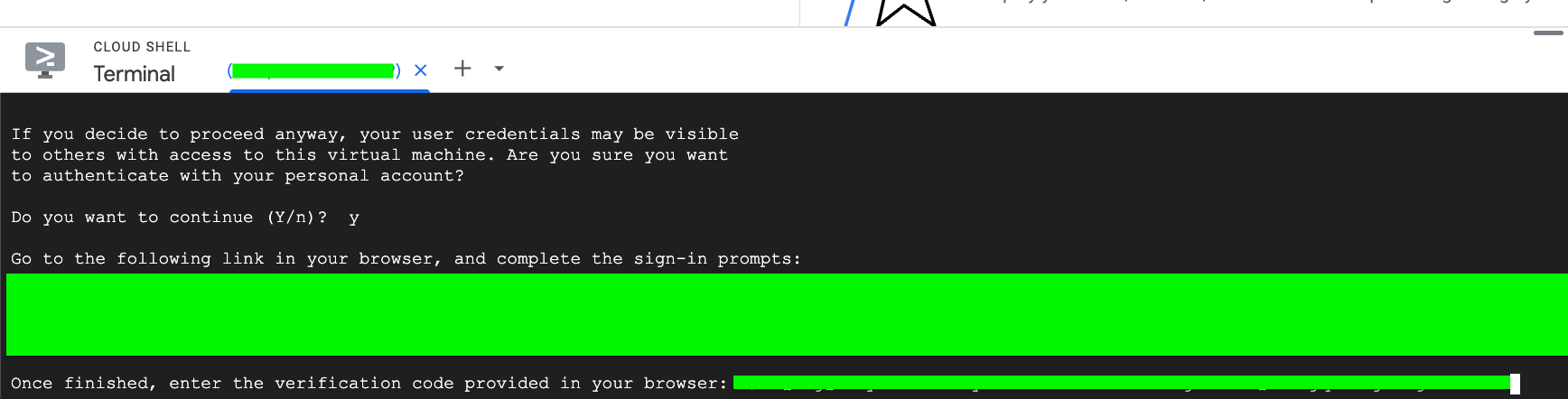
-
Use
cat <file_name>to view the temporary credentials file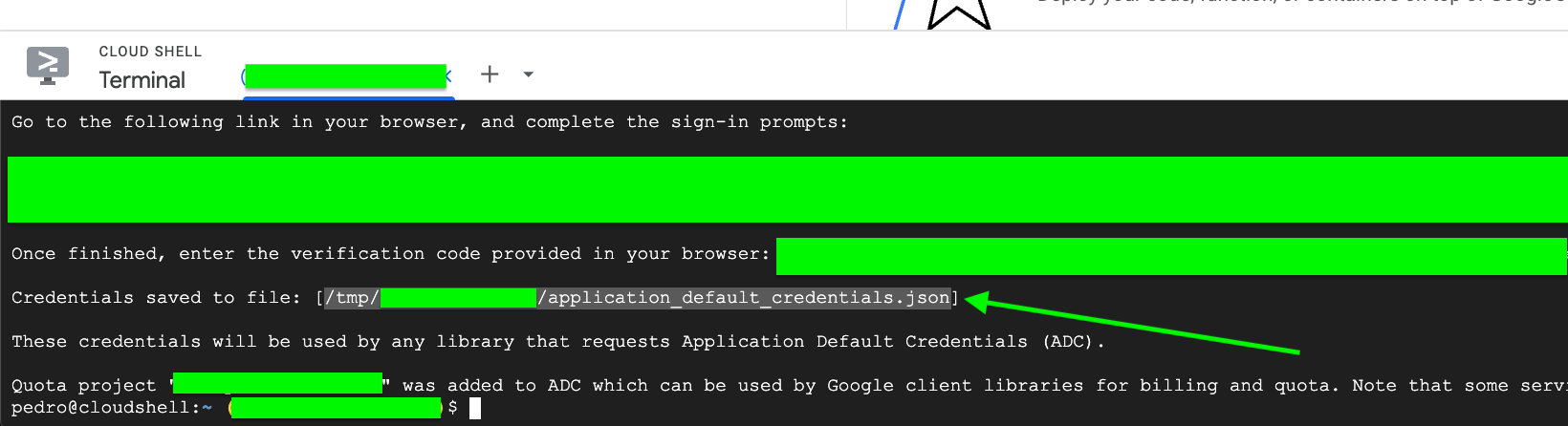
-
Extract the following values for Prowler Cloud/App:
client_idclient_secretrefresh_token
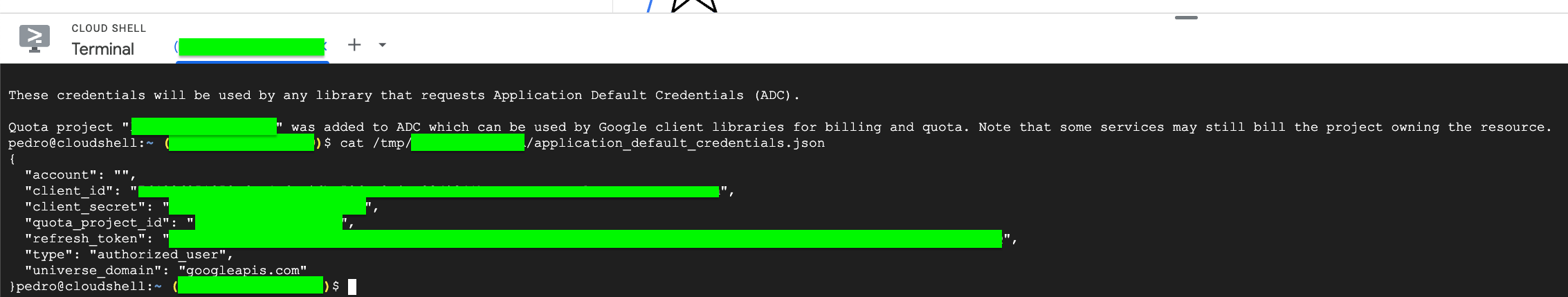
Using with Prowler CLI
Once application default credentials are set up, run Prowler directly:Service Account Key File
This method uses a service account with a downloaded key file for authentication.Step 1: Create ProwlerRole
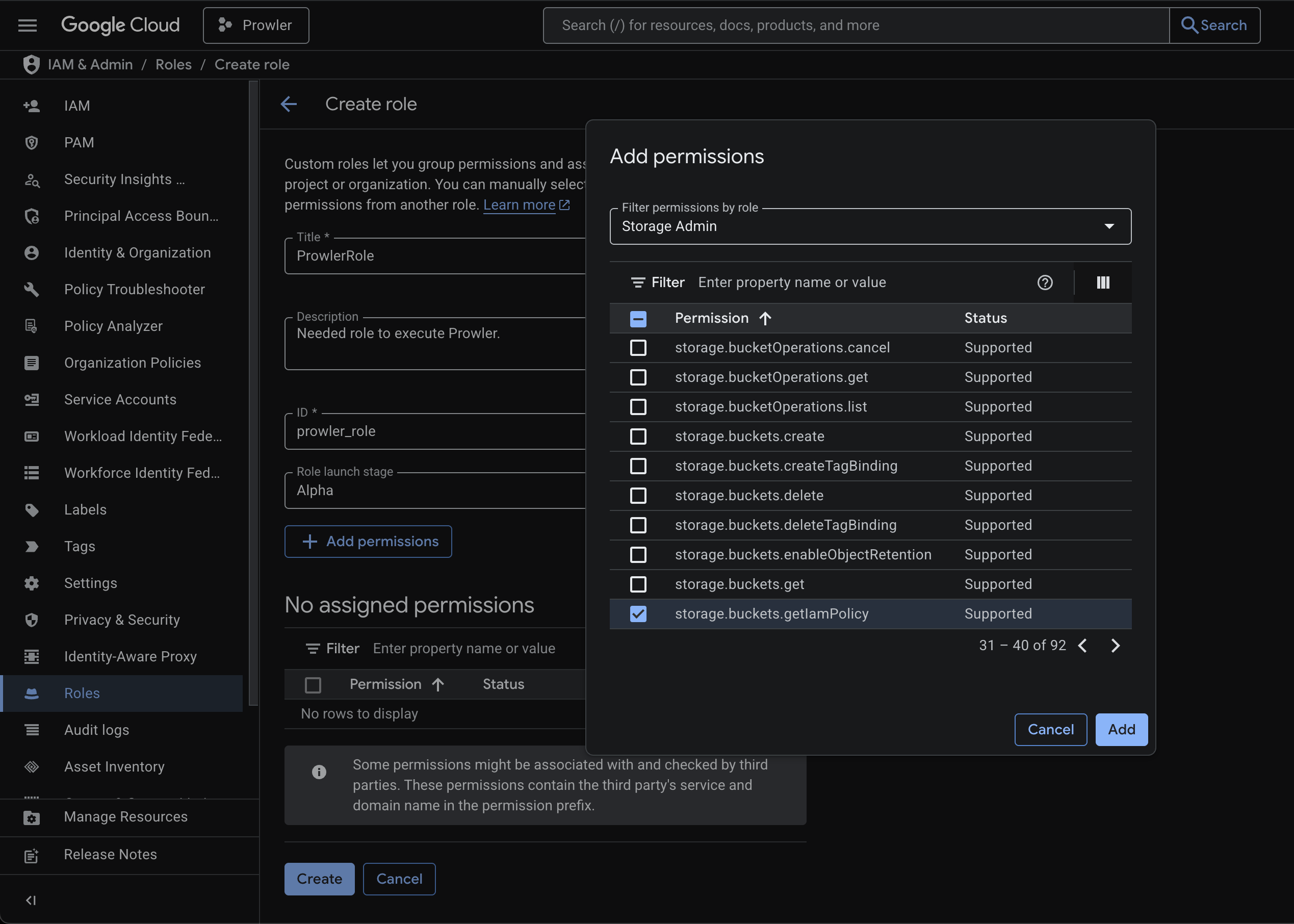
To keep permissions focused:- Create a custom role named ProwlerRole that explicitly includes the permissions your compliance team approves. Click Create role, set the title to ProwlerRole, keep the ID readable (for example,
prowler_role) - Add the required permission
storage.buckets.getIamPolicy(the permission highlighted in the screenshots). To make it easier, filter the permissions byStorage Adminrole.
Step 2: Create the Service Account
-
Navigate to IAM & Admin > Service Accounts and make sure the correct project is selected.
-
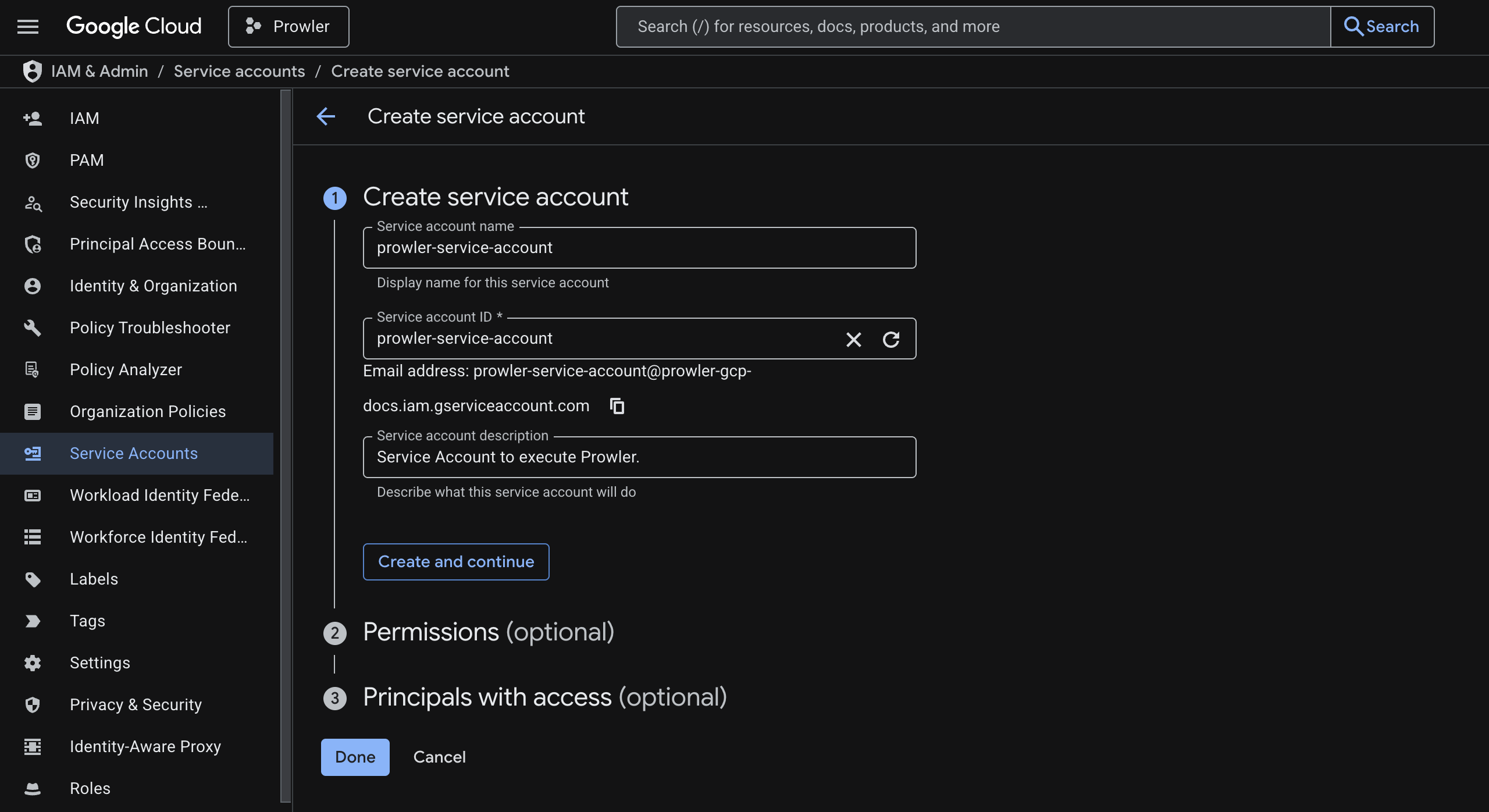
Select Create service account, provide a name, ID, and a short description that states the purpose (for example, “Service account to execute Prowler”), then click Create and continue.
-
Assign the roles you prepared earlier:
- ProwlerRole for
cloudstorageservice checks. - Viewer for broad read-only visibility.
- Service Usage Consumer so Prowler can inspect API states.
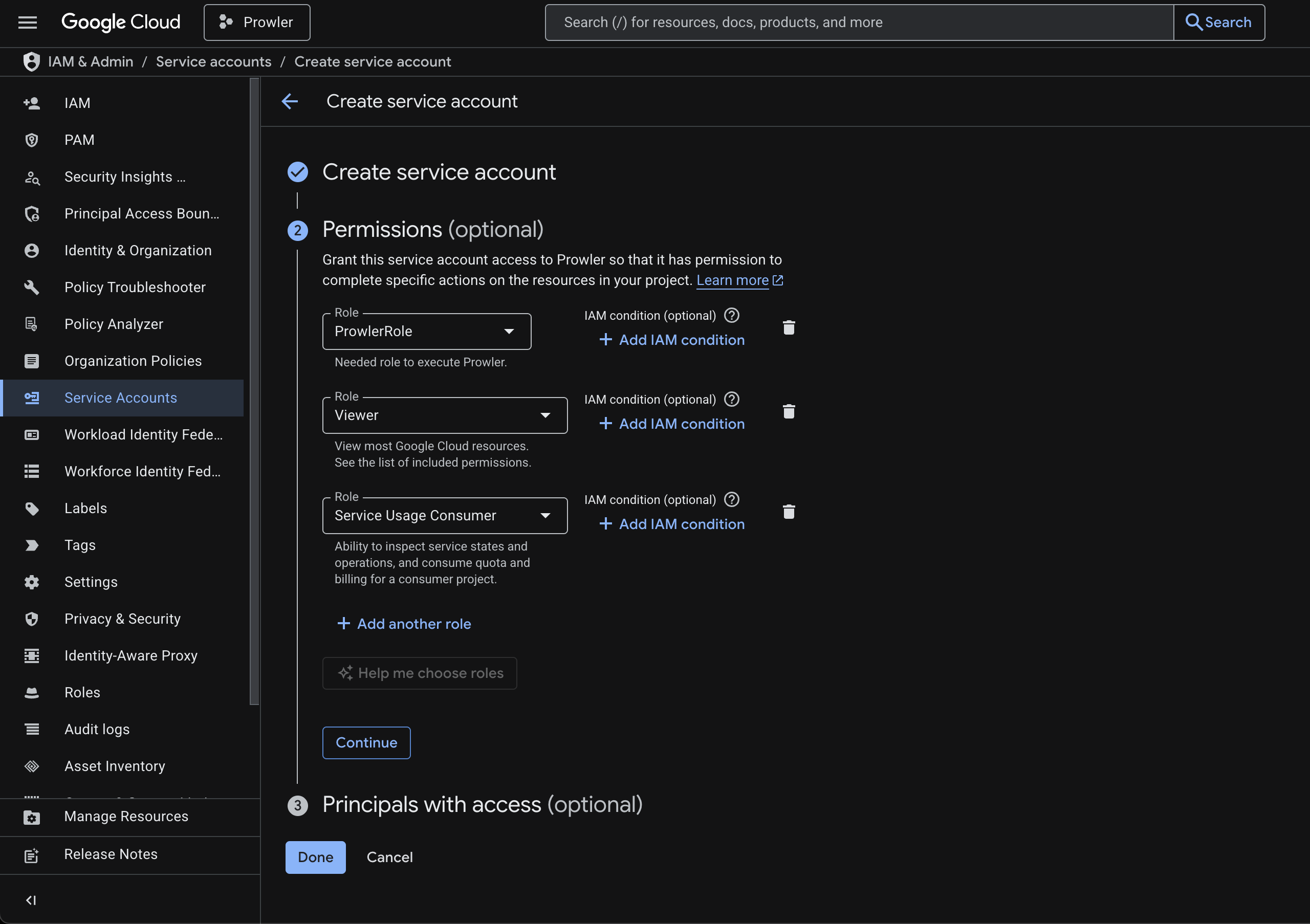
- ProwlerRole for
- Continue through the wizard and finish. No principals need to be granted access in step 3 unless you want other identities to impersonate this account.
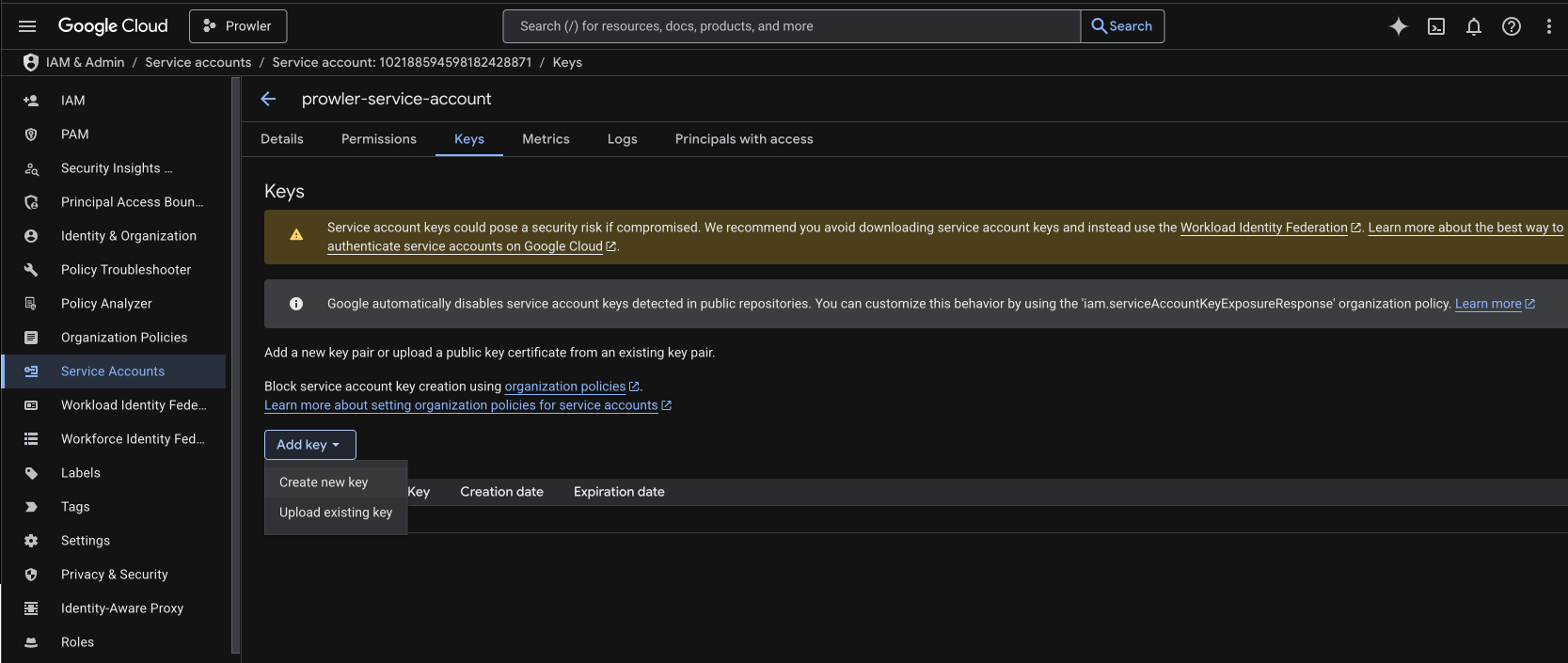
Step 3: Generate a JSON Key
-
Open the newly created service account, move to the Keys tab, and choose Add key > Create new key.
-
Select JSON as the key type and click Create. The browser downloads the file exactly once.
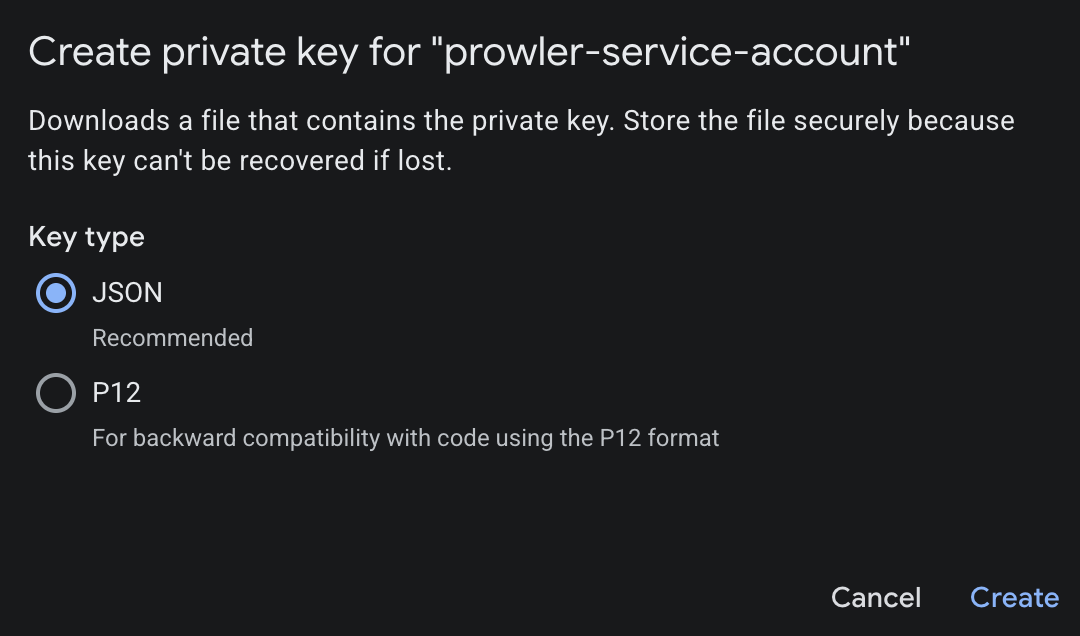
- Once created, make sure to store the Key securely.
Using with Prowler CLI
Set theGOOGLE_APPLICATION_CREDENTIALS environment variable:
Access Token
For existing access tokens (e.g., generated withgcloud auth print-access-token), run Prowler with:
When using this method, also set the default project explicitly:
Service Account Impersonation
To impersonate a GCP service account, use the--impersonate-service-account argument followed by the service account email:
Prerequisites for Impersonation
The identity running Prowler must have the following permission on the target service account:roles/iam.serviceAccountTokenCreator
iam.serviceAccounts.generateAccessToken

