- Static Credentials
- Assumed Role
Required Permissions
To ensure full functionality, attach the following AWS managed policies to the designated user or role:arn:aws:iam::aws:policy/SecurityAuditarn:aws:iam::aws:policy/job-function/ViewOnlyAccess
Additional Permissions
For certain checks, additional read-only permissions are required. Attach the following custom policy to your role: prowler-additions-policy.jsonAssume Role (Recommended)
This method grants permanent access and is the recommended setup for production environments.- CloudFormation
- Terraform
-
Download the Prowler Scan Role Template
-
Open the AWS Console, search for CloudFormation
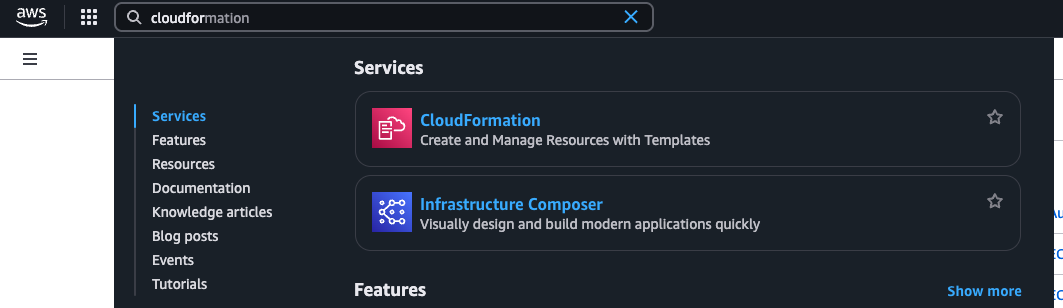
-
Go to Stacks and click “Create stack” > “With new resources (standard)”
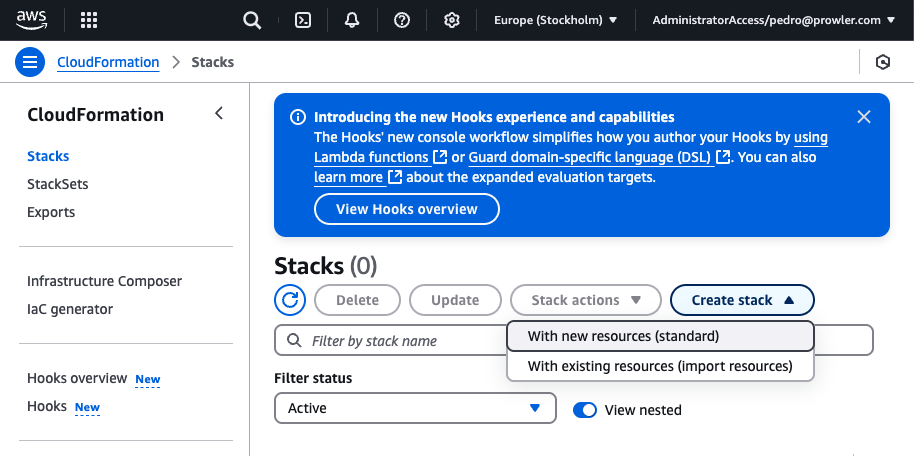
-
In Specify Template, choose “Upload a template file” and select the downloaded file
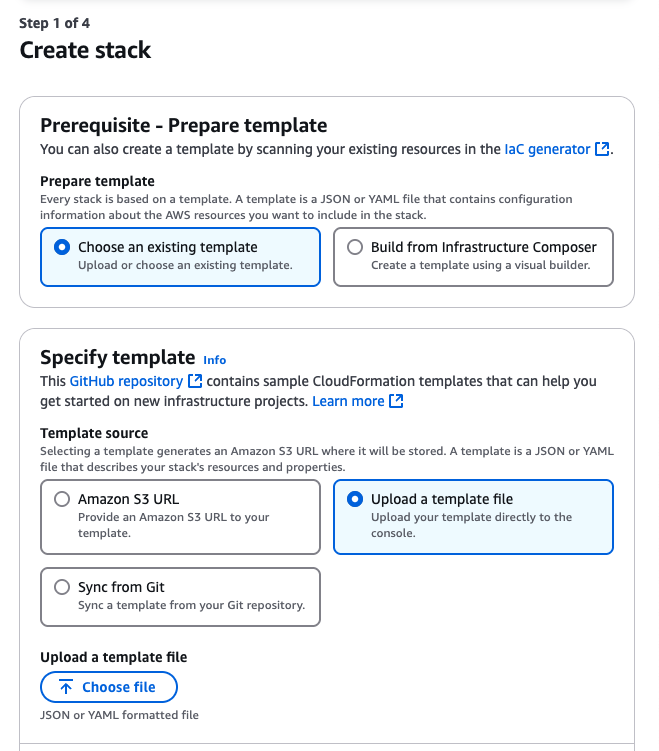

-
Click “Next”, provide a stack name and the External ID shown in the Prowler Cloud setup screen
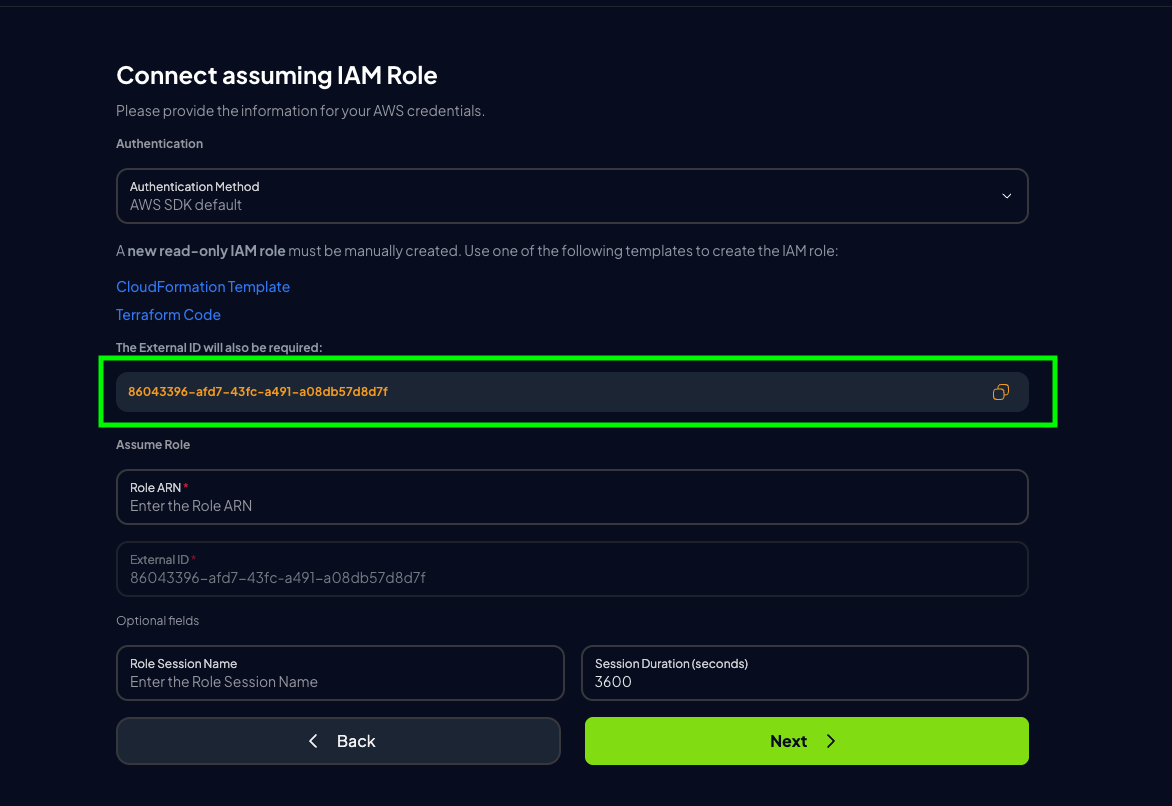
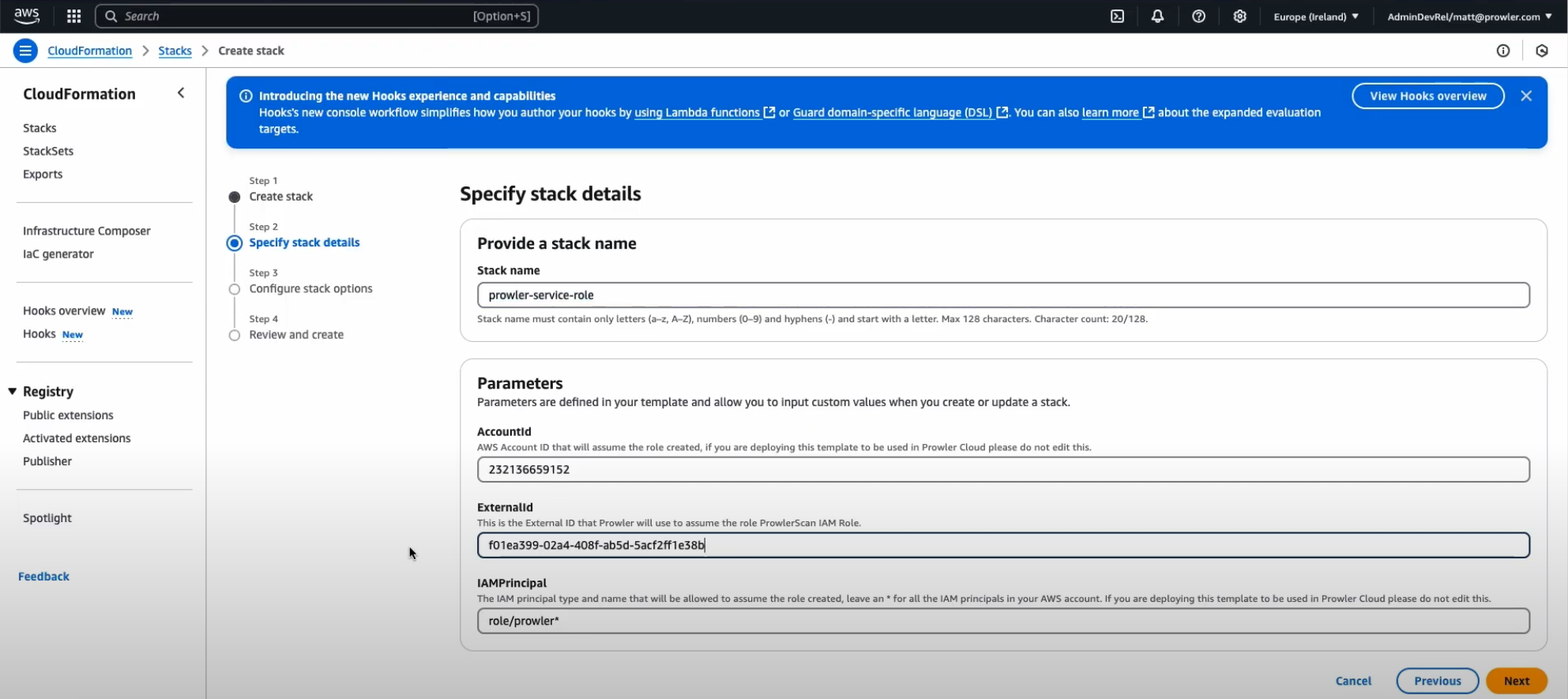 An External ID is required when assuming the ProwlerScan role to prevent the confused deputy problem.
An External ID is required when assuming the ProwlerScan role to prevent the confused deputy problem. -
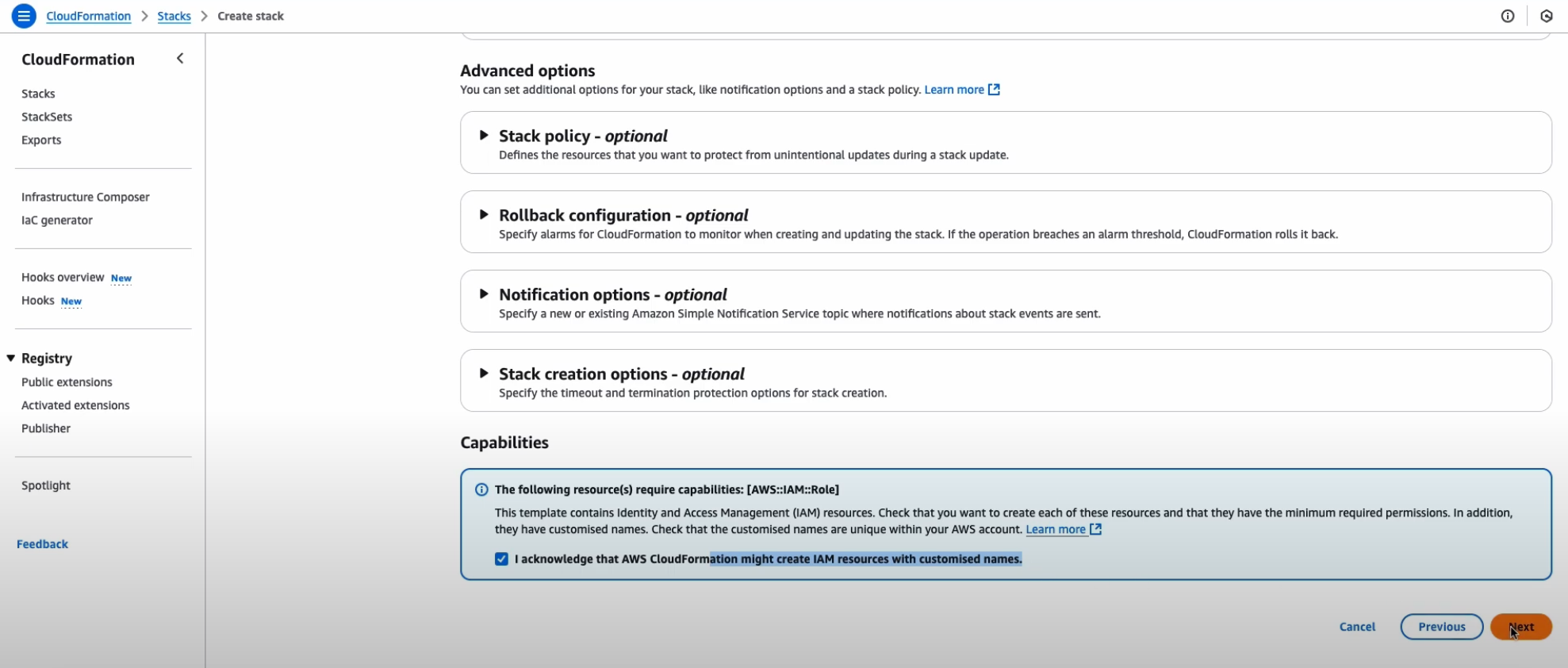
Acknowledge the IAM resource creation warning and proceed
-
Click “Submit” to deploy the stack
Credentials
- Long term credentials
- Short term credentials (Recommended)
-
Go to the AWS Console, open CloudShell

-
Run:

