Added in: 5.9.0
This guide provides comprehensive instructions to configure SAML-based Single Sign-On (SSO) in Prowler App. This configuration allows users to authenticate using the organization’s Identity Provider (IdP).
This document is divided into two main sections:
- User Guide: For organization administrators to configure SAML SSO through Prowler App.
- Developer and Administrator Guide: For developers and system administrators running self-hosted Prowler App instances, providing technical details on environment configuration, API usage, and testing.
User Guide Configuration
Follow these steps to enable and configure SAML SSO for an organization.Key Features
Prowler can be integrated with SAML SSO identity providers such as Okta to enable single sign-on for the organization’s users. The Prowler SAML integration currently supports the following features:- IdP-Initiated SSO: Users can initiate login from their Identity Provider’s dashboard.
- SP-Initiated SSO: Users can initiate login directly from the Prowler login page.
- Just-in-Time Provisioning: Users from the organization signing into Prowler for the first time will be automatically created.
Prerequisites
- Administrator access to the Prowler organization is required.
- Administrative access to the SAML 2.0 compliant Identity Provider (e.g., Okta, Azure AD, Google Workspace) is necessary.
Configuration Steps
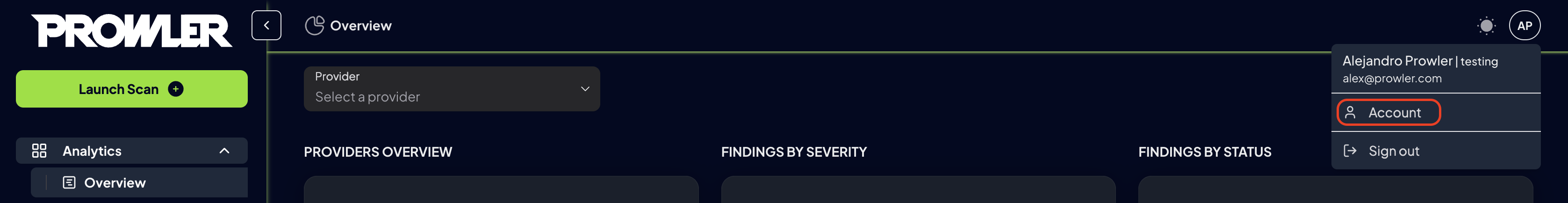
Step 1: Access Profile Settings
To access the account settings, click the “Account” button in the top-right corner of Prowler App, or navigate directly tohttps://cloud.prowler.com/profile (or http://localhost:3000/profile for local setups).
Step 2: Enable SAML Integration
On the profile page, find the “SAML SSO Integration” card and click “Enable” to begin the configuration process.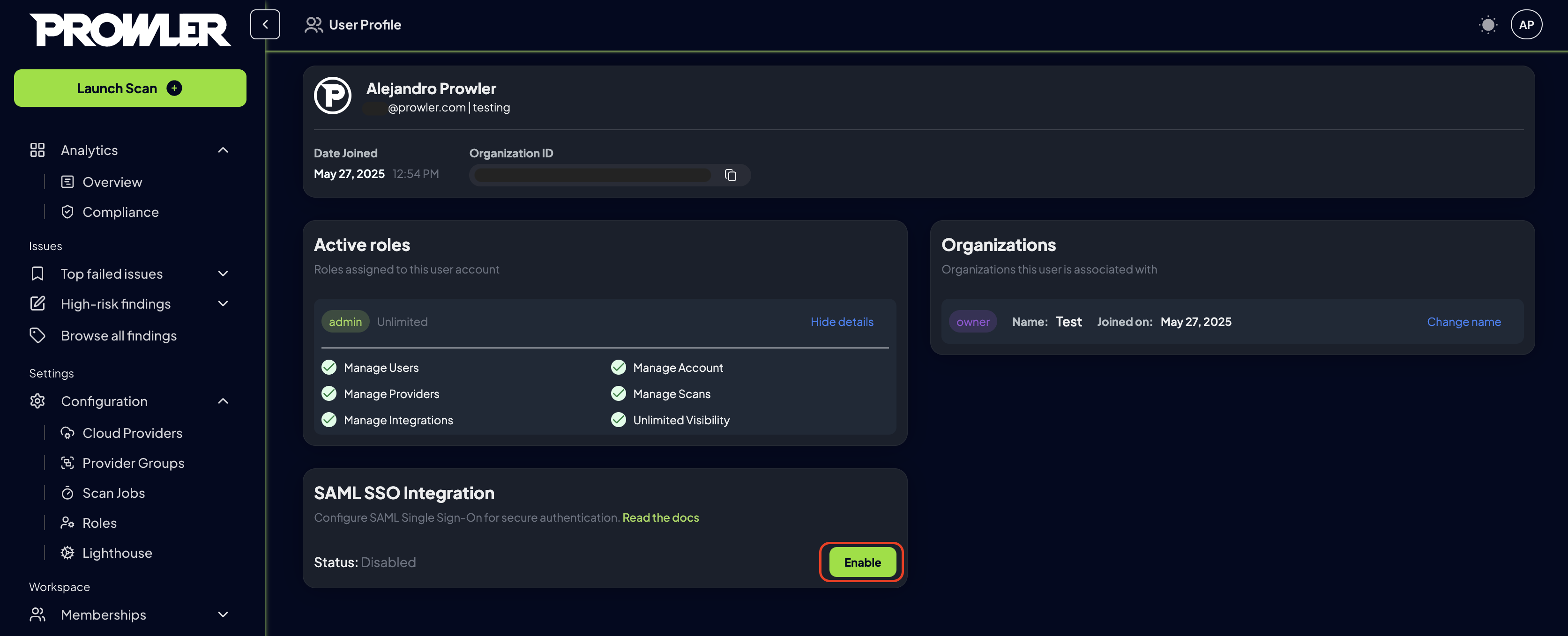
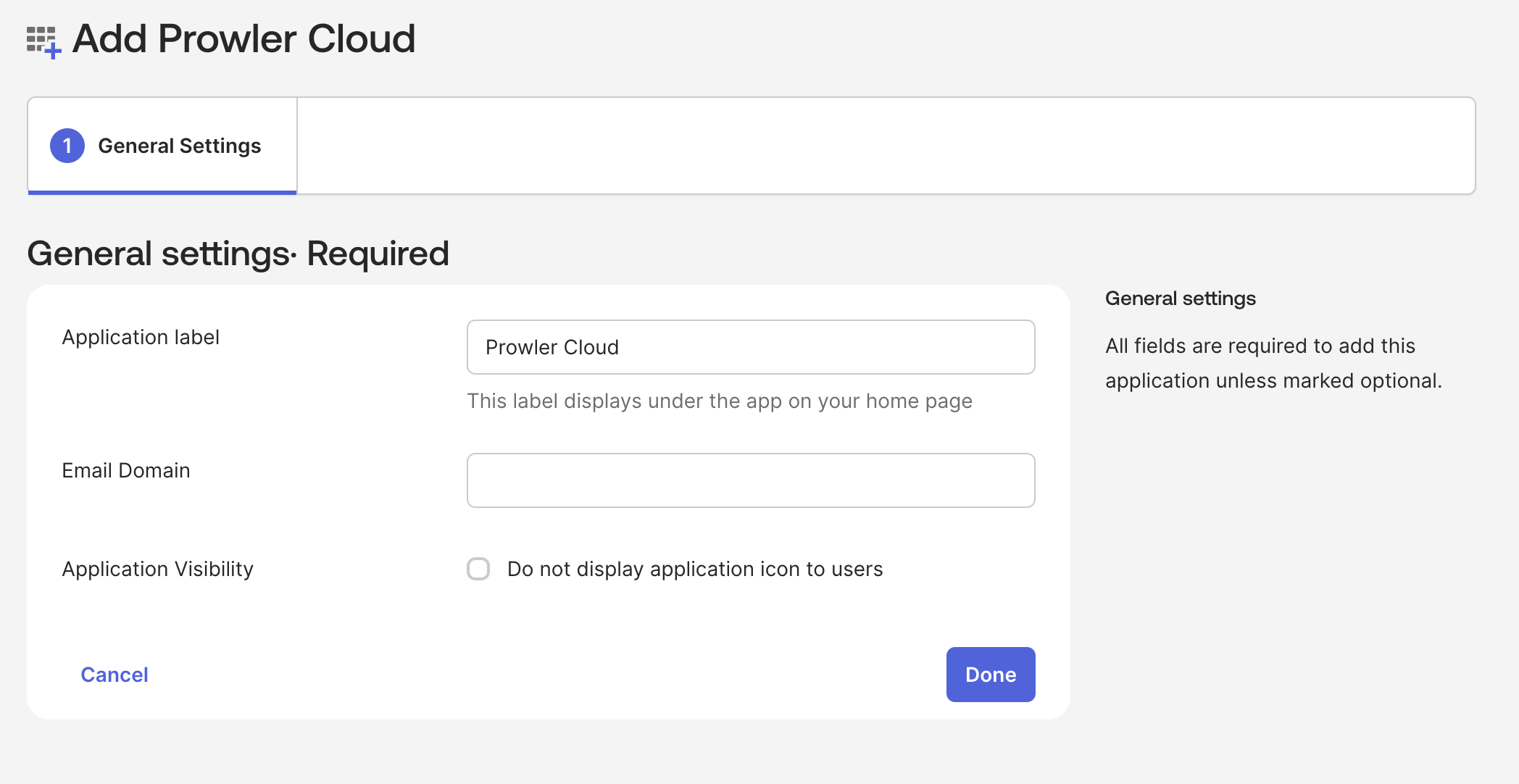
Step 3: Configure the Identity Provider (IdP)
Choose a Method:- Use Generic Method for any SAML 2.0 compliant Identity Provider or when you need custom configuration.
- Use Okta App Catalog if you’re using Okta and want a simplified setup process with pre-configured settings.
- Generic Method
- Okta App Catalog
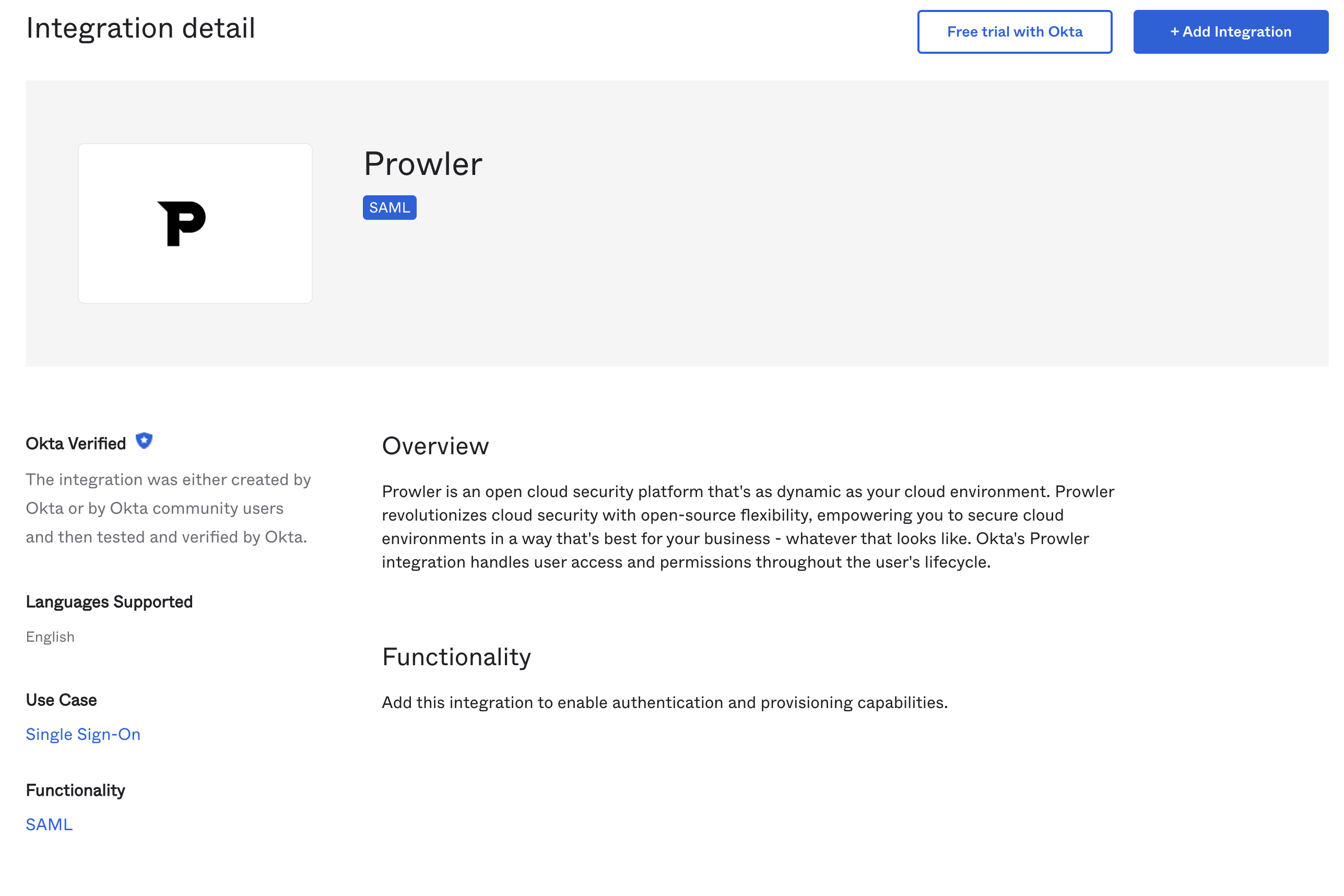
Prowler App displays the SAML configuration information needed to configure the IdP. Use this information to create a new SAML application in the IdP.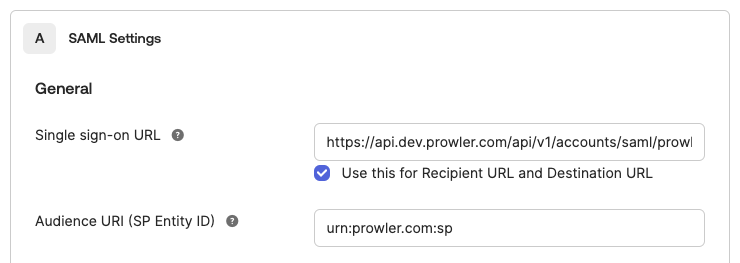
- Assertion Consumer Service (ACS) URL: The endpoint in Prowler that will receive the SAML assertion from the IdP.
- Audience URI (Entity ID): A unique identifier for the Prowler application (Service Provider).

IdP ConfigurationThe exact steps for configuring an IdP vary depending on the provider (Okta, Azure AD, etc.). Please refer to the IdP’s documentation for instructions on creating a SAML application. For SSO integration with Azure AD / Entra ID, see our Entra ID configuration instructions.
| Attribute Name | Description | Required |
|---|---|---|
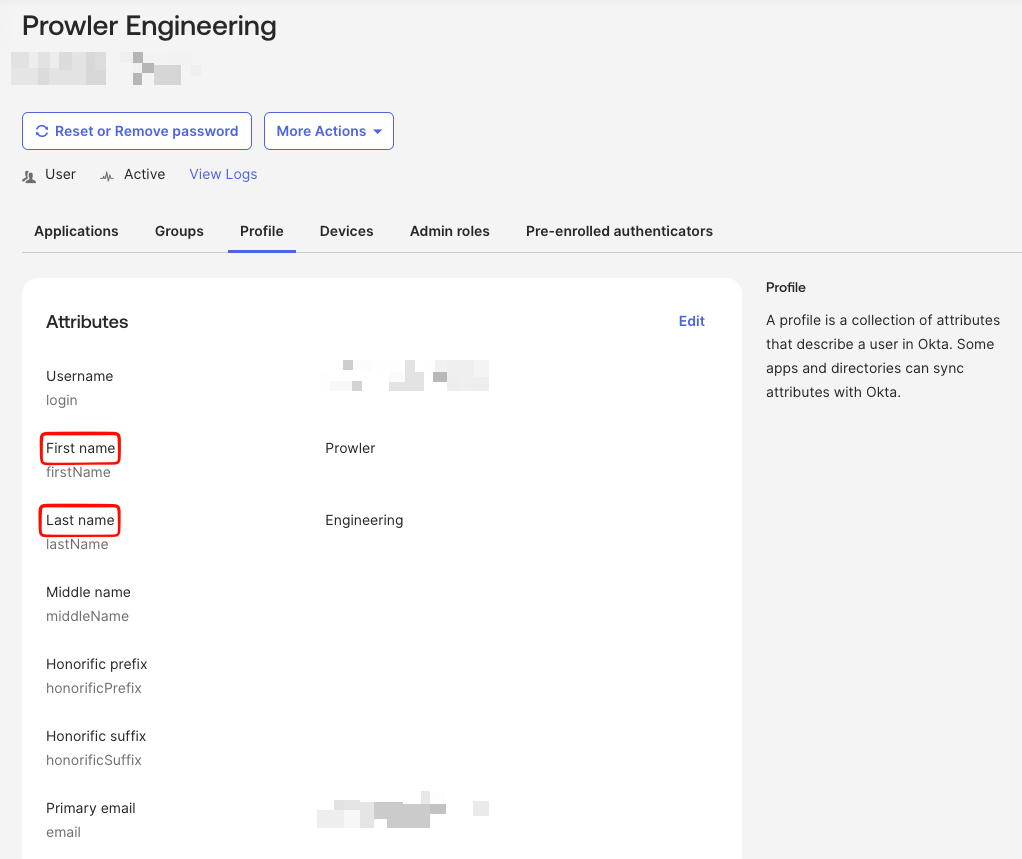
firstName | The user’s first name. | Yes |
lastName | The user’s last name. | Yes |
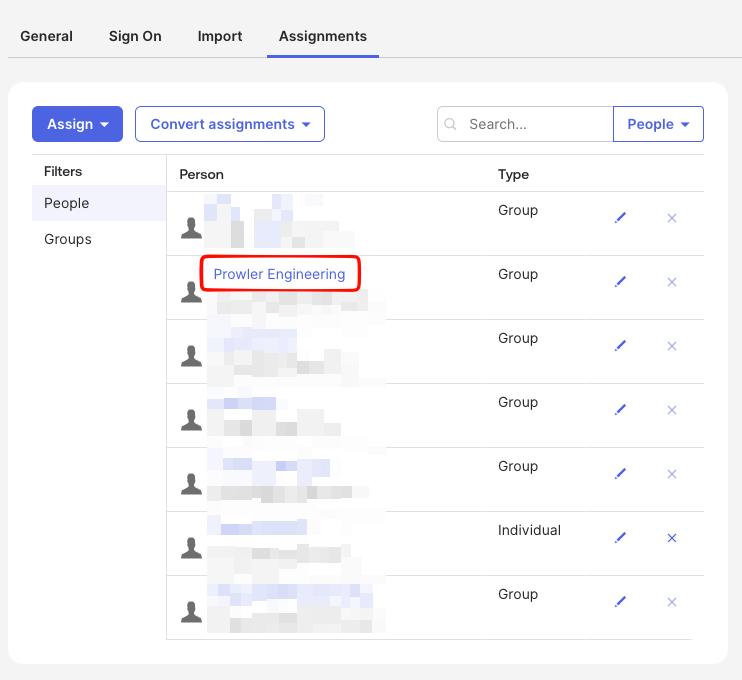
userType | Determines which Prowler role the user receives (e.g., admin, auditor). If a role with that name already exists, the user receives it automatically; if it does not exist, Prowler App creates a new role with that name without permissions. If userType is not defined, the user is assigned the no_permissions role. Role permissions can be edited in the RBAC Management tab. | No |
companyName | The user’s company name. This is automatically populated if the IdP sends an organization attribute. | No |
IdP Attribute MappingNote that the attribute name is just an example and may be different depending on the IdP. For instance, if the IdP provides a 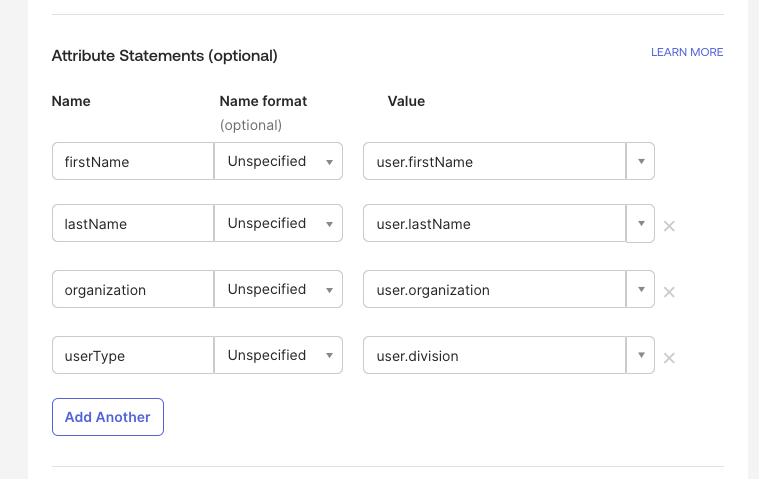
division attribute, it can be mapped to userType.
Step 4: Upload IdP Metadata to Prowler
Once the IdP is configured, it provides a metadata XML file. This file contains the IdP’s configuration information, such as its public key and login URL. To complete the Prowler App configuration:- Return to the Prowler SAML configuration page.
-
Enter the email domain for the organization (e.g.,
mycompany.com). Prowler App uses this to identify users who should authenticate via SAML. - Upload the metadata XML file downloaded from the IdP.
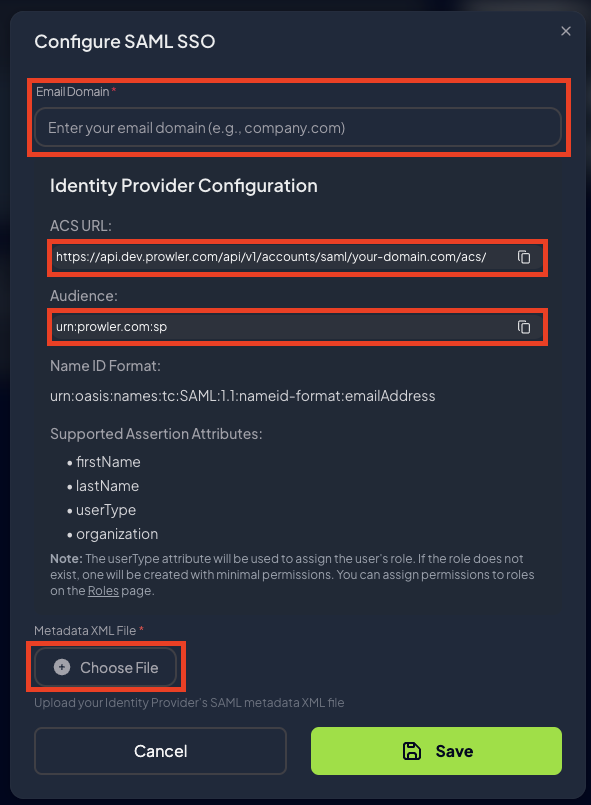
Step 5: Save and Verify Configuration
Click the “Save” button to complete the setup. The “SAML Integration” card will now display an “Active” status, indicating the configuration is complete and enabled.
IdP ConfigurationThe exact steps for configuring an IdP vary depending on the provider (Okta, Azure AD, etc.). Please refer to the IdP’s documentation for instructions on creating a SAML application.
Remove SAML Configuration
SAML SSO can be disabled by removing the existing configuration from the integration panel.
IdP-Initiated SSO
Once SAML SSO is configured, users can access Prowler Cloud directly from their Identity Provider’s dashboard:- Navigate to the IdP dashboard or portal
- Click on the Prowler Cloud application tile
- The system automatically authenticates users and redirects them to Prowler Cloud
SP-Initiated SSO
Users can also initiate the login process directly from Prowler’s login page:- Navigate to the Prowler login page
- Click “Continue with SAML SSO”
- Enter their email address from the configured domain

- The system redirects users to the IdP for authentication
- After successful authentication, users are returned to Prowler App
Developer and Administrator Guide
This section provides technical details for developers and administrators of self-hosted Prowler instances.Environment Configuration
For self-hosted deployments, several environment variables must be configured to ensure SAML SSO functions correctly. These variables are typically set in an.env file.
| Variable | Description | Example |
|---|---|---|
API_BASE_URL | The base URL of the Prowler API instance. | http://mycompany.prowler/api/v1 |
DJANGO_ALLOWED_HOSTS | A comma-separated list of hostnames that the Django backend will accept requests from. Include any domains used to access the Prowler API. | localhost,127.0.0.1,prowler-api,mycompany.prowler |
AUTH_URL | The base URL of the Prowler web UI. This is used to construct the callback URL after authentication. | http://mycompany.prowler |
SAML_SSO_CALLBACK_URL | The full callback URL where users are redirected after authenticating with the IdP. It is typically constructed using the AUTH_URL. | ${AUTH_URL}/api/auth/callback/saml |
SAML API Reference
Prowler provides a REST API to manage SAML configurations programmatically.- Endpoint:
/api/v1/saml-config - Methods:
GET: Retrieve the current SAML configuration for the tenant.POST: Create a new SAML configuration.PATCH: Update an existing SAML configuration.DELETE: Remove the SAML configuration.
API DocumentationFor detailed information on using the API, refer to the Prowler API Reference.
SAML Initiate Endpoint
- Endpoint:
POST /api/v1/accounts/saml/initiate/ - Description: This endpoint initiates the SAML login flow. It takes an email address, determines if the domain has a SAML configuration, and redirects the user to the appropriate IdP login page. It is primarily designed for browser-based flows.
Testing SAML Integration
Follow these steps to test a SAML integration in a development environment.1. Expose the Local Environment
Since the IdP needs to send requests to the local Prowler instance, it must be exposed to the internet. A tool likengrok can be used for this purpose.
To start ngrok, run the following command:
https://<random-string>.ngrok.io) that forwards to the local server on port 8080.
2. Update DJANGO_ALLOWED_HOSTS
To allow requests from ngrok, add its URL to the DJANGO_ALLOWED_HOSTS environment variable.
3. Configure the IdP
When configuring the IdP for testing, use the ngrok URL for the ACS URL:https://<your-ngrok-url>/api/v1/accounts/saml/<YOUR_DOMAIN>/acs/
4. Configure Prowler via API
To create a SAML configuration for testing, usecurl. Replace placeholders with actual data.
5. Initiate Login Flow
To test the end-to-end flow, construct the login URL and open it in a browser. This starts the IdP-initiated login flow.https://<your-ngrok-url>/api/v1/accounts/saml/<YOUR_DOMAIN>/login/
If successful, the user will be redirected back to the Prowler application with a valid session.