What is Prowler?
Prowler is the world’s most widely used open-source cloud security platform that automates security and compliance across any cloud environment. With hundreds of ready-to-use security checks, remediation guidance, and compliance frameworks, Prowler delivers AI-driven, customizable, and easy-to-use monitoring and integrations, making cloud security simple, scalable, and cost-effective for organizations of any size.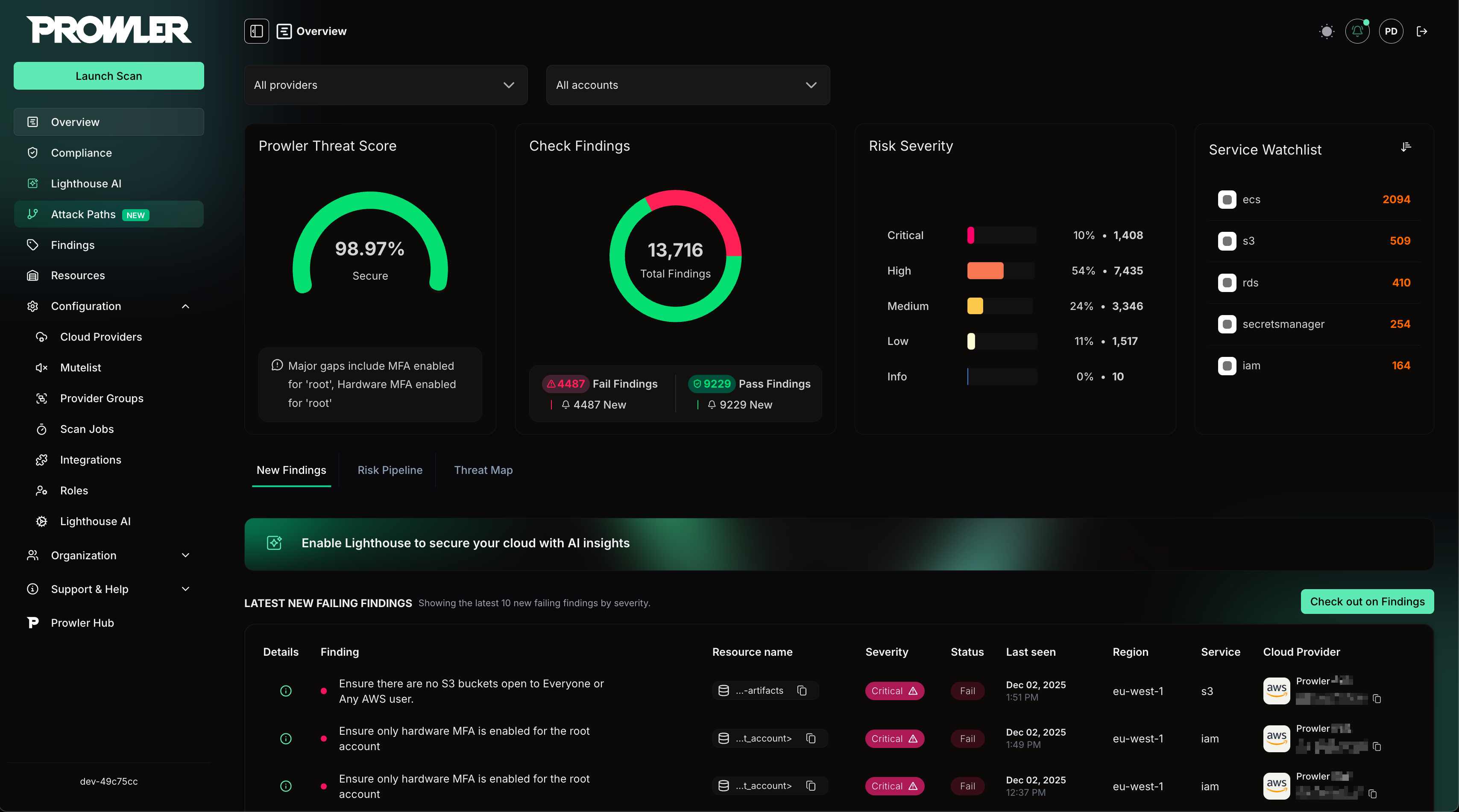
Prowler CLI
Command Line Interface
Prowler App
Web Application
Prowler Cloud
A managed service built on top of Prowler App.
Prowler Hub
A public library of versioned checks, cloud service artifacts, and compliance frameworks.
Supported Providers
The supported providers right now are:| Provider | Support | Audit Scope/Entities | Interface |
|---|---|---|---|
| AWS | Official | Accounts | UI, API, CLI |
| Azure | Official | Subscriptions | UI, API, CLI |
| Google Cloud | Official | Projects | UI, API, CLI |
| Kubernetes | Official | Clusters | UI, API, CLI |
| M365 | Official | Tenants | UI, API, CLI |
| Github | Official | Organizations / Repositories | UI, API, CLI |
| Oracle Cloud | Official | Tenancies / Compartments | UI, API, CLI |
| Alibaba Cloud | Official | Accounts | UI, API, CLI |
| Cloudflare | Official | Accounts | CLI |
| Infra as Code | Official | Repositories | UI, API, CLI |
| MongoDB Atlas | Official | Organizations | UI, API, CLI |
| OpenStack | Official | Projects | CLI |
| LLM | Official | Models | CLI |
| Image | Official | Container Images | CLI |
| NHN | Unofficial | Tenants | CLI |

