Getting Started with M365 on Prowler Cloud/App¶
Set up your M365 account to enable security scanning using Prowler Cloud/App.
Requirements¶
To configure your M365 account, you'll need:
-
Obtain a domain from the Entra ID portal.
-
Access Prowler Cloud/App and add a new cloud provider
Microsoft 365. -
Configure your M365 account:
3.1 Create the Service Principal app.
3.2 Grant the required API permissions.
3.3 Assign the required roles to your user.
-
Add the credentials to Prowler Cloud/App.
Step 1: Obtain your Domain¶
Go to the Entra ID portal, then you can search for Domain or go to Identity > Settings > Domain Names.
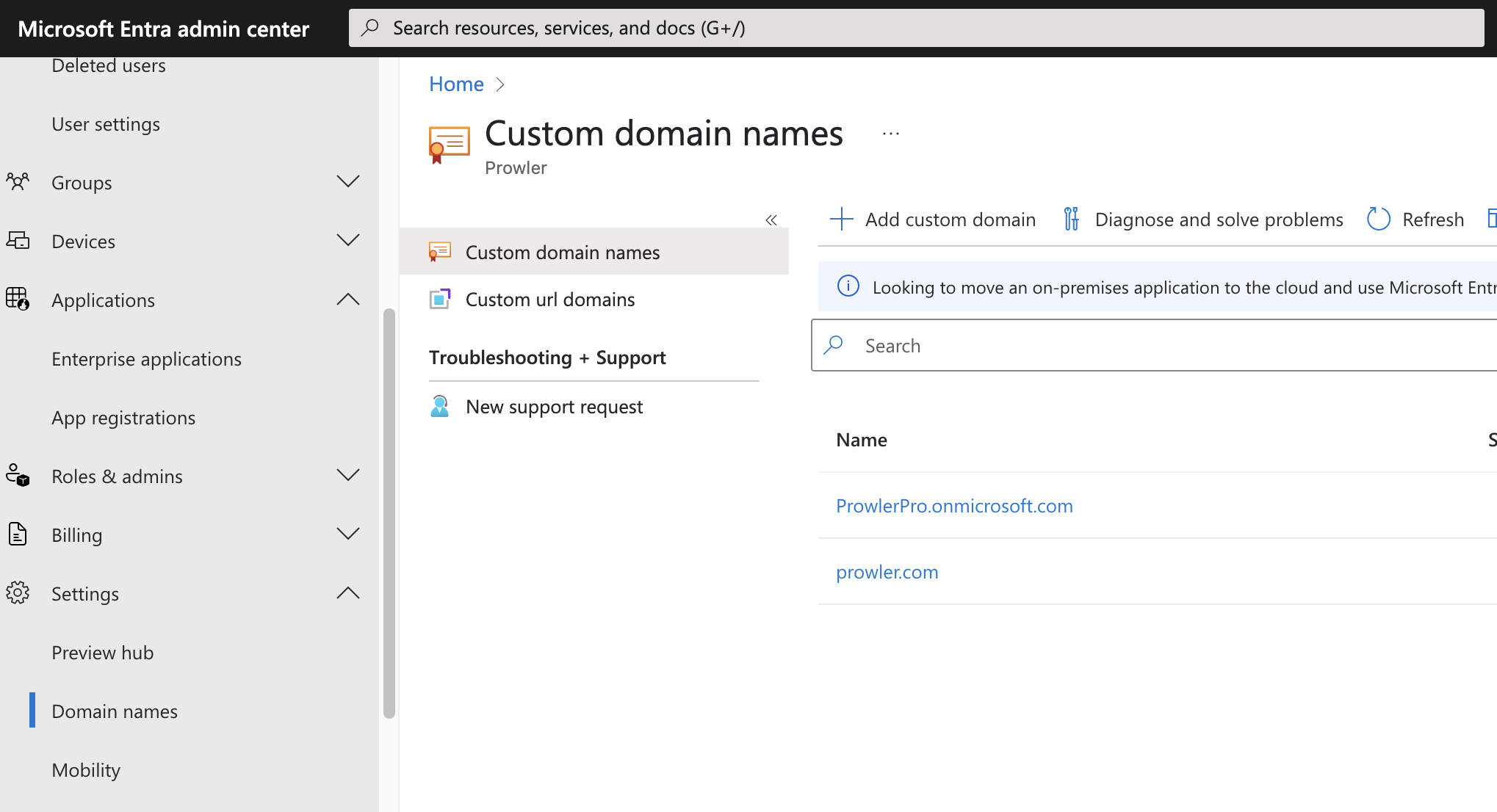
Once you are there just select the domain you want to use.
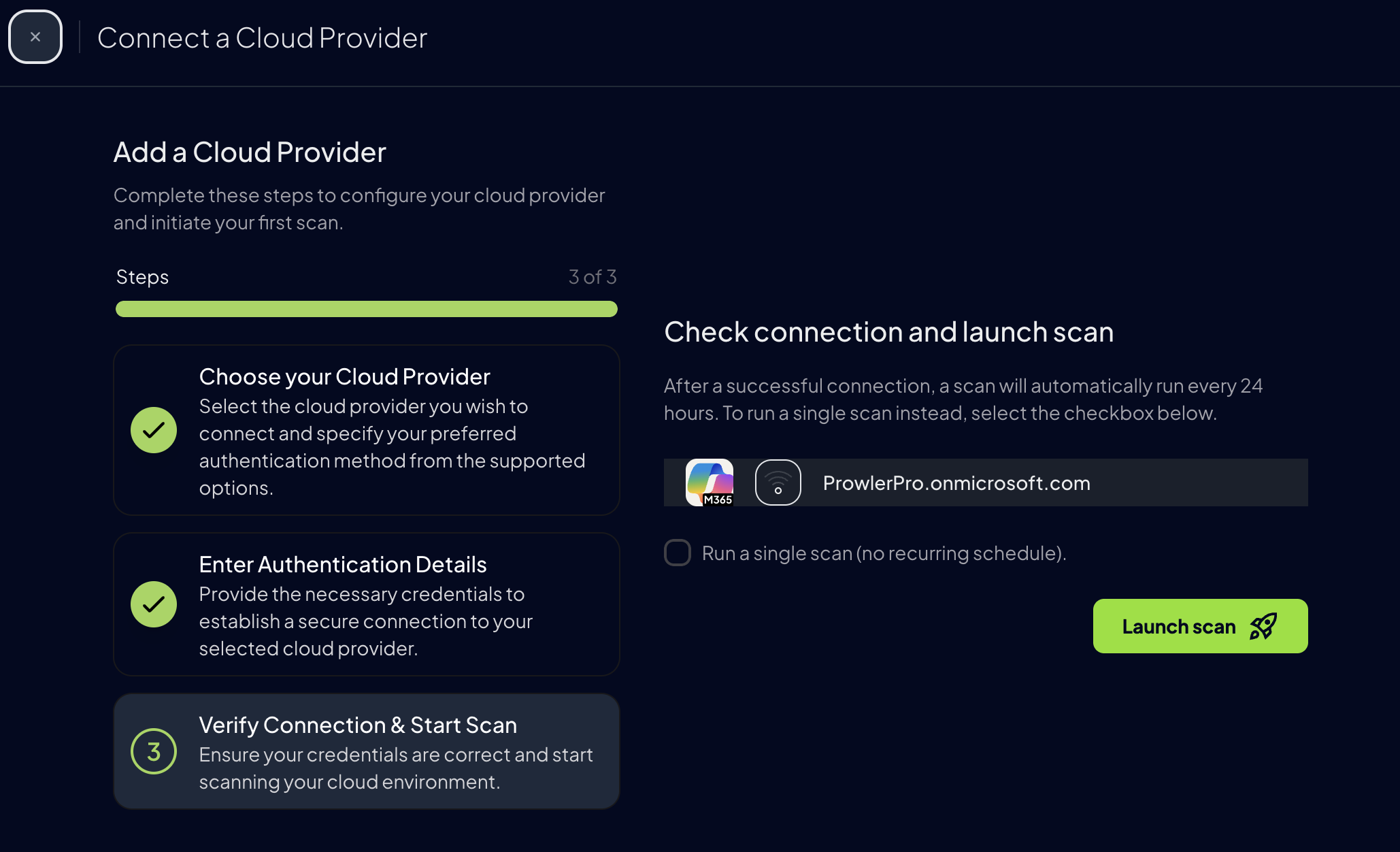
Step 2: Access Prowler Cloud/App¶
- Go to Prowler Cloud or launch Prowler App
-
Navigate to
Configuration>Cloud Providers
-
Click on
Add Cloud Provider
-
Select
Microsoft 365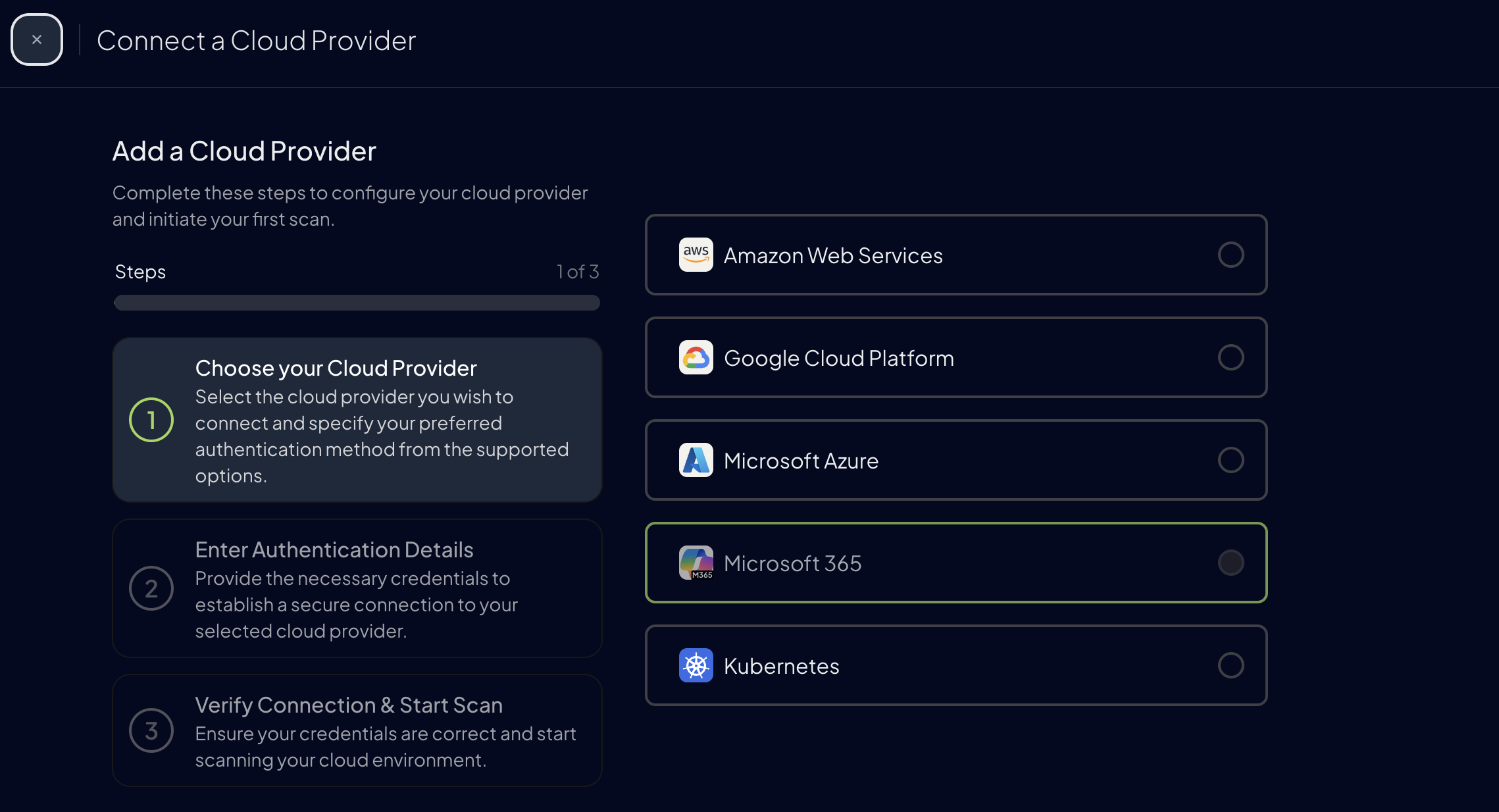
-
Add the Domain ID and an optional alias, then click
Next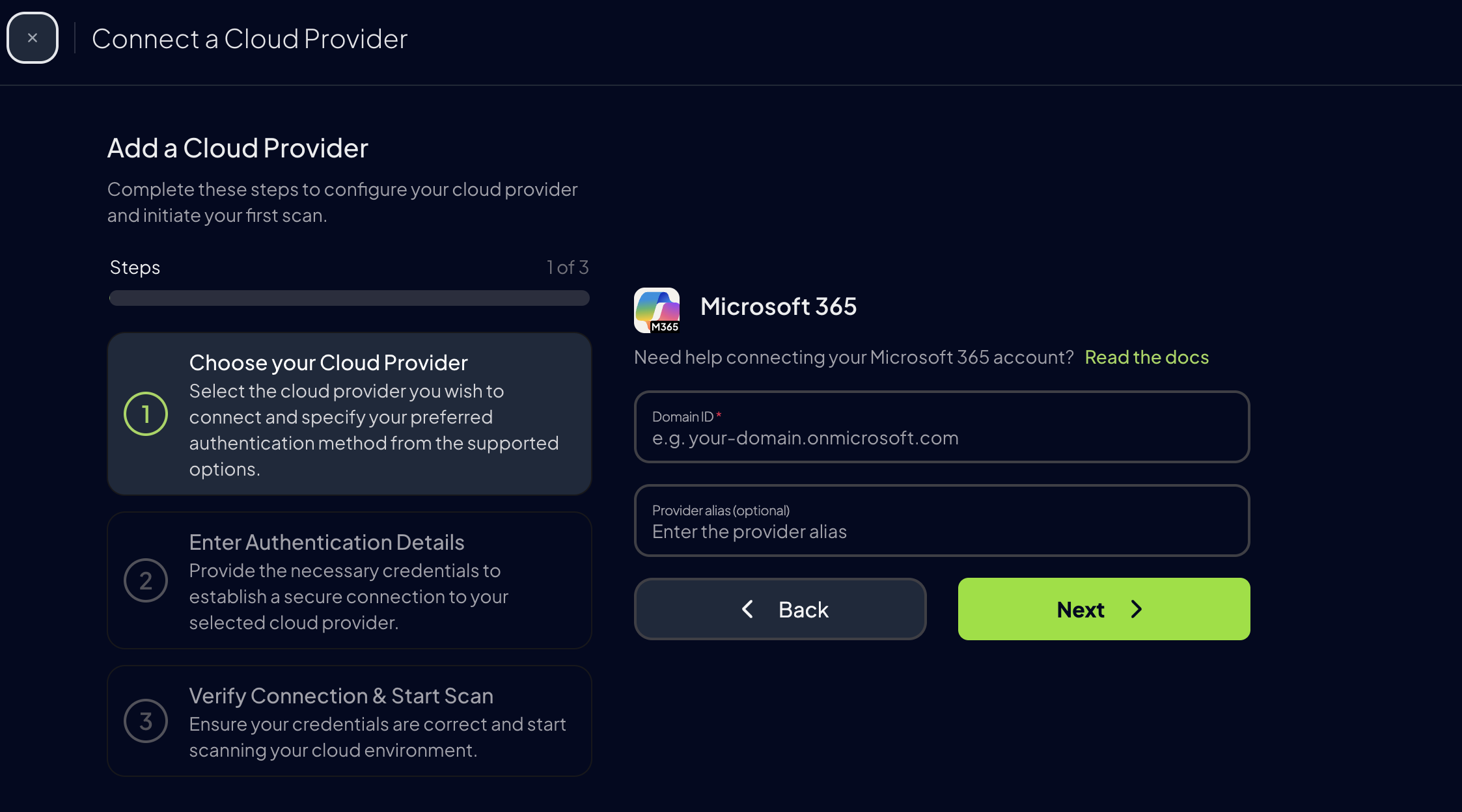
Step 3: Configure your M365 account¶
Create the Service Principal app¶
A Service Principal is required to grant Prowler the necessary privileges.
-
Access Microsoft Entra ID
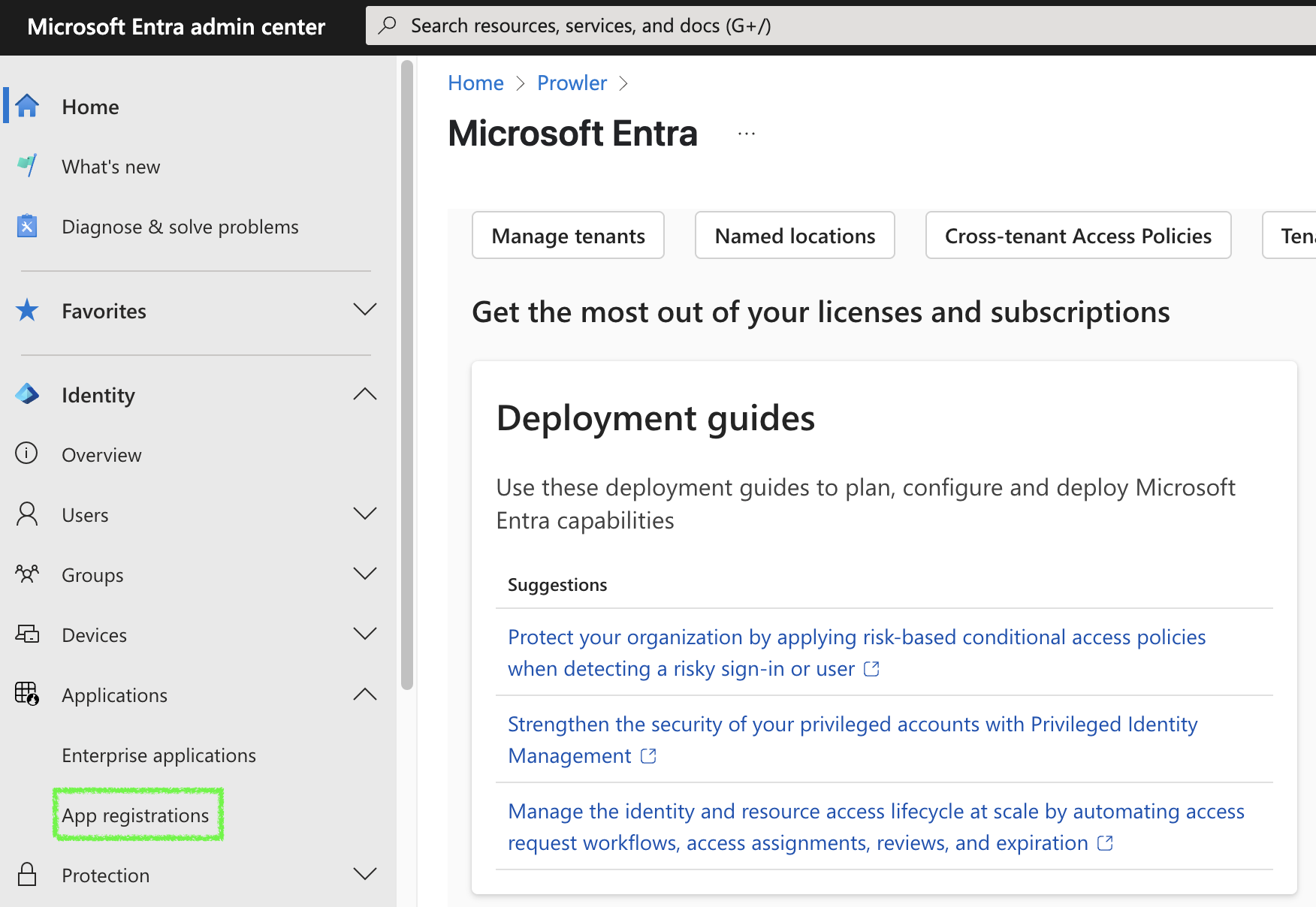
-
Navigate to
Applications>App registrations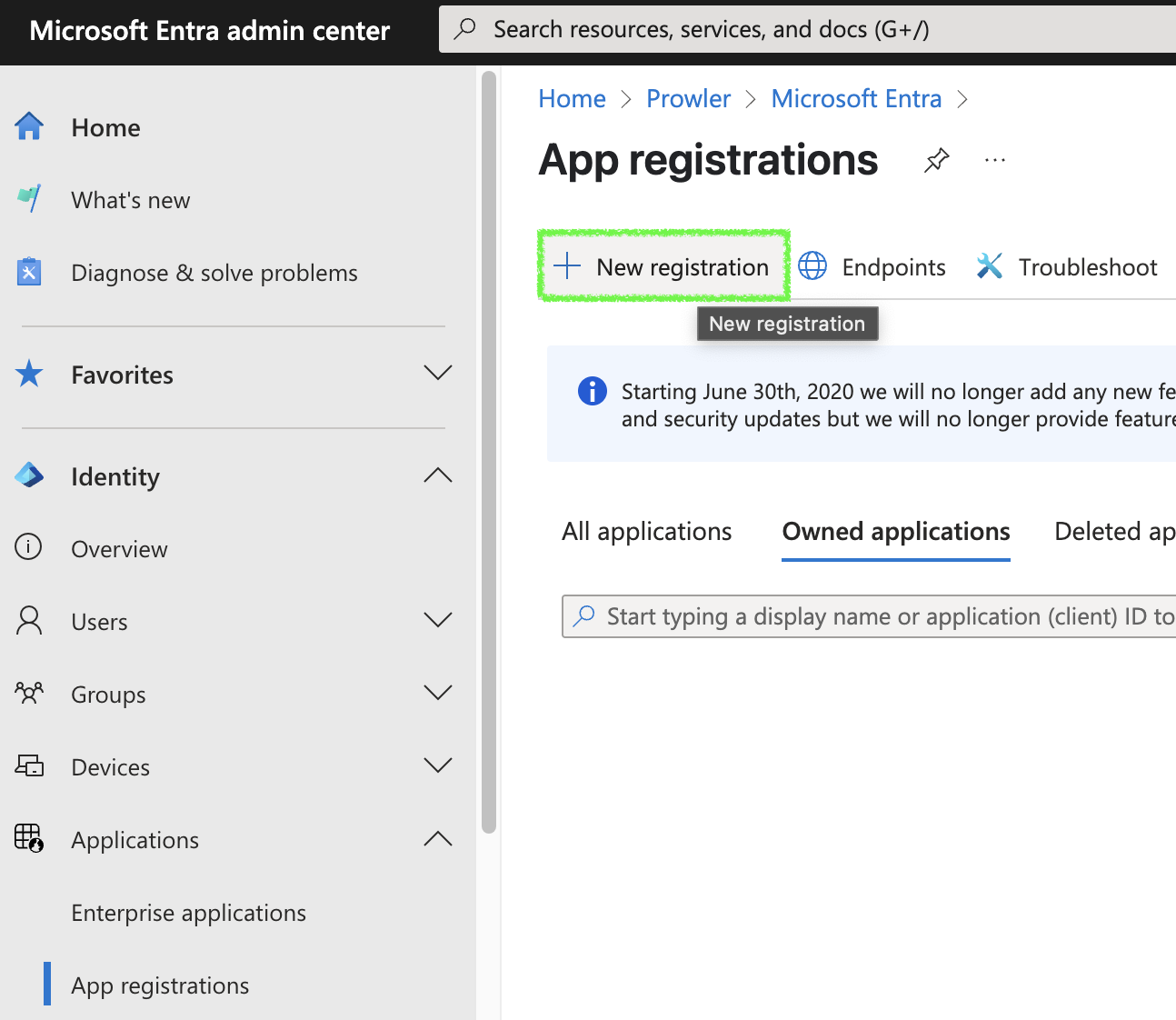
-
Click
+ New registration, complete the form, and clickRegister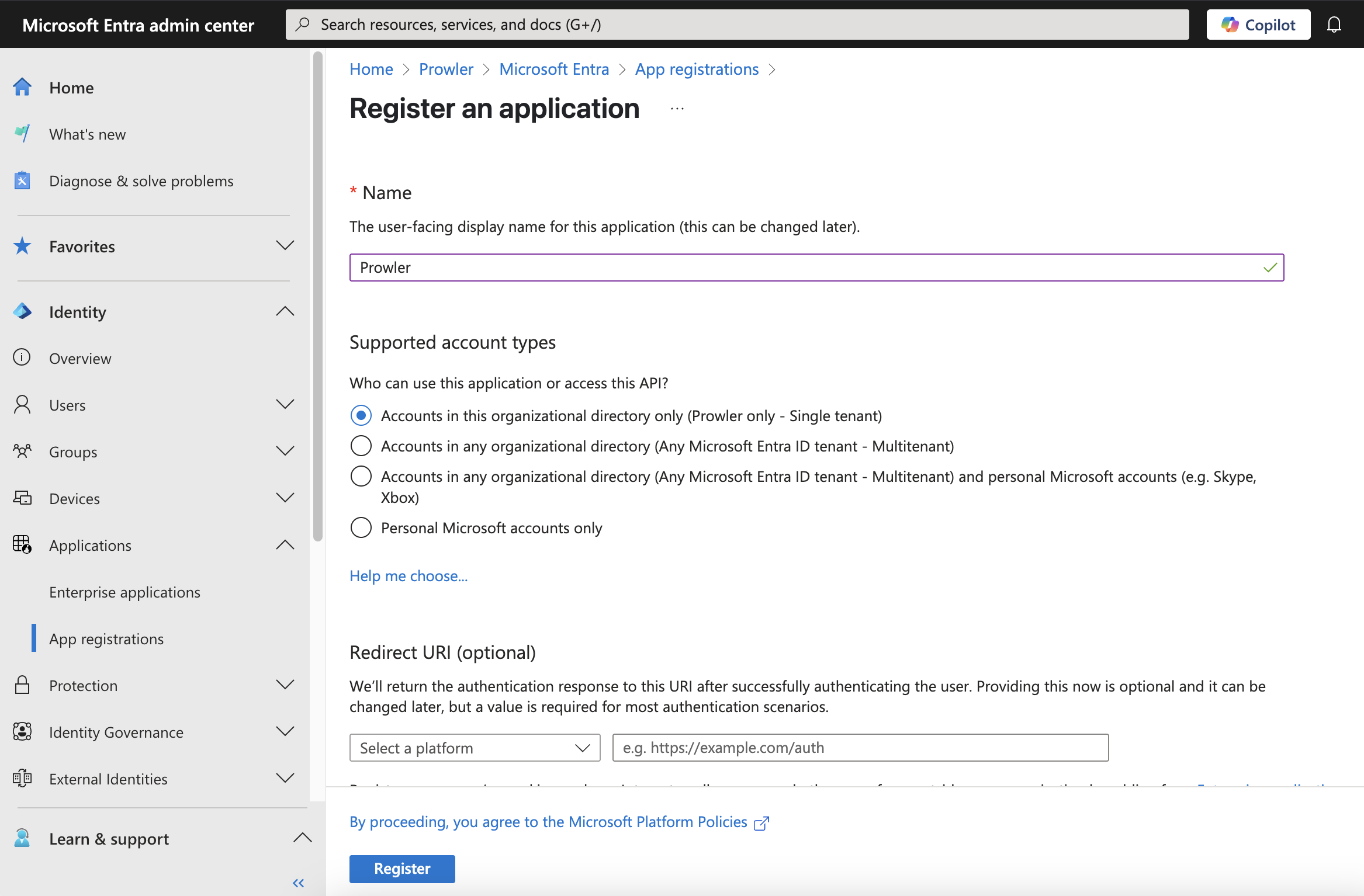
-
Go to
Certificates & secrets>Client secrets>+ New client secret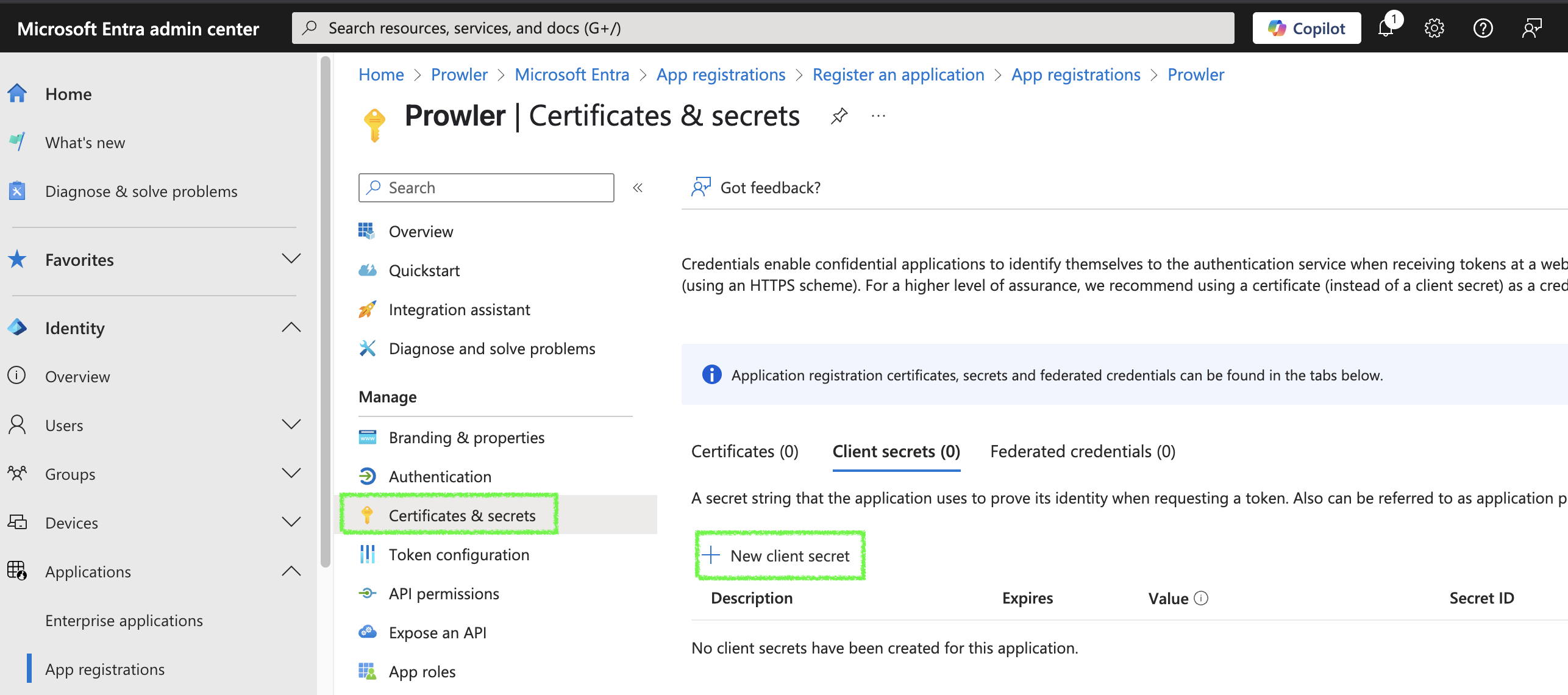
-
Fill in the required fields and click
Add, then copy the generatedvalue(that value will beAZURE_CLIENT_SECRET)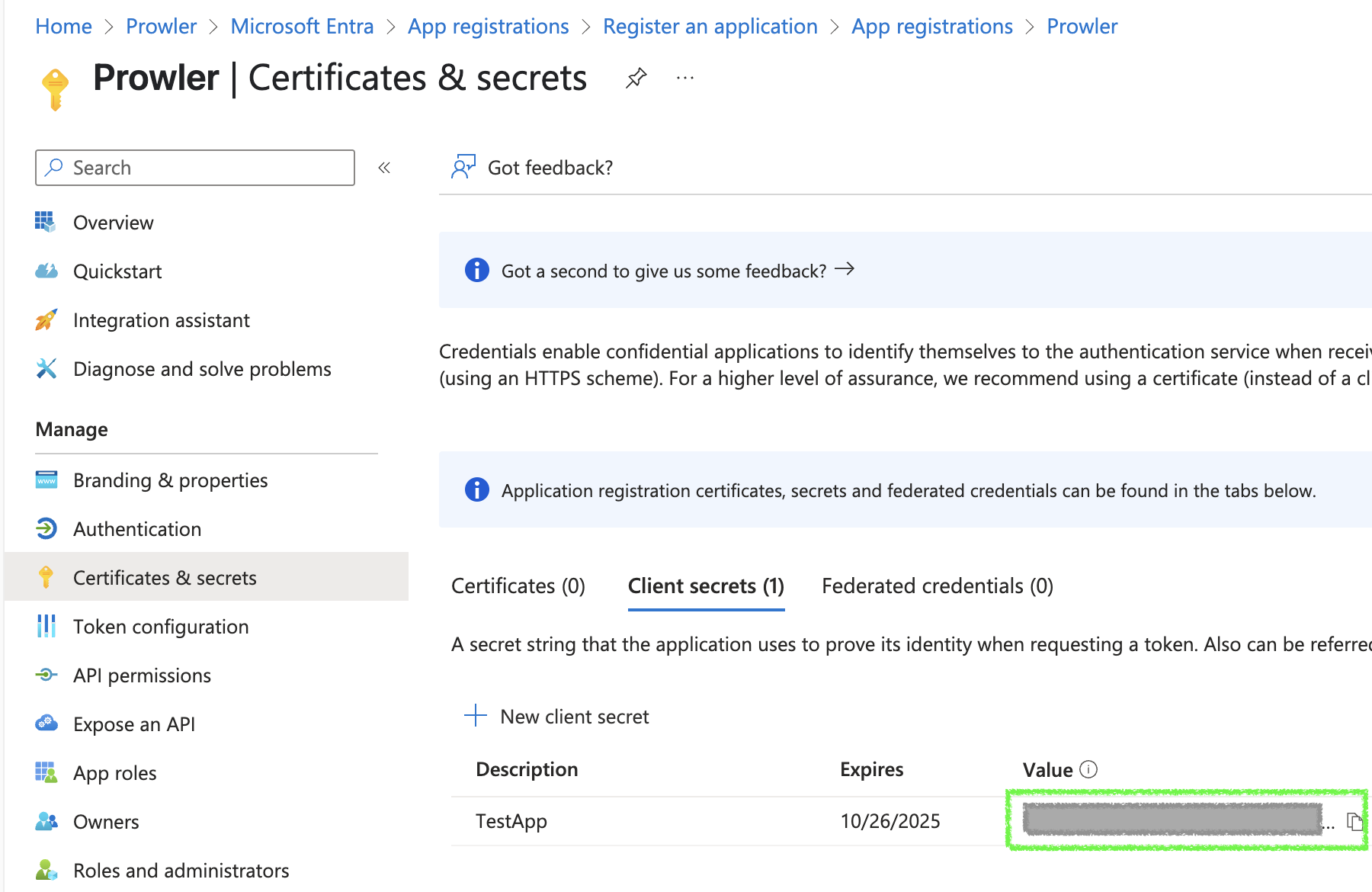
With this done you will have all the needed keys, summarized in the following table
| Value | Description |
|---|---|
| Client ID | Application (client) ID |
| Client Secret | AZURE_CLIENT_SECRET |
| Tenant ID | Directory (tenant) ID |
Grant required Graph API permissions¶
Assign the following Microsoft Graph permissions:
AuditLog.Read.All: Required for Entra service.Directory.Read.All: Required for all services.Policy.Read.All: Required for all services.SharePointTenantSettings.Read.All: Required for SharePoint service.User.Read(IMPORTANT: this is set as delegated): Required for the sign-in only if using user authentication.
Note
You can replace Directory.Read.All with Domain.Read.All is a more restrictive permission but you won't be able to run the Entra checks related with DirectoryRoles and GetUsers.
If you do this you will need to add also the
Organization.Read.Allpermission to the service principal application in order to authenticate.
Follow these steps to assign the permissions:
-
Go to your App Registration > Select your Prowler App created before > click on
API permissions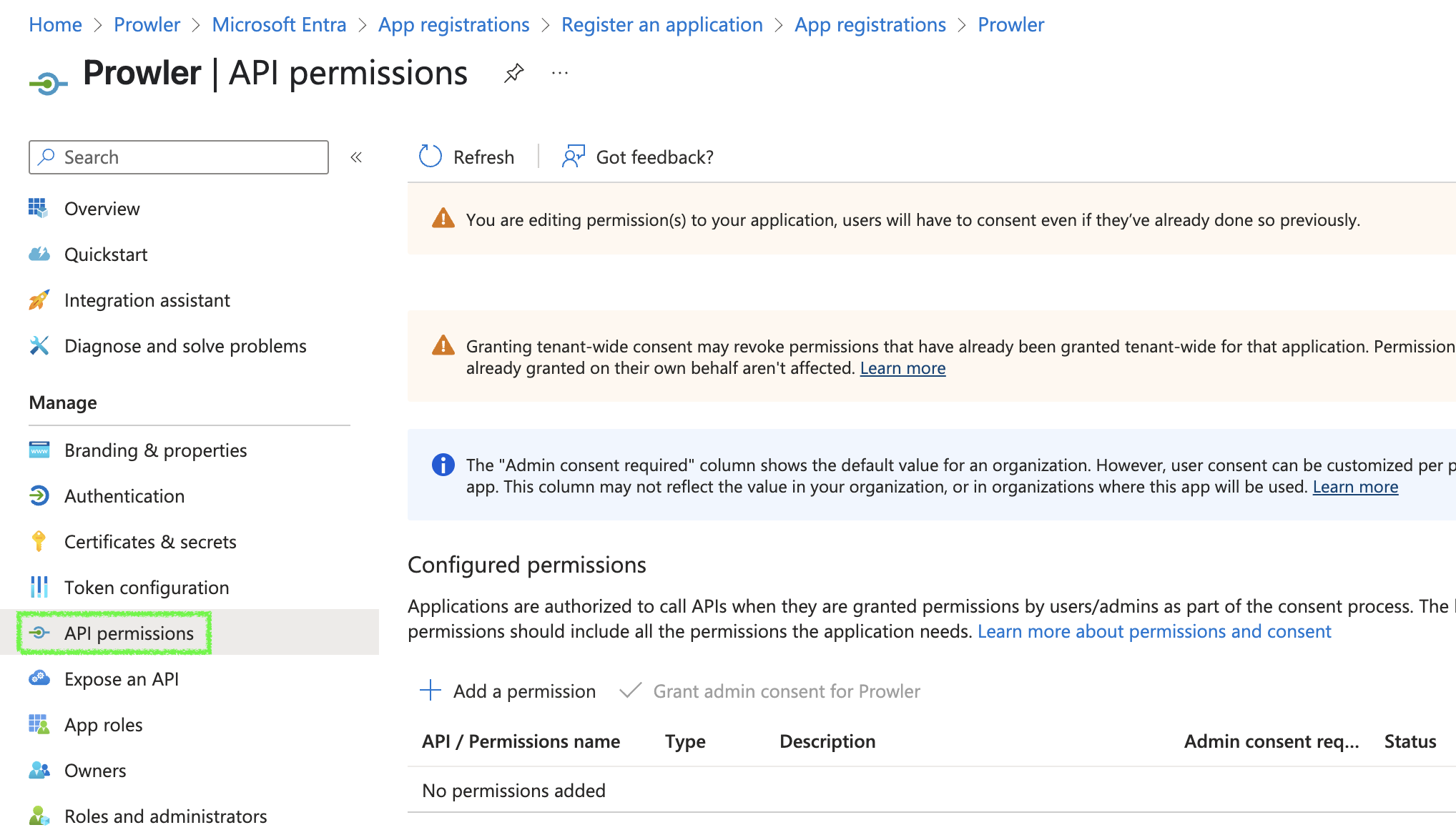
-
Click
+ Add a permission>Microsoft Graph>Application permissions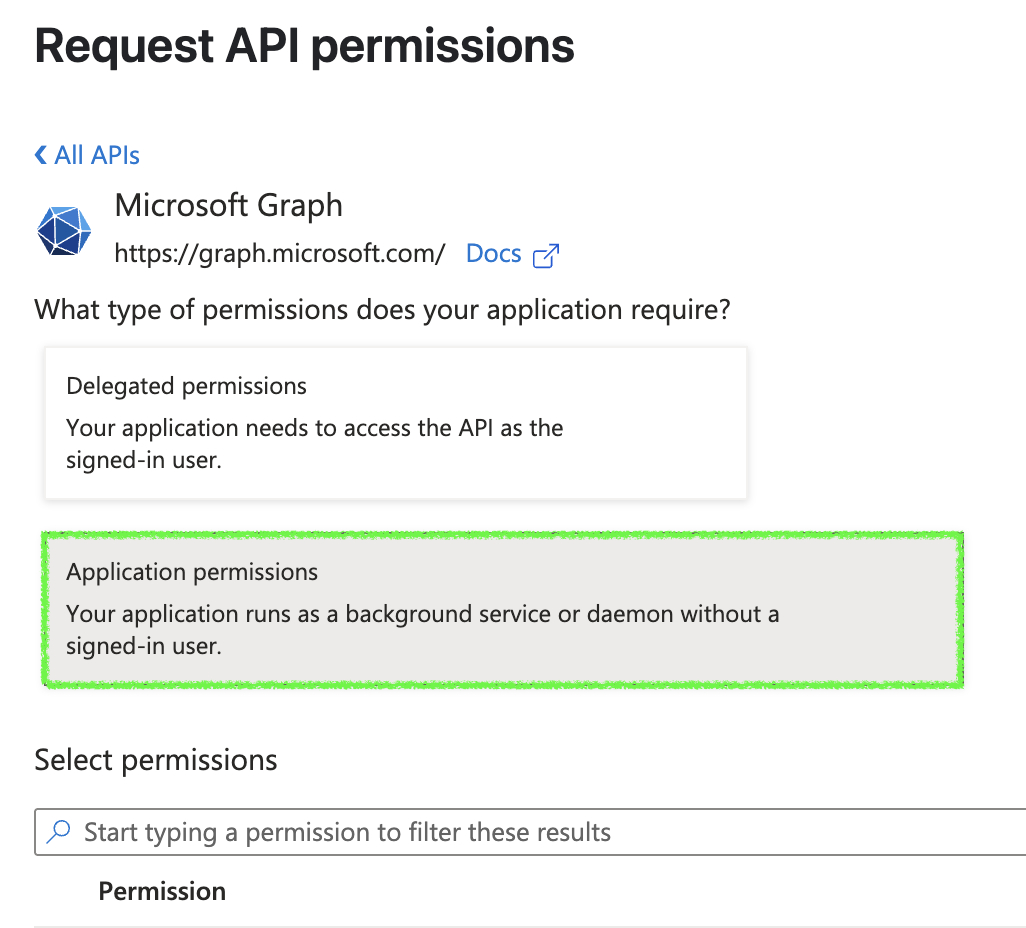
-
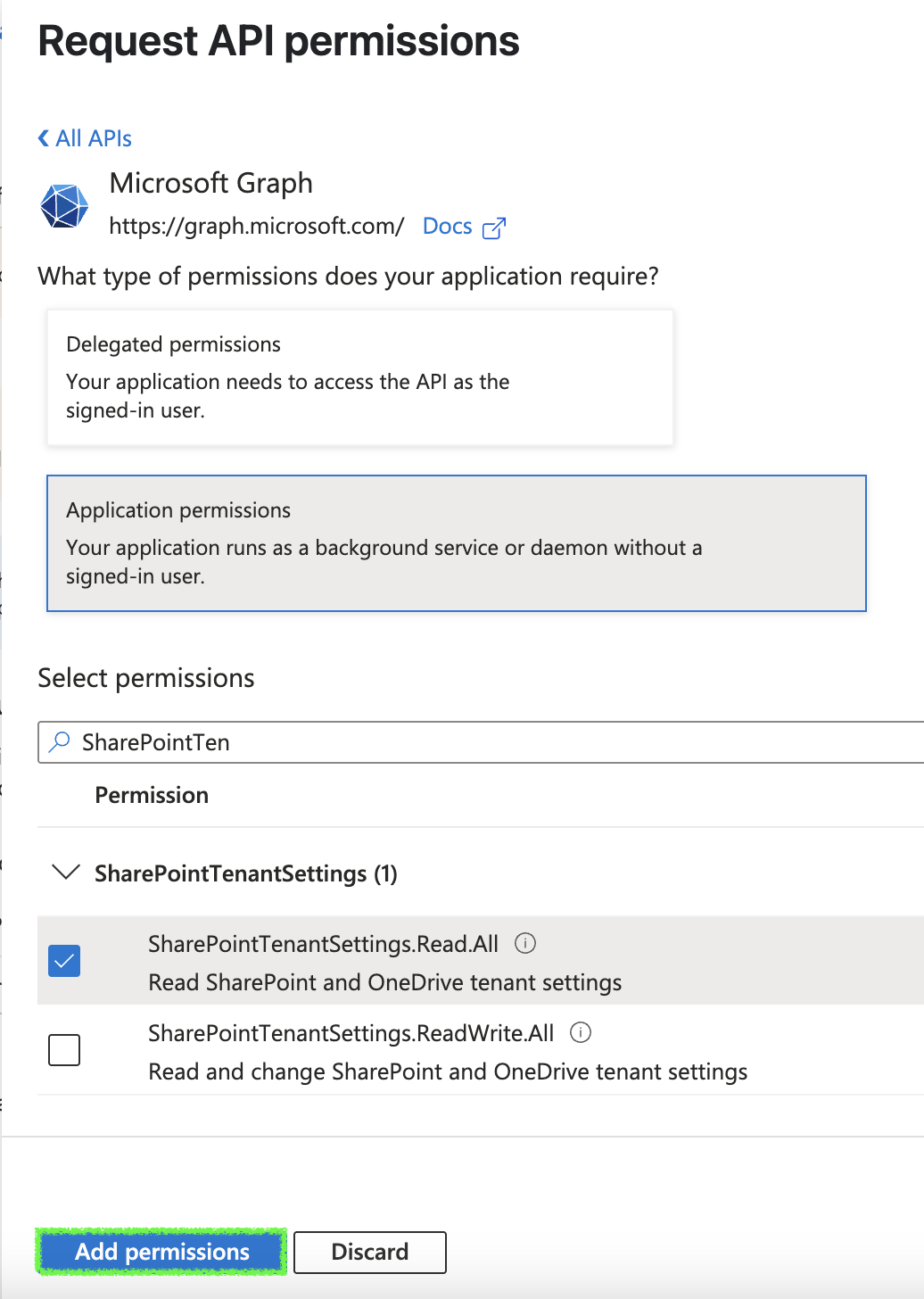
Search and select every permission below and once all are selected click on
Add permissions:AuditLog.Read.All: Required for Entra service.Directory.Read.AllPolicy.Read.AllSharePointTenantSettings.Read.All

Grant PowerShell modules permissions¶
The permissions you need to grant depends on whether you are using user credentials or service principal to authenticate to the M365 modules.
Warning
Make sure you add the correct set of permissions for the authentication method you are using.
If using application(service principal) authentication¶
Warning
Currently Prowler Cloud only supports user authentication.
To grant the permissions for the PowerShell modules via application authentication, you need to add the necessary APIs to your app registration.
Warning
You need to have a license that allows you to use the APIs.
-
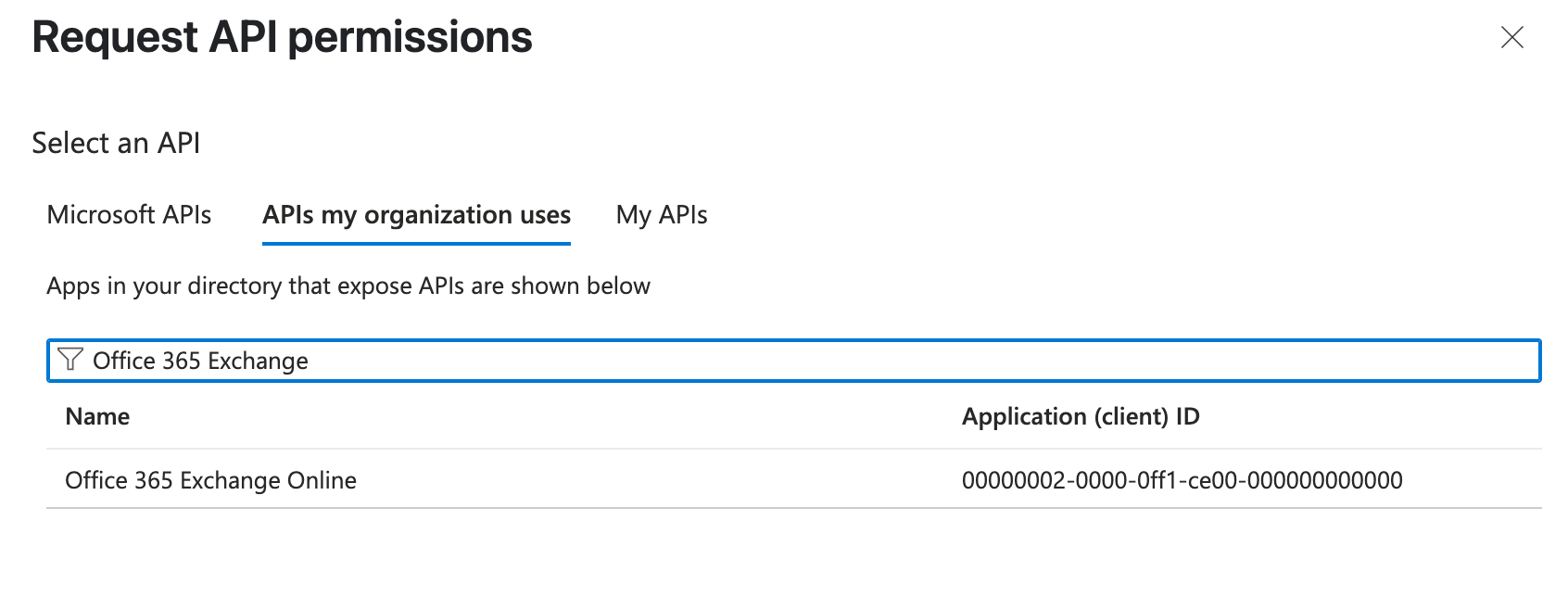
Add Exchange API:
- Search and select
Office 365 Exchange OnlineAPI in APIs my organization uses.
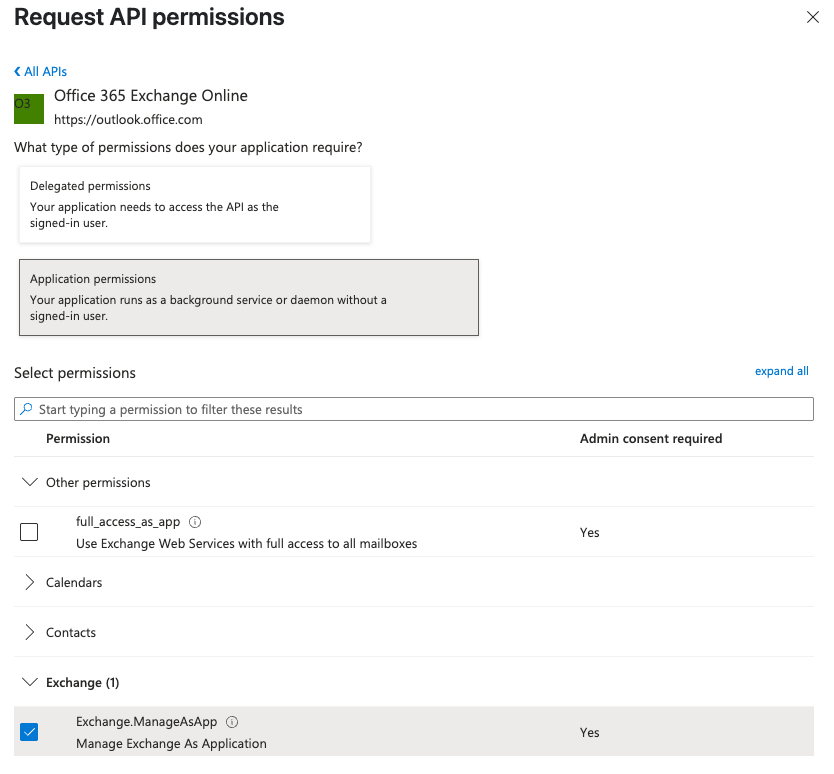
- Select
Exchange.ManageAsApppermission and click onAdd permissions.
You also need to assign the
Exchange Administratorrole to the app. For that go toRoles and administratorsand in theAdministrative rolessection clickhereto go to the directory level assignment: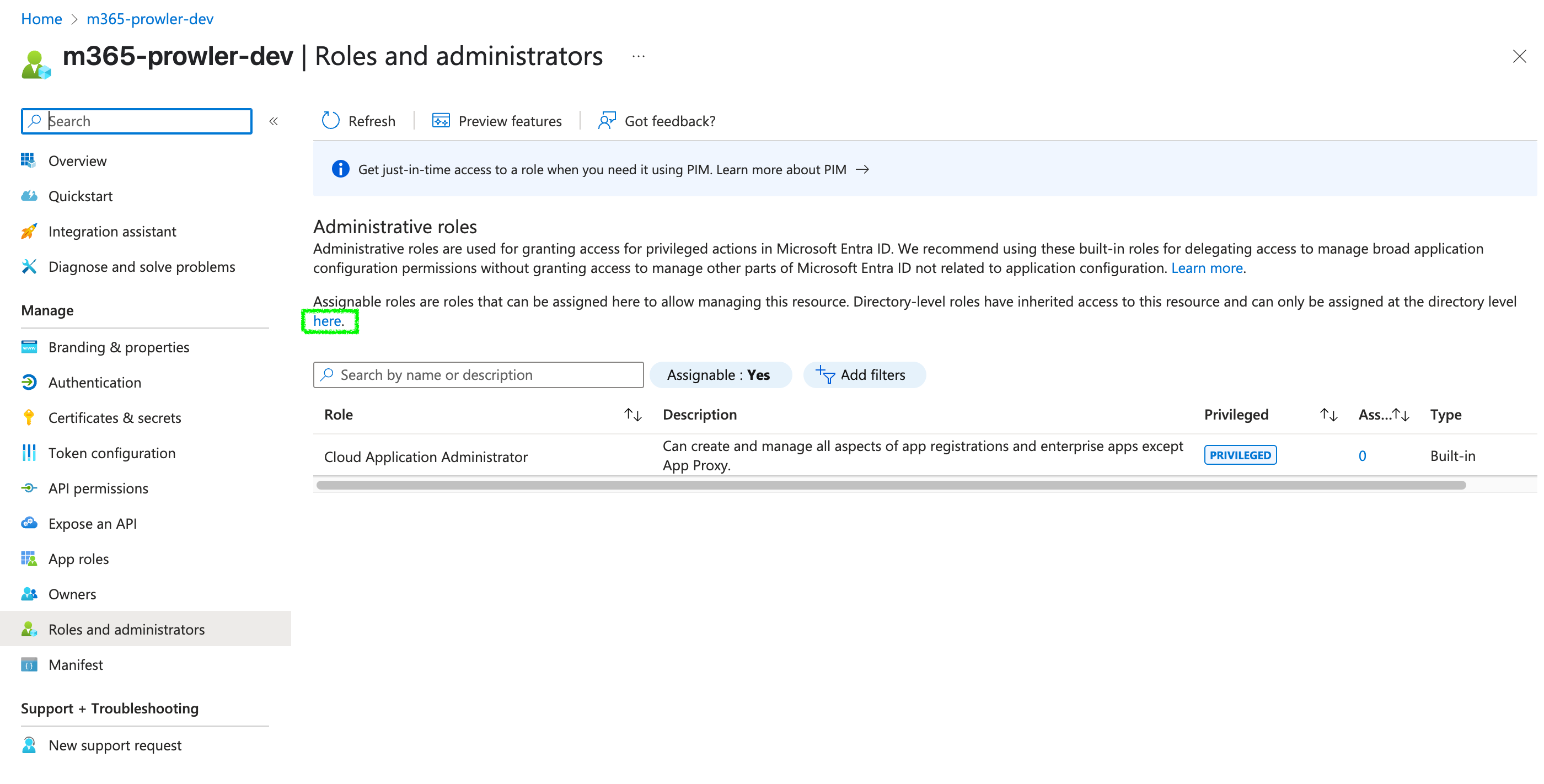
Once in the directory level assignment, search for
Exchange Administratorand click on it to open the assginments page of that role.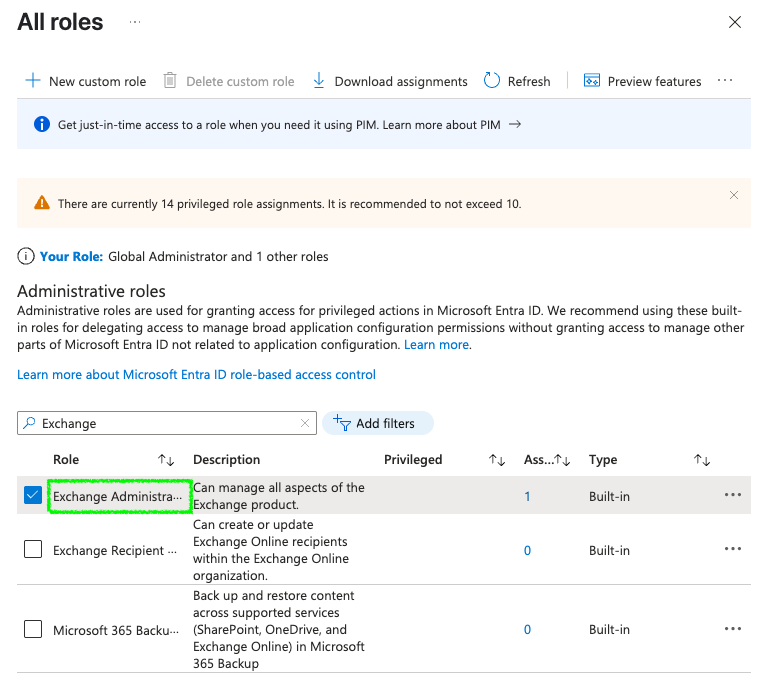
Click on
Add assignments, search for your app and click onAssign.You have to select it as
Activeand click onAssignto assign the role to the app.
- Search and select
-
Add Teams API:
- Search and select
Skype and Teams Tenant Admin APIAPI in APIs my organization uses.

- Select
application_accesspermission and click onAdd permissions.

- Search and select
-
Click on
Grant admin consent for <your-tenant-name>to grant admin consent.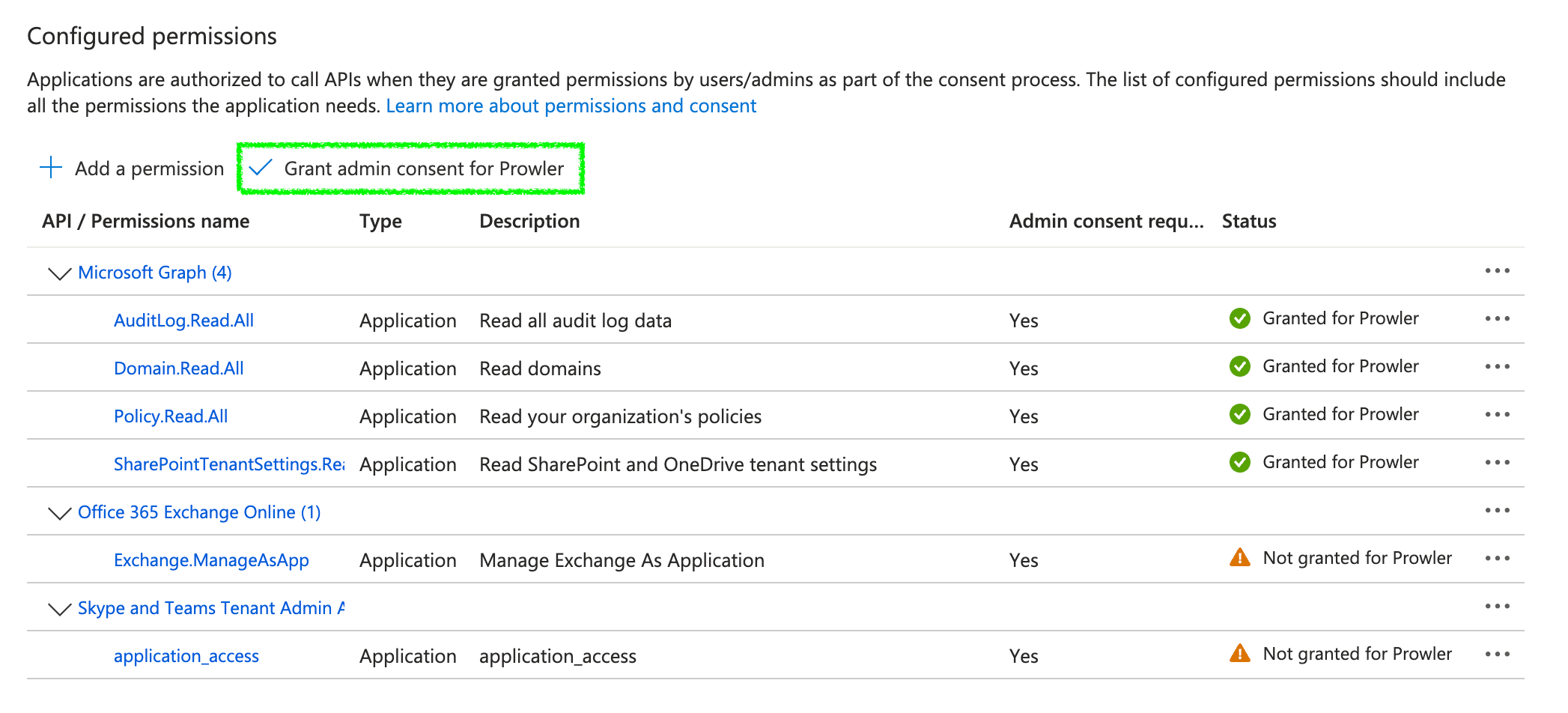
The final result of permission assignment should be this:

Warning
Remember that if the user is newly created, you need to sign in with that account first, as Microsoft will prompt you to change the password. If you don’t complete this step, user authentication will fail because Microsoft marks the initial password as expired.
If using user authentication (Currently Prowler Cloud only supports this method)¶
-
Search and select:
User.Read
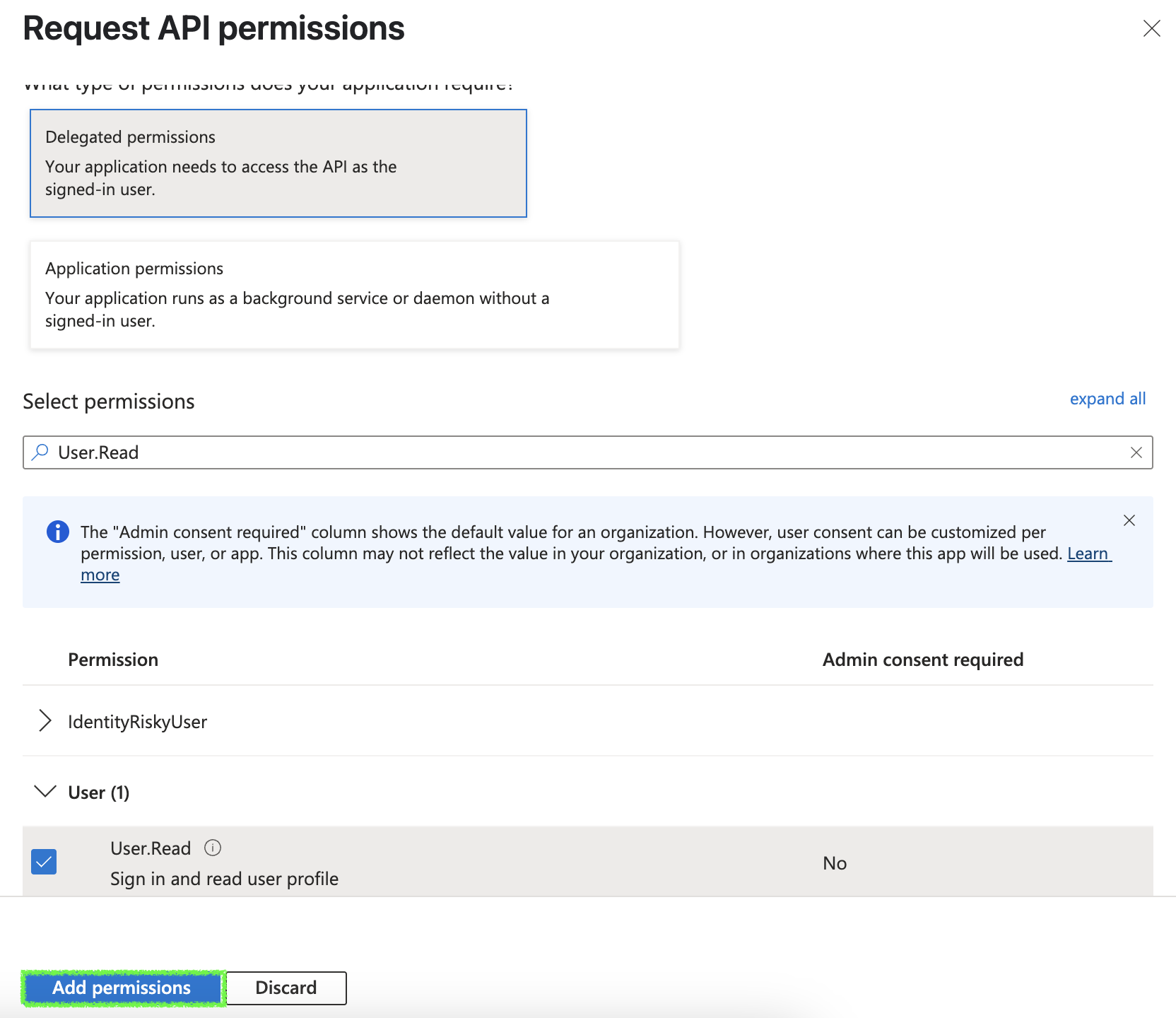
-
Click
Add permissions, then grant admin consent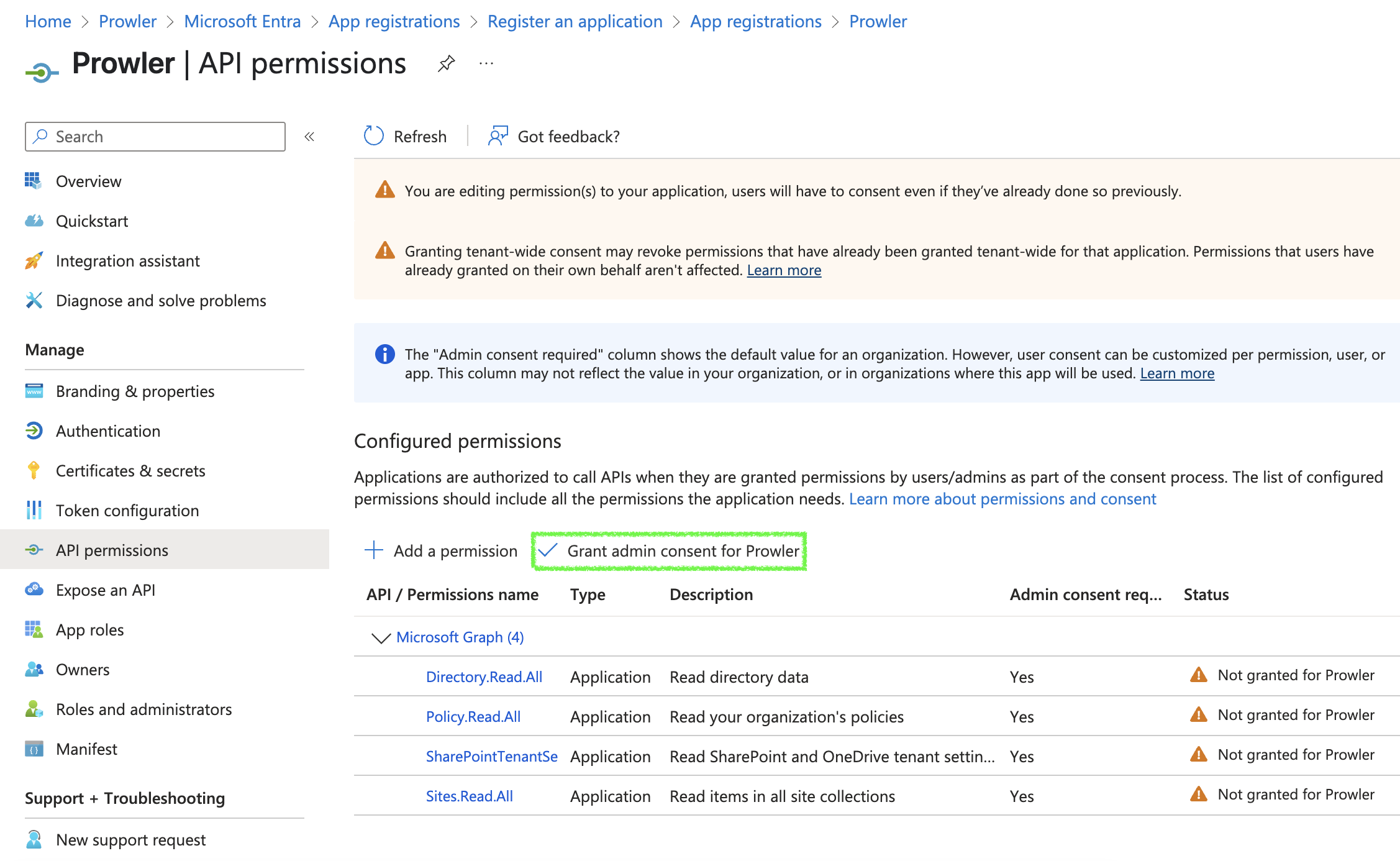
The final result of permission assignment should be this:
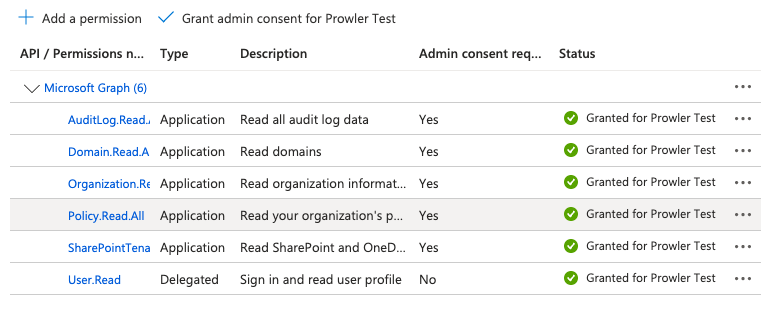
-
Assign required roles to your user
Assign one of the following roles to your User:
Global Reader(recommended): this allows you to read all roles needed.Exchange AdministratorandTeams Administrator: user needs both roles but with this roles you can access to the same information as a Global Reader (here you only read so that's why we recomend that role).
Follow these steps to assign the role:
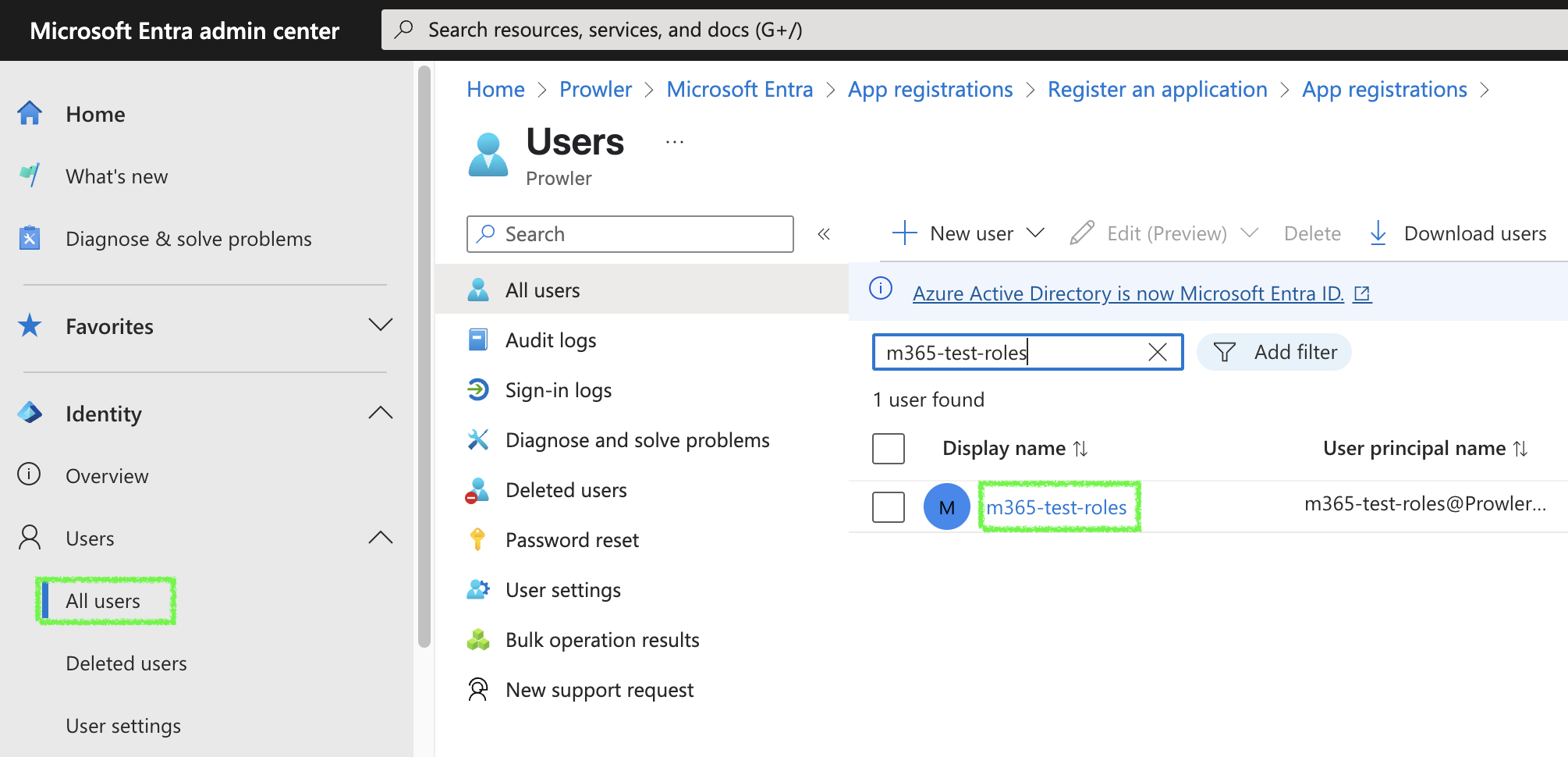
-
Go to Users > All Users > Click on the email for the user you will use
-
Click
Assigned Roles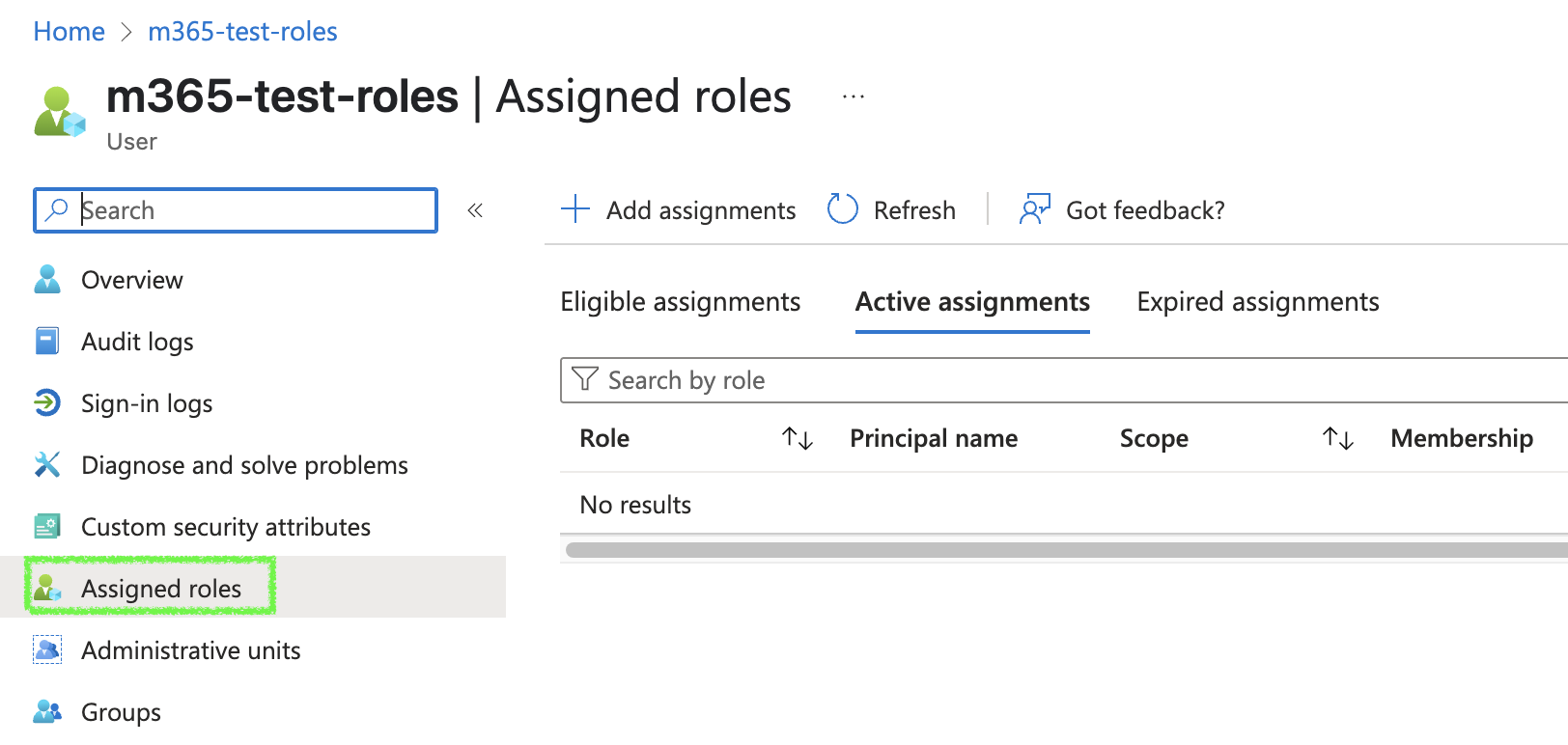
-
Click on
Add assignments, then search and select:Global ReaderThis is the recommended, if you want to use the others just search for them
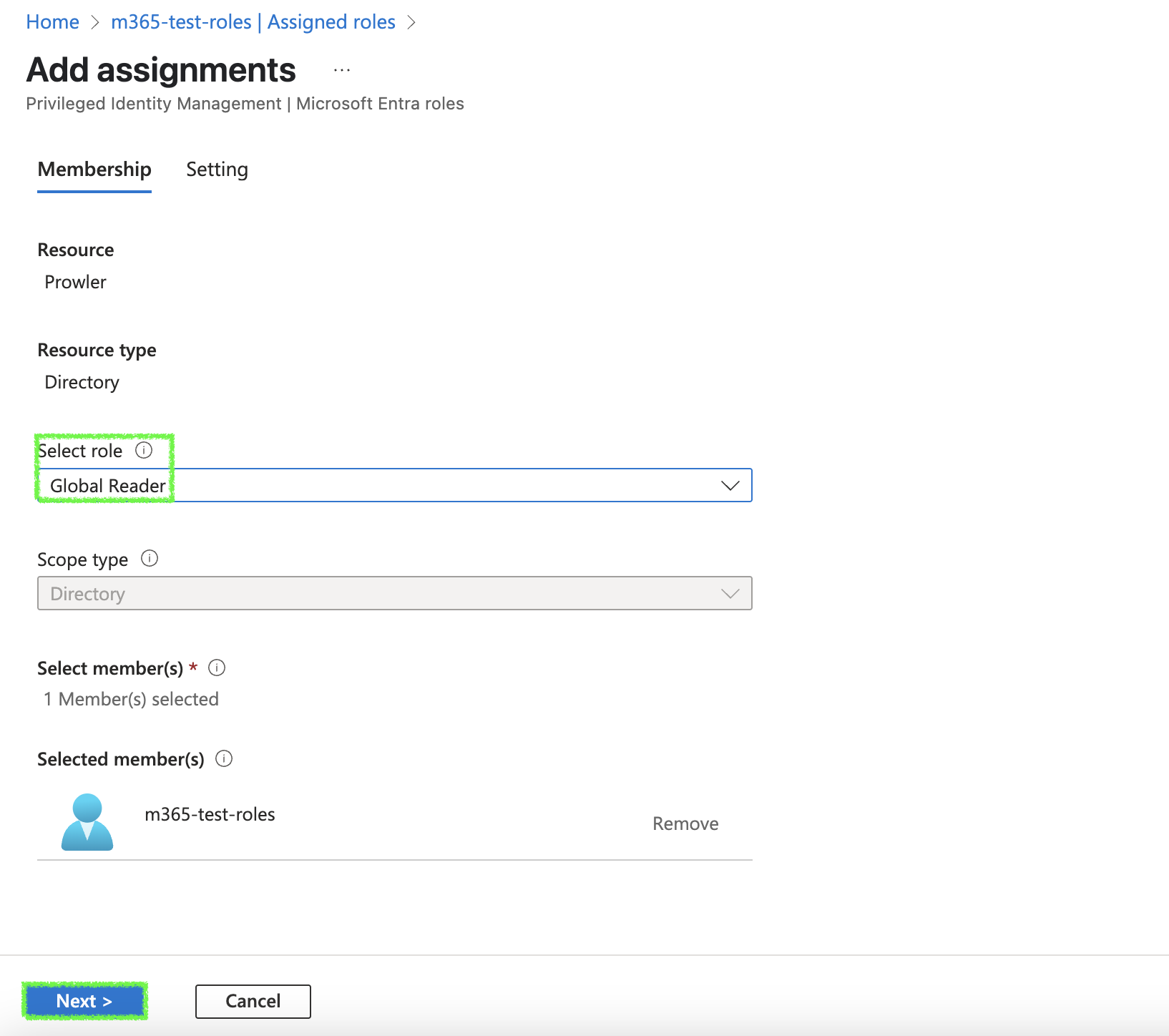
-
Click on next, then assign the role as
Active, and click onAssignto grant admin consent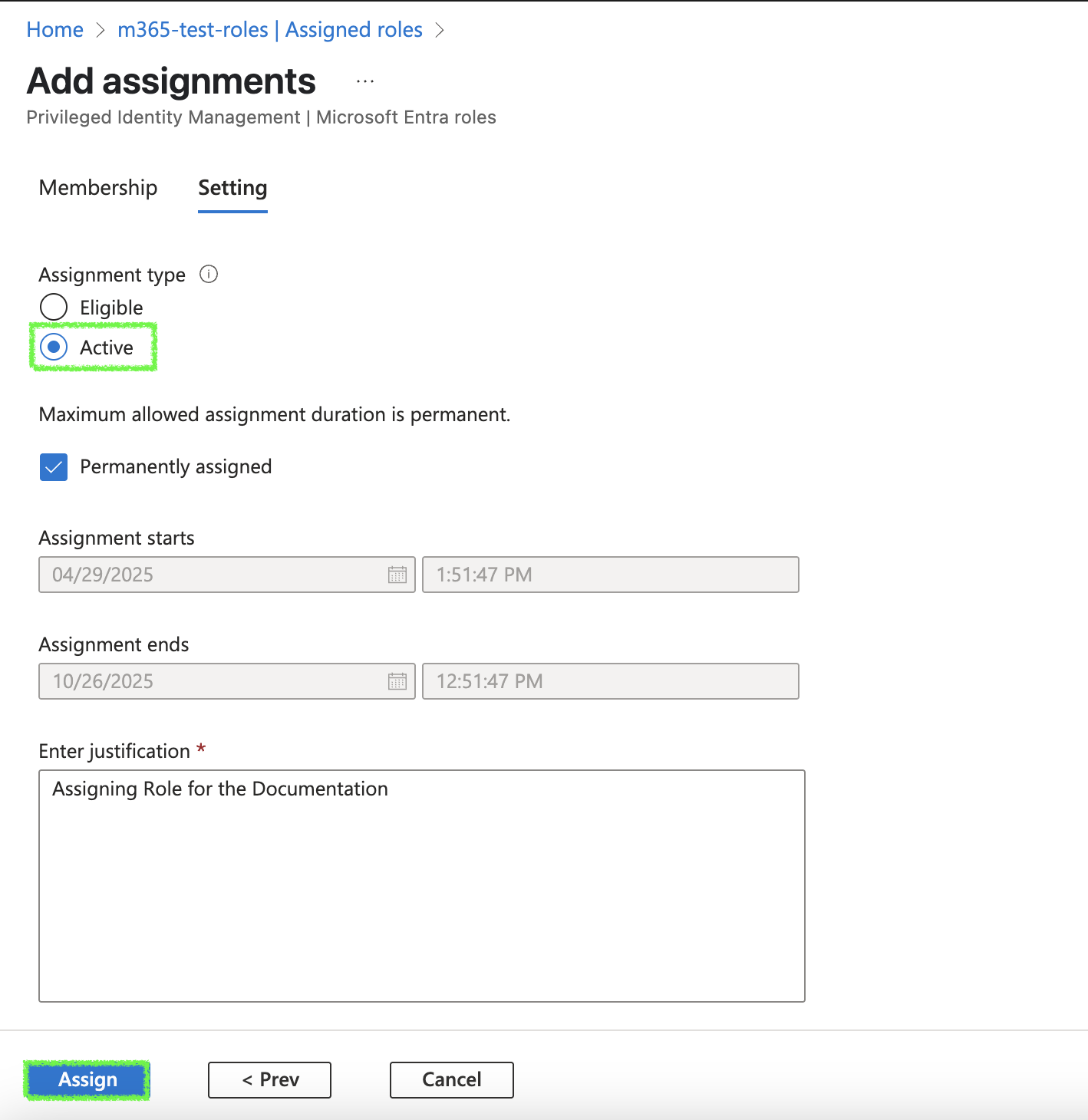
Step 4: Add credentials to Prowler Cloud/App¶
-
Go to your App Registration overview and copy the
Client IDandTenant ID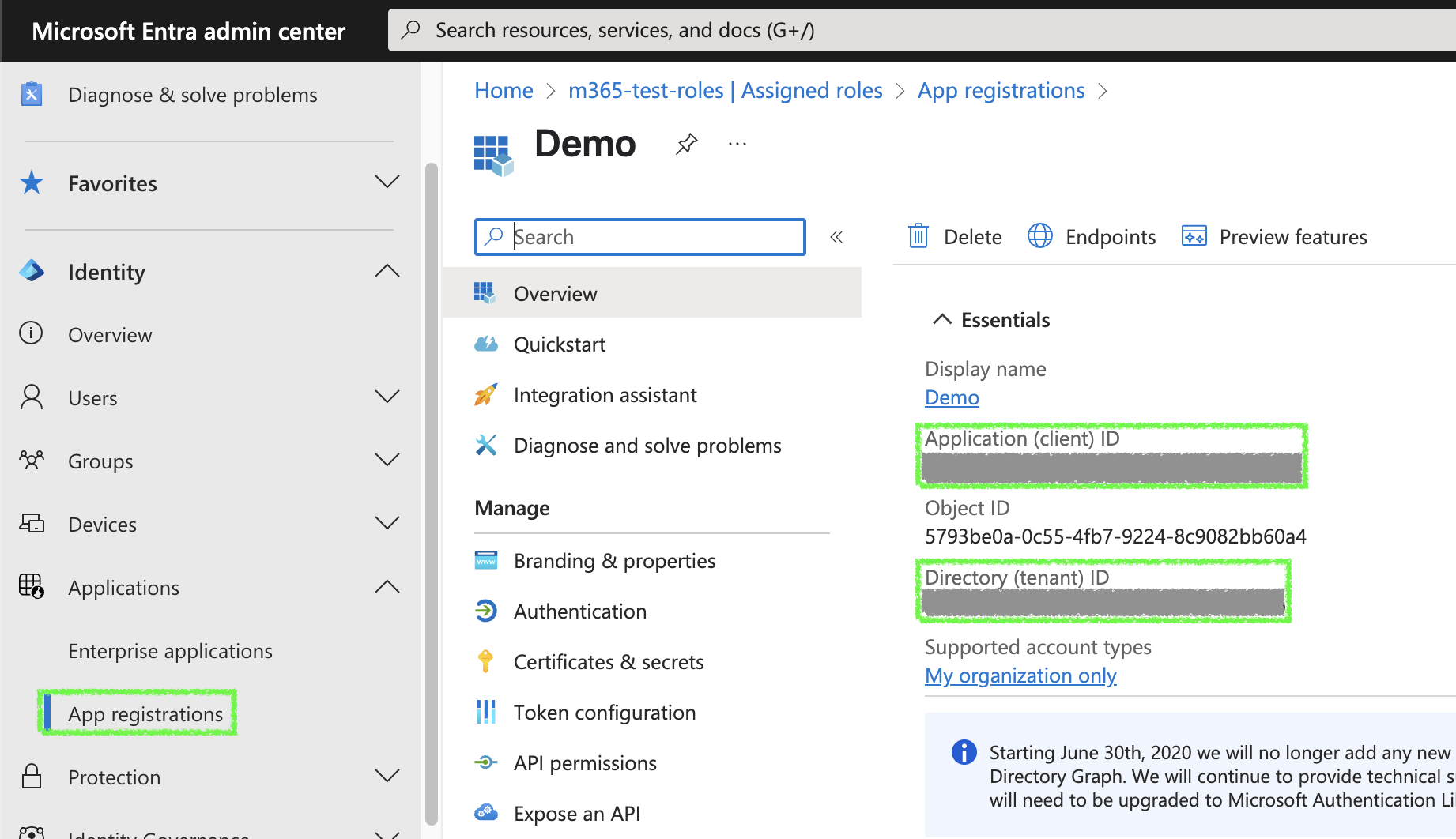
-
Go to Prowler Cloud/App and paste:
Client IDTenant IDAZURE_CLIENT_SECRETfrom earlierM365_USERthe user using the correct assigned domain, more info hereM365_PASSWORDthe password of the user
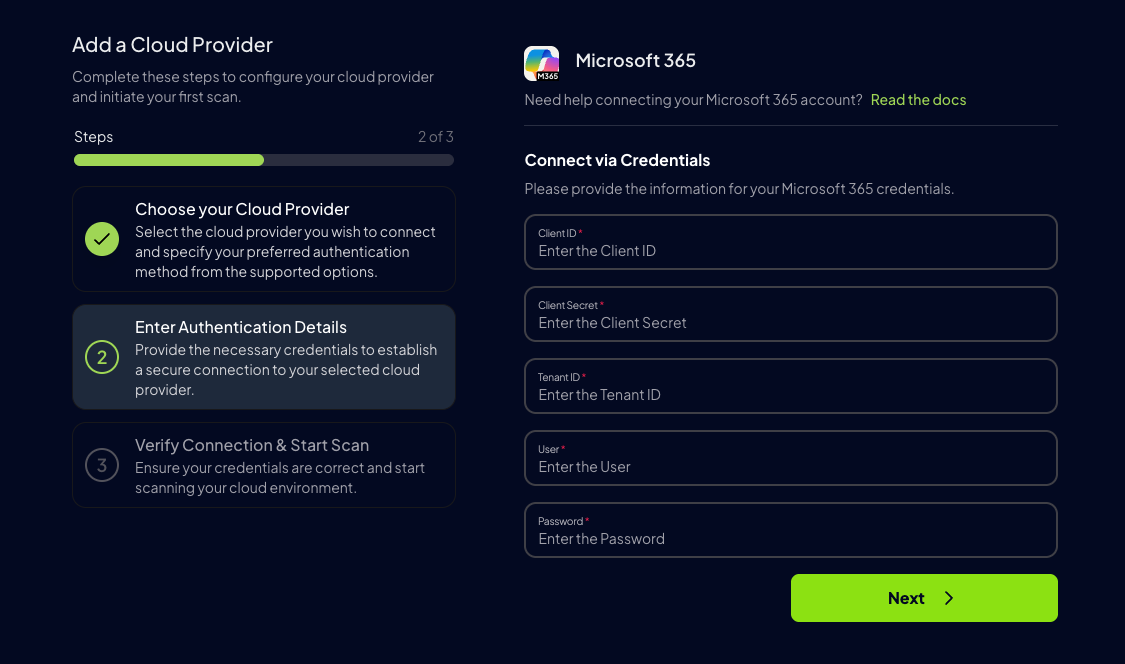
-
Click
Next
-
Click
Launch Scan